
HTTP Parameter Pollution (HPP) is a cunning technique employed by attackers to manipulate or retrieve hidden information by injecting encoded query string delimiters into existing parameters of web applications. This vulnerability arises when user input is not adequately encoded for output by the web application. HPP can impact both GET and POST requests, making it a versatile attack vector. It can be exploited in various scenarios, such as password changes, two-factor authentication (2FA), comment sections, profile photo uploads, and even when passing API keys or one-time passwords (OTPs) as parameters.
HTTP parameters play a crucial role in facilitating communication between clients and servers. They allow clients to customize their requests by providing additional information, such as user-input data, to the server. HTTP parameters can be included in GET, POST, PUT, PATCH, and DELETE requests, depending on the nature of the interaction.
Let’s explore the different types of HTTP parameters:
GET requests are used to retrieve information from a server by specifying a URL. The parameters in a GET request are appended to the URL, following a question mark? Each parameter is a key-value pair separated by an equal sign =. Multiple parameters are separated by an ampersand &.
For example, consider a GET request to retrieve details about a specific book from an online bookstore:
http://bookstore.com/books?title=ToKillAMockingbird&author=HarperLee
In this example, http://bookstore.com/books is the URL, and the parameters are title=ToKillAMockingbird and author=HarperLee. The server will process this request and retrieve information about the book titled “To Kill a Mockingbird” by Harper Lee.
POST requests are used to send data to a server for creating or updating a resource. Unlike GET requests, POST parameters are not included in the URL but are sent in the body of the HTTP request. This is particularly useful for sending large amounts of data, including files, or when data needs to be secure, such as user passwords.
An example of a POST request would be creating a new user in a system. Let’s say we want to add a new user to our online bookstore’s system with the username BookLover101 and password Secret Password. The POST request might look like this:
POST /users HTTP/1.1 Host: bookstore.com Content-Type: application/x-www-form-URL encoded Content-Length: length username=BookLover101&password=Secret Password
In this example, the request informs the server that it is a POST request to the /user URL. The Content-Type header indicates that the request body contains form data. The Content-Length header specifies the length of the body data. The body of the request contains the POST parameters username and password along with their respective values.
PUT and PATCH requests are like POST requests in that they send data in the request’s body. However, these methods are typically used for updating existing resources. A PUT request replaces the entire resource with the provided data, while a PATCH request modifies only specific parts of the resource.
DELETE requests are used to remove a specific resource identified by its URL. These requests typically do not require any parameters in the body of the request and rely on the URL to specify the resource to be deleted.
HTTP Parameter Pollution leverages the ambiguity in how web servers and applications process requests with duplicate parameter names. By sending a manipulated HTTP request with duplicated parameter names, each containing a portion of malicious code, an attacker can exploit the server’s configuration and application framework to achieve their objectives.
The behaviour of servers in handling duplicate parameters can vary, which provides attackers with an opportunity to hide malicious code within seemingly harmless parameters. Some servers concatenate the values of parameters with the same name, reassembling the malicious code on the server side. Other servers might only consider the first or last instance of a duplicated parameter, potentially allowing attackers to conceal their malicious intent behind benign parameter values.
This ability to split and conceal malicious code within seemingly innocuous parameters makes HPP a stealthy technique that can bypass traditional security mechanisms like WAFs and intrusion detection systems that rely on identifying known malicious patterns. Through HPP, attackers can manipulate the behaviour of the targeted web application, potentially leading to unauthorized data access, information disclosure, or even remote code execution.
Example 1
To better understand how HTTP Parameter Pollution works in practice, let’s consider an example involving a web application that uses a parameter to redirect users to a specified URL. A valid request URL might look like this:
http://example.com/home?redirectURL=internalPage
In this example, the redirectURL parameter is intended to contain the URL of an internal page where the user will be redirected. However, an attacker can exploit HPP by sending a polluted request, including the parameter twice:
http://example.com/home?redirectURL=internalPage&redirectURL=http://malicious.com
The server’s handling of the repeated redirectURL parameter can lead to unintended consequences due to HPP. Some servers concatenate the parameter values, potentially opening a loophole where the user may be redirected to the malicious external website instead of the intended internal page. This manipulation of the request allows the attacker to bypass security mechanisms, illustrating the potential impact of HPP.
Example 2
Let’s imagine a situation where a malicious attacker attempts a security breach to gain access to user data. However, the website’s access controls are set up to permit only administrator users to view this data.
1) Begin by entering the username as “john” and then click the “Search” button.
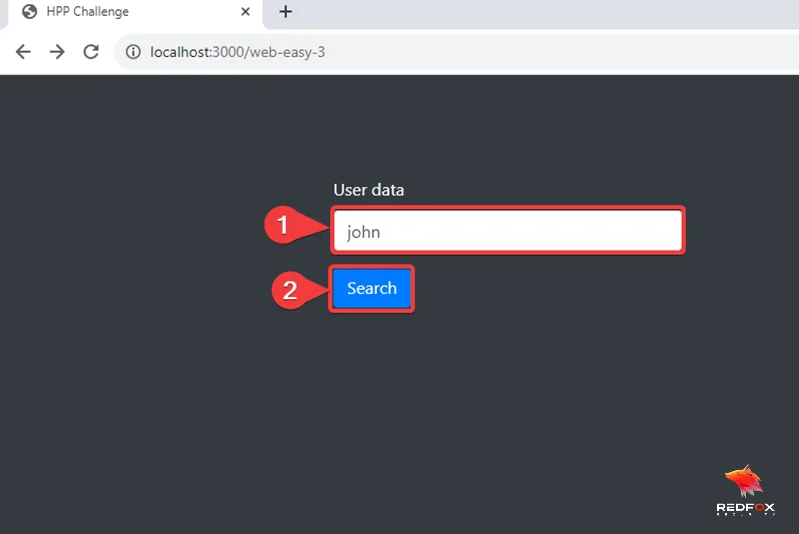
2) Note that the website enforces strict access controls, allowing only administrator users to access the user data.
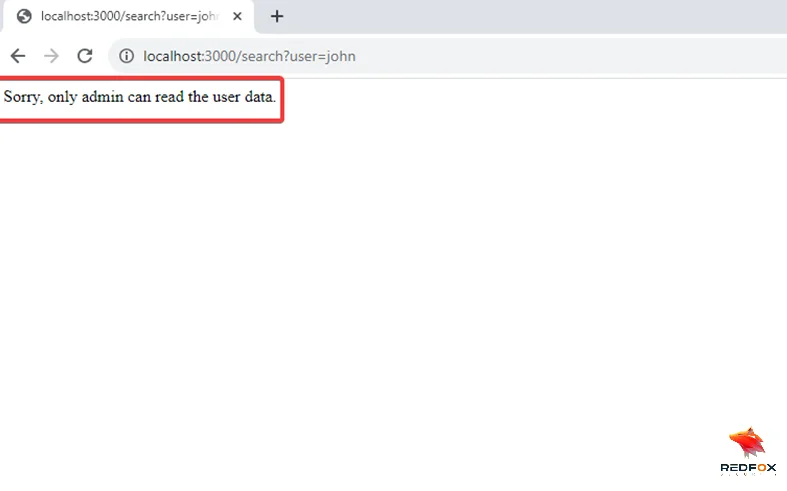
3) Next, shift your focus to the URL endpoint. As a diligent penetration tester, you may consider modifying the username from “john” to “admin” to assess whether the web application allows access to user data.
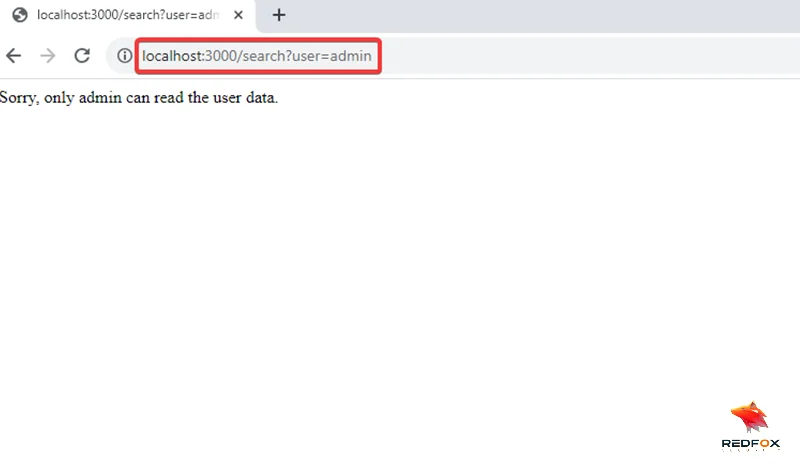
4) Keep in mind that even after altering the username to “admin,” the web application maintains its robust security measures, denying access to user data.
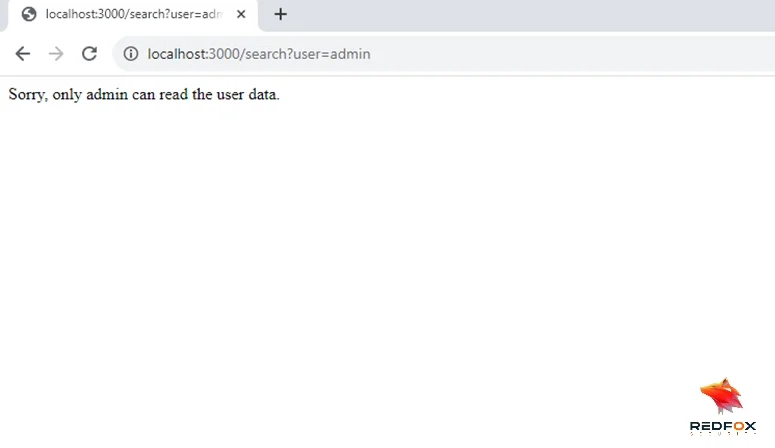
5) As part of your investigation, append “&user=john” to the URL and press “Enter”.
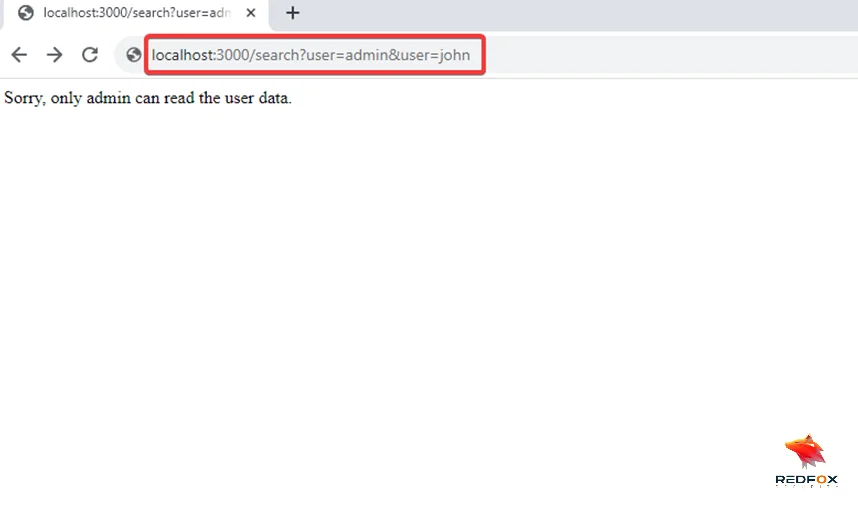
6) Now, you can see that we have successfully bypassed the restriction to view user data.
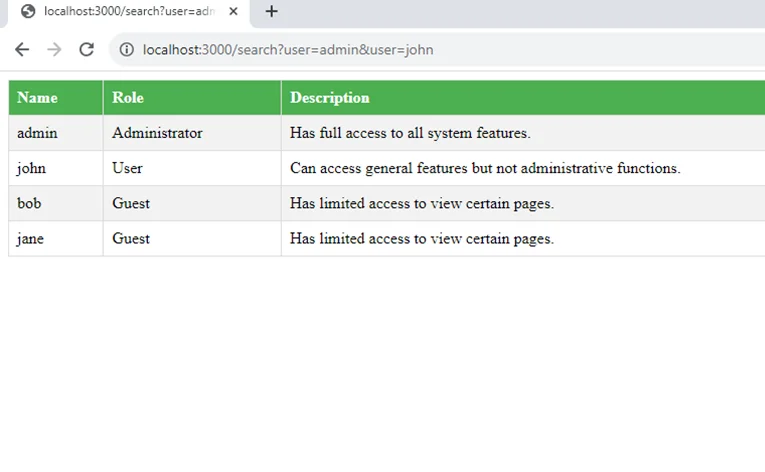
When both “john” and “admin” were included as parameters in the URL, the website’s request processing logic might have prioritized one over the other, or it might have interpreted them differently. This resulted in a situation where the website allowed access, as the request might have been interpreted as a legitimate request from the user “john.”
However, when only “admin” was the username in the URL, the request processing logic recognized it as an attempt to access user data as an administrator. Since the user making the request was not an administrator, the access control mechanism correctly denied access.
The vulnerability in this case is the website’s inability to correctly handle multiple conflicting or ambiguous parameters, which allowed the security mechanism to be bypassed through parameter manipulation, leading to potential unauthorized access. This highlights the importance of proper request handling and parameter validation in web application security to prevent HTTP parameter pollution vulnerabilities.
Mitigating HTTP Parameter Pollution attacks involves implementing proper input validation, awareness of web technology, and employing updated security mechanisms. By following these strategies, web application developers can reduce the risk of falling victim to HPP attacks. Here are some mitigation techniques to consider:
Ensure that your web application only accepts the expected parameters. Any unrecognized parameters should be treated as anomalies, resulting in an error or the request being ignored. By strictly defining the parameters that your application handles, you can minimize the risk of unexpected behaviour caused by HPP.
Implement rigorous validation checks for all input parameters. Validate the type, format, and range of each parameter to ensure that they meet the expected criteria. For example, if a parameter is expected to be a number, reject any non-numeric input. By enforcing strict parameter validation, you can prevent HPP attacks that exploit the mishandling of parameter values.
Design your application to accept only the first occurrence of a parameter with the same name. Any subsequent occurrences should be ignored. This approach can prevent attackers from leveraging the same parameter multiple times to execute HPP attacks. By treating only the first instance of a parameter as valid, you can mitigate the risk of malicious parameter pollution.
Implement a robust input sanitization routine to remove potentially harmful strings from user input. By filtering out malicious characters or patterns, you can strengthen the security of your web application and minimize the risk of HPP attacks. Regular expression matching, input encoding, and HTML sanitization are some common techniques for input sanitization.
Consider implementing security headers, such as Content Security Policy (CSP), to mitigate the risk of code injection attacks, including HPP. Security headers provide an additional layer of protection by defining the expected behaviour of web browsers and preventing the execution of unauthorized scripts or codes. By configuring appropriate security headers, you can enhance the security posture of your web application.
Regularly update your web application firewall (WAF), intrusion detection systems, and other security defences to ensure they are equipped with the latest threat intelligence. Keeping your security mechanisms up to date is crucial for detecting and blocking new forms of attacks, including emerging HPP techniques. By staying proactive with security updates, you can defend against evolving threats more effectively.
Perform regular code reviews to identify and patch potential vulnerabilities before they can be exploited. Code reviews help ensure that best practices and secure coding techniques are followed throughout the development process. By conducting thorough code reviews, you can identify and address any weaknesses or potential entry points for HPP attacks.
Imperva Web Application Firewall (WAF) is an effective solution for mitigating HTTP Parameter Pollution attacks. It provides near-zero false positives, ensuring that legitimate traffic is not blocked while protecting against malicious attacks. With a global Security Operations Center (SOC), Imperva offers real-time protection against the latest threats, ensuring your organization is safeguarded within minutes of new vulnerabilities being discovered.
By applying HTTP protocol validation rules, Imperva WAF can prevent protocol exploits like buffer overflow, malicious encoding, HTTP smuggling, and illegal server operations. The default policy provided by Imperva enables strict adherence to RFC standards while allowing minor variations for specific applications. This fine-tuned approach ensures optimal security without hindering the functionality of your web application.
Imperva WAF forms a critical component of a comprehensive Web Application and API Protection (WAAP) stack. By securing your entire application stack, from the edge to the database, Imperva ensures that the traffic you receive is only the traffic you want. With advanced analytics that goes beyond OWASP Top 10 coverage, Imperva reduces the risks associated with third-party code and provides PCI-compliant, automated security for your web applications.
In conclusion, HTTP Parameter Pollution is a web application vulnerability that attackers exploit to manipulate or retrieve hidden information. By understanding the techniques employed by attackers, implementing proper input validation, and utilizing advanced security mechanisms like Imperva WAF, organizations can effectively protect their web applications from HPP attacks. Stay proactive, stay updated, and prioritize security to safeguard your valuable data and ensure the integrity of your web applications.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.