
Excerpt from AWS documentation:
Amazon Simple Storage Service (Amazon S3) is an object storage service offering industry-leading scalability, data availability, security, and performance. Customers of all sizes and industries can store and protect any amount of data for virtually any use case, such as data lakes, cloud-native applications, and mobile apps. With cost-effective storage classes and easy-to-use management features, you can optimize costs, organize data, and configure fine-tuned access controls to meet specific business, organizational, and compliance requirements.
While retrieving sensitive data from misconfigured AWS S3 buckets is an important first step, it’s not the only one. It’s possible, for example, to backdoor JavaScript files in an S3 bucket such that it affects everyone who uses the injected malicious code in their web application.
In this blog series, we are going to demonstrate the process of finding sensitive data and other secrets kept in misconfigured S3 buckets, which may then be used to exploit other linked apps. We will then delve into other attack vectors to see how vulnerable S3 buckets can be exploited to detect JavaScript files that are being loaded by web applications and then subsequently backdooring them to acquire user data.
In this Part 1 of the “Misconfigured Amazon S3 Buckets”, we are going to first create a vulnerable S3 bucket and demonstrate the process of finding sensitive data and other secrets kept in misconfigured S3 buckets.
To begin with, we are going to first create a vulnerable S3 bucket. For this, log in to the AWS console and navigate to the Amazon S3 service. Then create a new bucket by navigating to “Create Bucket”. Give a unique name to the S3 bucket. For instance – “redfox-production”.
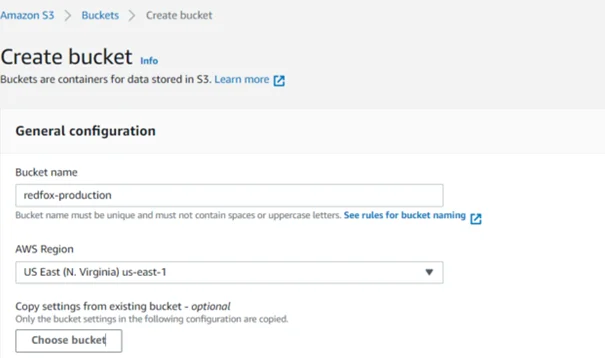
Next, we’ll disable the “Block all public access” setting. Note that this setting is enabled by default. This effectively disables the following settings:
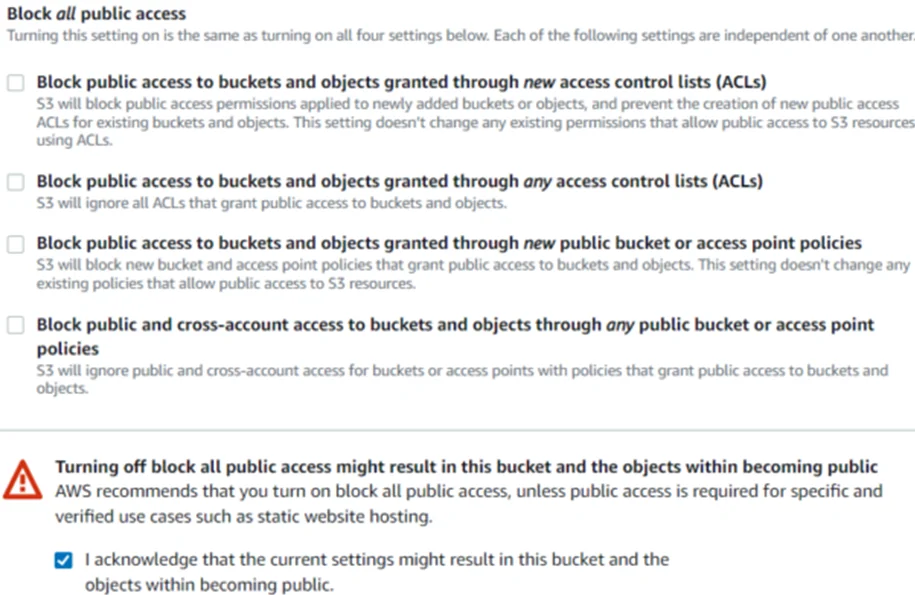
Next click on “Create bucket”. This will create our new S3 bucket, namely, “redfox-production”.
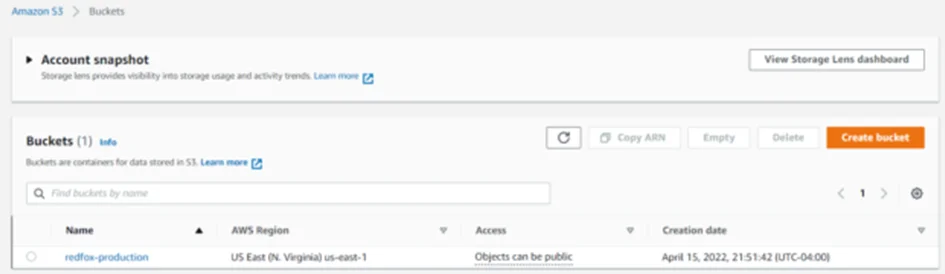
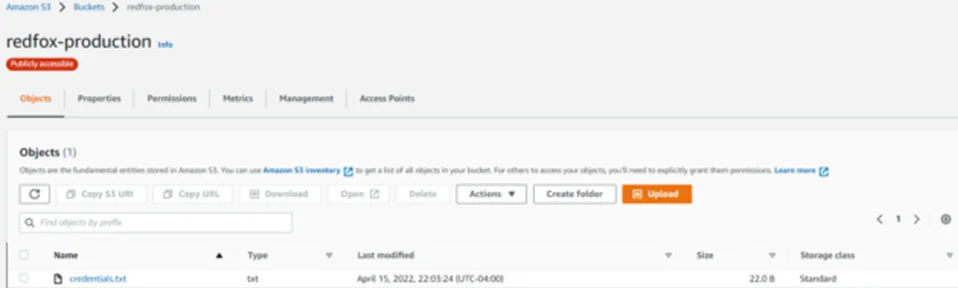
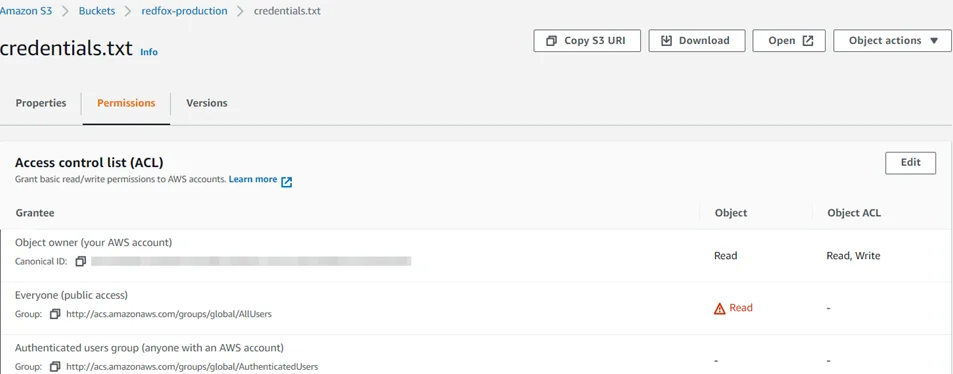
Note that the access level is set to “Objects can be public”. This effectively means that the bucket is not public but anyone with appropriate permissions can grant public access to objects. For demonstration, we’ll create a sample file “credentials.txt” and upload it to our vulnerable S3 bucket.
One final setting that we need to apply is to change the “Edit Object Ownership” settings from “ACLs Disabled” to “ACLs Enabled”.
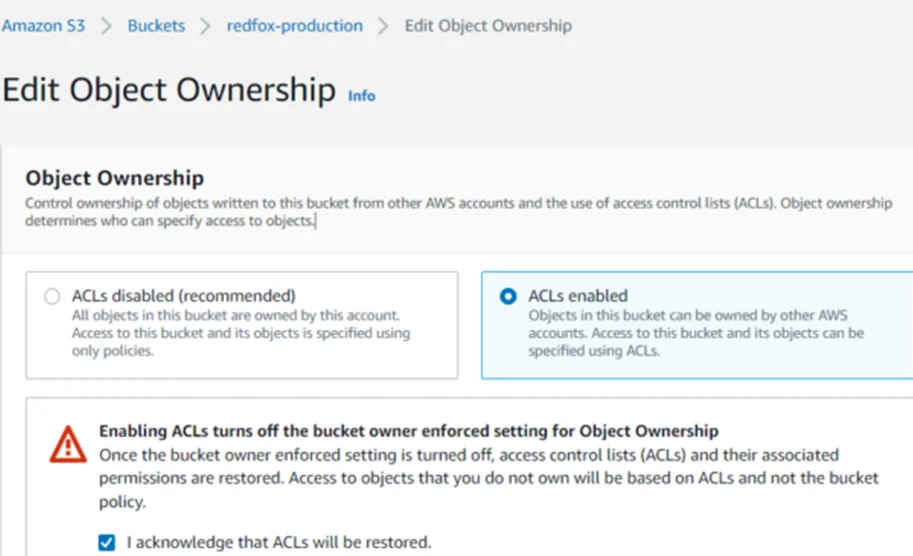
Once that’s done, we’ll give “Read” permissions to “Everyone” at the Object level.
Controlling access to S3 resources may be done in three ways:
We’ll talk about this in a future blog post. But for now, this following diagram should explain what we need for this blog post:
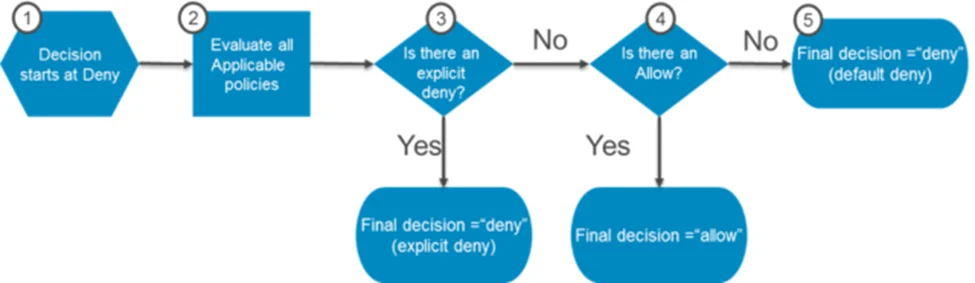
Note: In accordance with the principle of least-privilege, decisions default to DENY and an explicit DENY always trumps an ALLOW. For example, if an IAM policy grants access to an object, the S3 bucket policies denies access to that object, and there is no S3 ACL, then access will be denied. Similarly, if no method specifies an ALLOW, then the request will be denied by default. Only if no method specifies a DENY and one or more methods specify an ALLOW will the request be allowed.
For this exercise, we’ll use the AWSBucketDump tool to search for S3 buckets. This tool to quickly enumerates AWS S3 buckets to look for sensitive information. It’s similar to a subdomain brute-forcer but is made specifically for S3 buckets and also has some extra features that allow for grepping for files as well as for downloading interesting files.
Next, we’ll configure the tool as per the instructions in the GitHub repository.
AWSBucketDump comes with a couple of sample files –
Once installed, make the following changes:
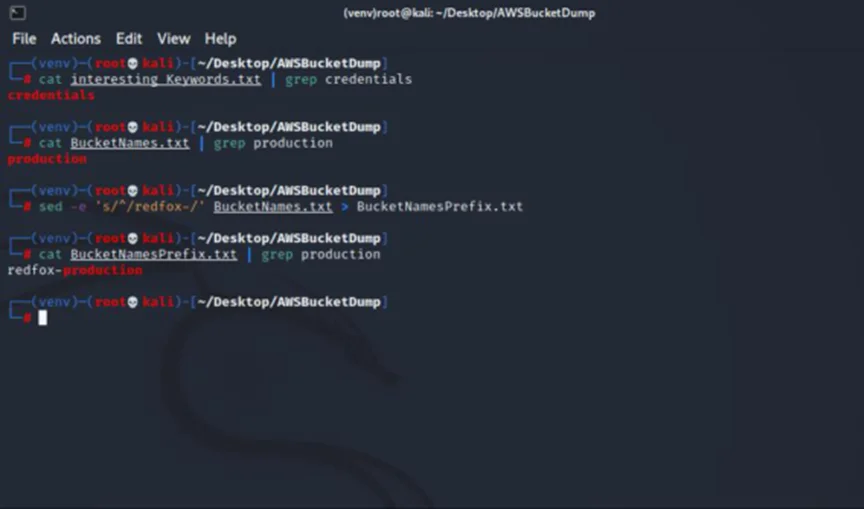
We can now run the AWSBucketDump tool to search for our misconfigured S3 bucket and download the credentials file. For this, we’ll run the following command:
# python3 AWSBucketDump.py -D -l BucketNamesPrefix.txt -g interesting_Keywords.txt
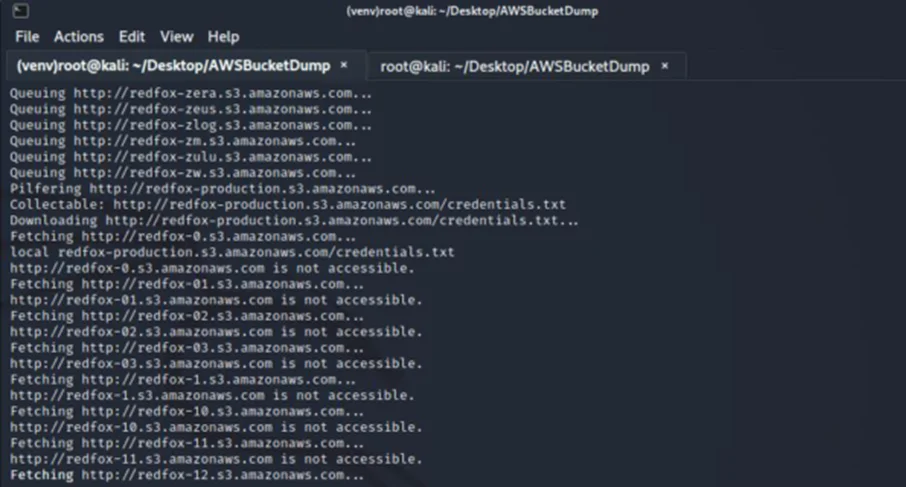
AWSBucketDump creates a folder “redfox-production.s3.amazonaws.com” with our credentials file:
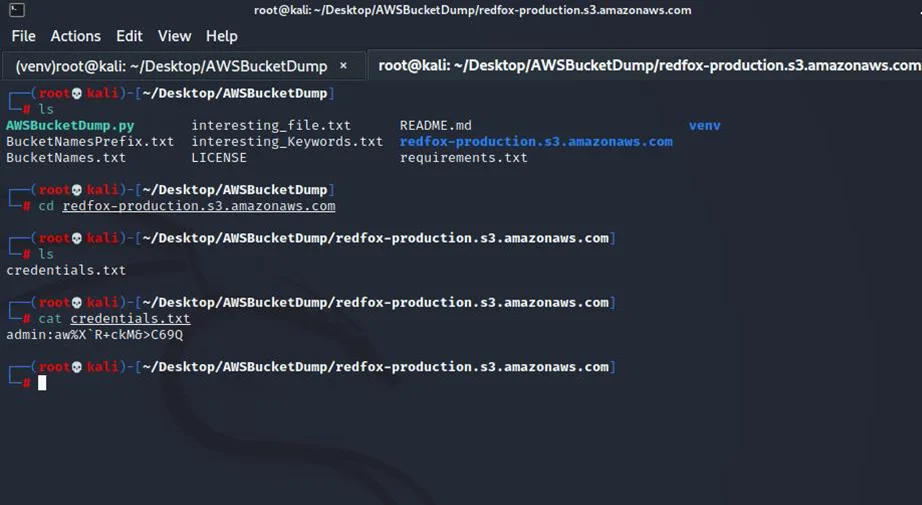
In conclusion, we went through the AWSBucketDump tool and discussed how it can be used to dump data from misconfigured Amazon S3 buckets. In Part 2 of the “Misconfigured Amazon S3 Buckets” series, we will see how vulnerable S3 buckets can be exploited to detect JavaScript files that are being loaded by web applications, and then subsequently backdoor them to acquire user data.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.