
Drones are no longer just hobby gadgets—they’ve become critical assets across industries like agriculture, surveillance, defense, and logistics. The Nabhyaan Drone, with its advanced design and robust performance, is one such tool. But as with any connected technology, drones also bring along unique security risks.
This guide will walk you through understanding the Nabhyaan Drone, identifying its vulnerabilities, and applying security best practices to keep it safe from threats.

Advanced Navigation System: GPS + GLONASS for precise positioning.
High-Resolution Camera: Options from 720p to 1080p with gimbal stabilization.
Extended Flight Time: High-capacity batteries for up to 30 minutes per charge.
Durable Design: Built to withstand harsh environments.



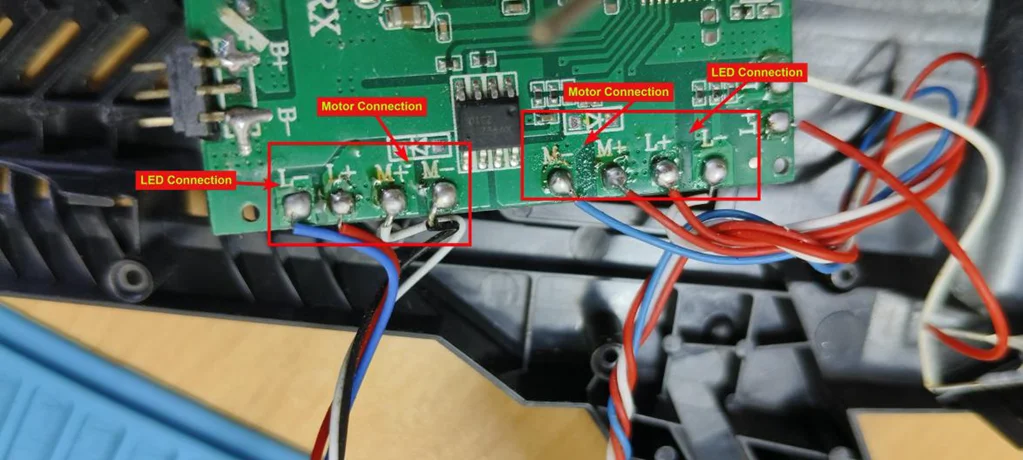
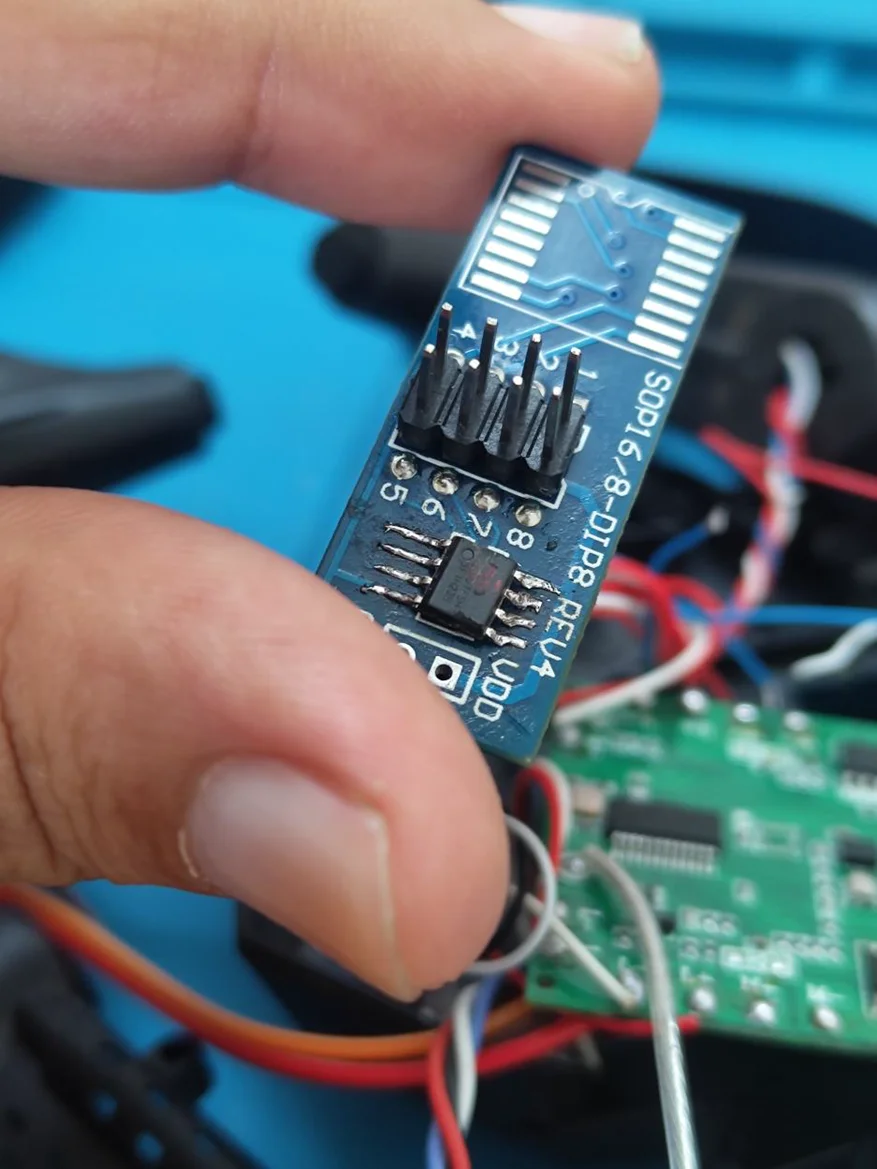
Wi-Fi Module PCB: Contains the Wi-Fi module and flash chip.
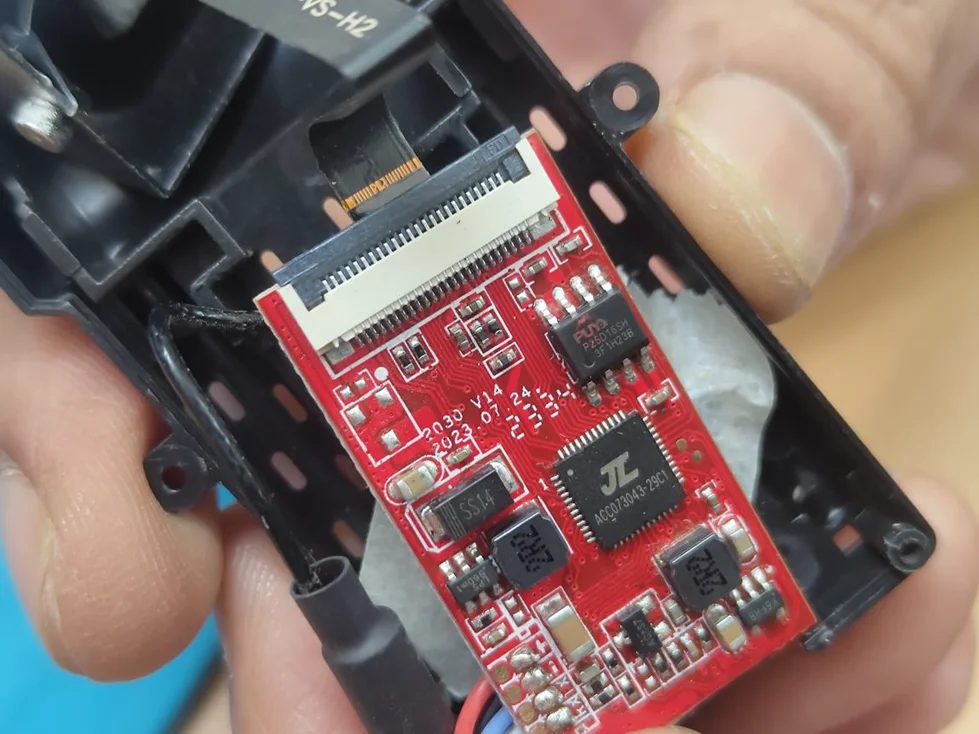
MCUs: Core processors for flight operations.
Sensors: GPS, IMU, barometric sensors for stability and navigation.
Communication Modules: Wireless connectivity for control & telemetry.
Camera System: High-resolution optics with stabilization.
Power System: Efficient, high-capacity batteries.
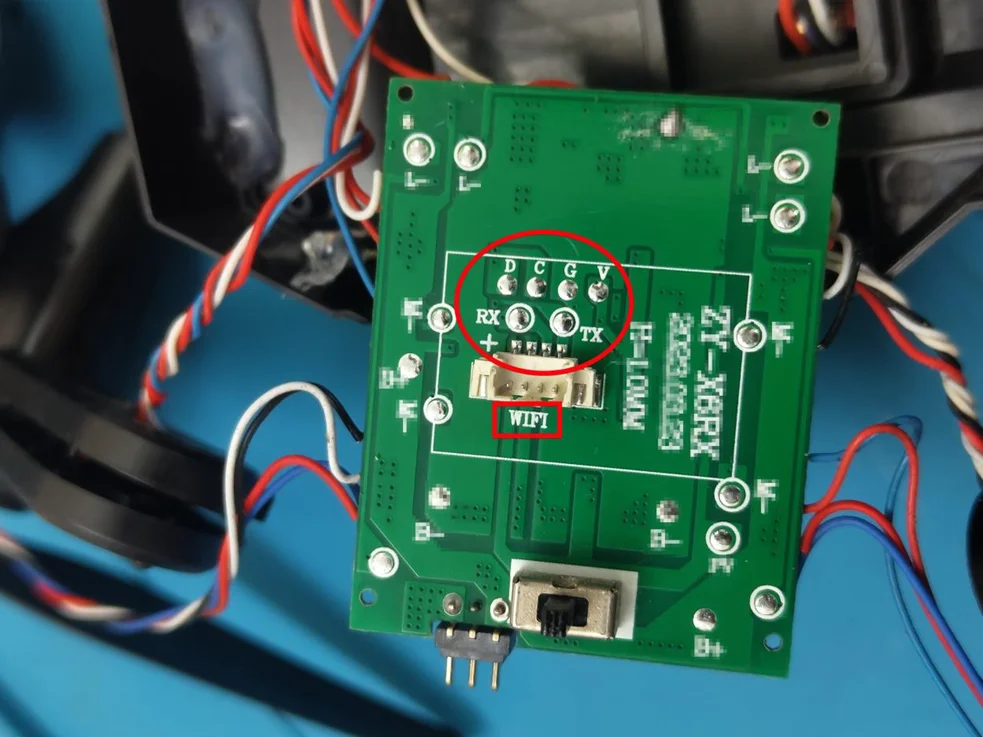
Debugging Interfaces: RX, TX, and GND pins (often locked).
Flight Control Software – Handles navigation and inputs.
Communication Protocols – Secure data exchange between drone and controller.
Data Management Software – Collects and transmits sensor/camera data.
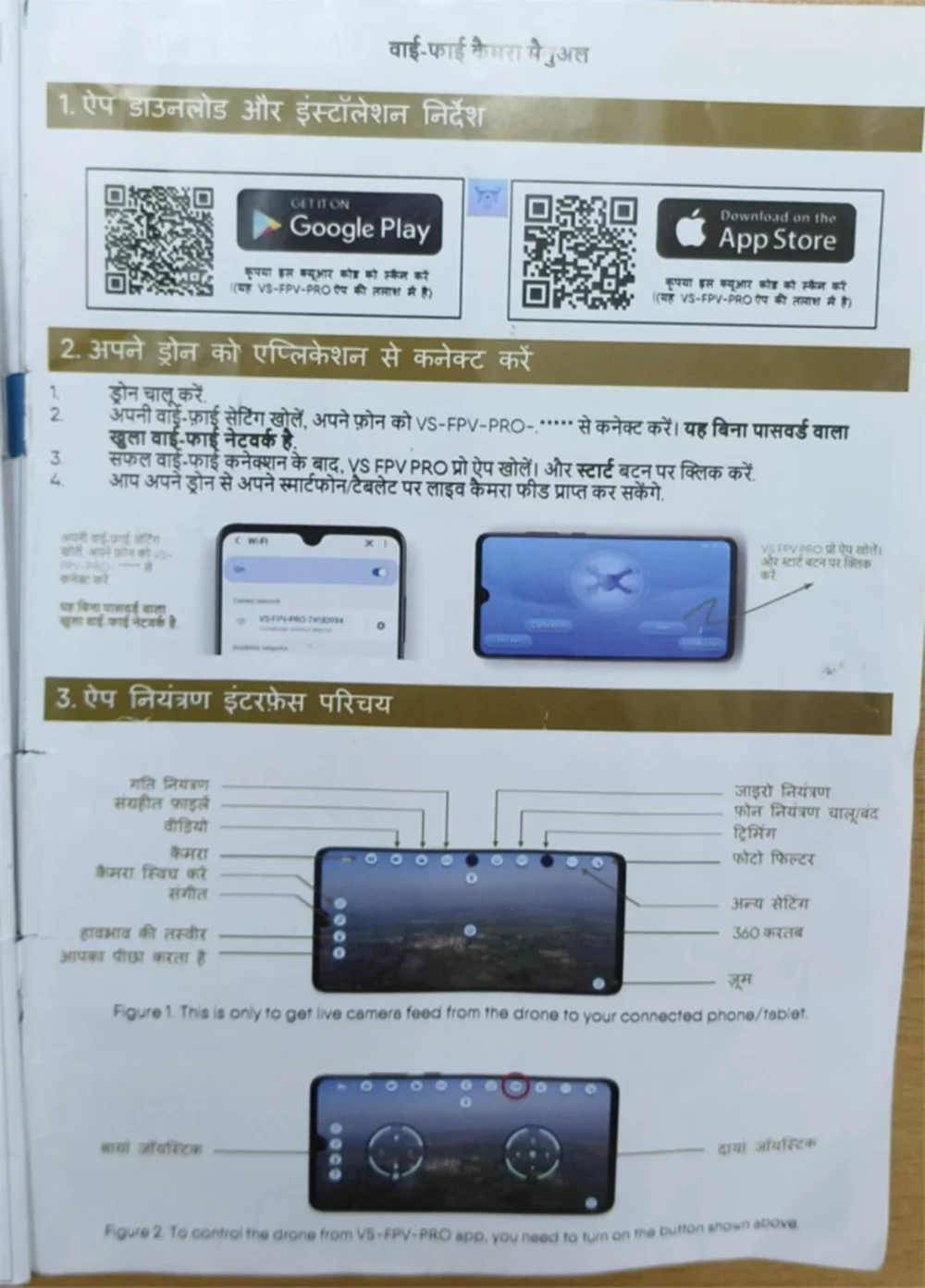
Potential entry points for attackers include:
Wireless Communication – Intercepted if unencrypted.
Physical Access – Tampering, data theft, or malware installation.
GPS Spoofing – Feeding false navigation data.
Wi-Fi Hotspot Attacks – Fake hotspots tricking the drone.
Firmware – Outdated versions leave open doors.
Mobile Apps – Flaws in companion apps exploited.
DoS Attacks – Flooding systems with requests to crash operations.

Intercepted Communication → Use strong encryption.
Firmware Exploits → Keep firmware updated.
GPS Spoofing → Implement anti-spoofing checks.
Physical Tampering → Secure storage and access controls.
Reconnaissance – Gather drone model, firmware, communication methods.
Enumeration – Scan for open ports, services, and weak points.
Discovery – Analyze firmware/software for weak credentials.
Exploitation – Target flaws in firmware, comms, or authentication.
Unencrypted Links → Apply encryption + authentication.
Weak Authentication → Strengthen login security.
Malware Risks → Use antivirus + regular scans.
Physical Security → Restrict access to ground stations.
Phishing Attacks → Train operators to detect scams.
Wireshark – Network packet analysis.
Dronesploit – Drone security testing framework.
Dronextract – Forensic tool (DJI drones).
Burp Suite – Communication analysis.
Apktool / MobSF – Reverse engineering drone apps.
HackRF One & GNU Radio – SDR tools for communication analysis.
Nmap – Network scanning.
Ghidra & Binwalk – Firmware reverse engineering.
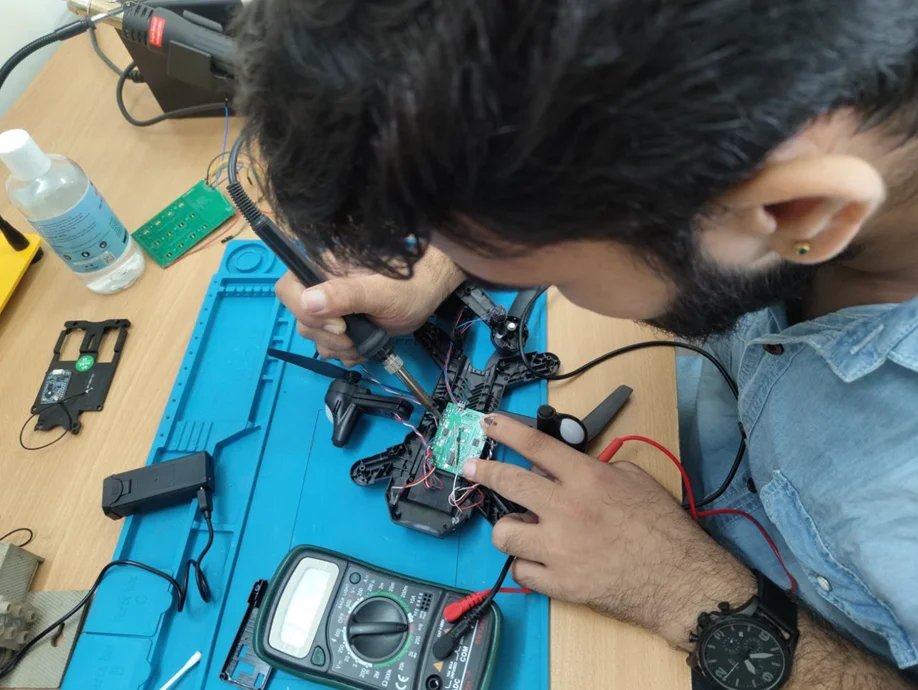
RX, TX, GND Pins – Usually locked but critical for debugging.
Flash IC Chip Removal – For advanced firmware analysis.
Firmware Encryption – Protects against unauthorized modification.
Use strong encryption & secure protocols.
Keep firmware & apps updated.
Enable secure boot to block rogue firmware.
Enforce multi-factor authentication.
Apply firewalls & antivirus at ground stations.
Disable unnecessary services to reduce attack surface.
Avoid public Wi-Fi connections.
Implement physical security controls.
Deploy drone detection technology (radar, acoustic, Drone ID).
The Nabhyaan Drone is a powerful UAV platform, but like all connected devices, it comes with risks. By following best practices—encryption, firmware updates, secure communication, strong authentication, and operator awareness—you can maximize its potential while minimizing threats.
At Redfox Security, we help organizations strengthen their UAV and IoT security posture. If you’d like expert assistance in identifying vulnerabilities and safeguarding your assets, contact us today.
Want to gain hands-on expertise? Explore our comprehensive cybersecurity courses at Redfox Academy