
In the vast landscape of the internet, a hidden world of devices is waiting to be discovered. These devices, ranging from servers and routers to webcams and printers, are often accessible to anyone with the right tools and knowledge. This is where Shodan comes into play – a powerful search engine that uncovers these internet-accessible devices, providing a wealth of information and passive reconnaissance opportunities.
Shodan has been described as a search engine for hackers, but its true potential lies in its ability to assist security professionals and researchers in identifying vulnerable systems and potential attack vectors. It is a valuable resource for passive reconnaissance, enabling users to gather crucial information about internet-connected devices.
Devices that Shodan can find
Shodan’s capabilities span a wide range of internet-accessible devices. Here are just a few examples:
With Shodan, the possibilities are vast and varied. It’s a treasure trove of information waiting to be explored.
Port: Search by a specific port number.
Net: Search based on an IP or CIDR range.
Hostname: Locate devices by their hostname.
OS: Search by the operating system running on the device.
City: Locate devices by city.
Country: Locate devices by country.
Geo: Locate devices by coordinates.
Org: Search by organization.
Before/After: Delimit search results by timeframe.
Hash: Search based on banner hash.
Has_screenshot:true: Filter search results based on the presence of a screenshot.
Title: Search on the basis of text within the title.
These filters help narrow down your search and provide more targeted results.
Now that you know how to use the search filters, let’s explore some examples of how you can search for specific devices or information using Shodan.
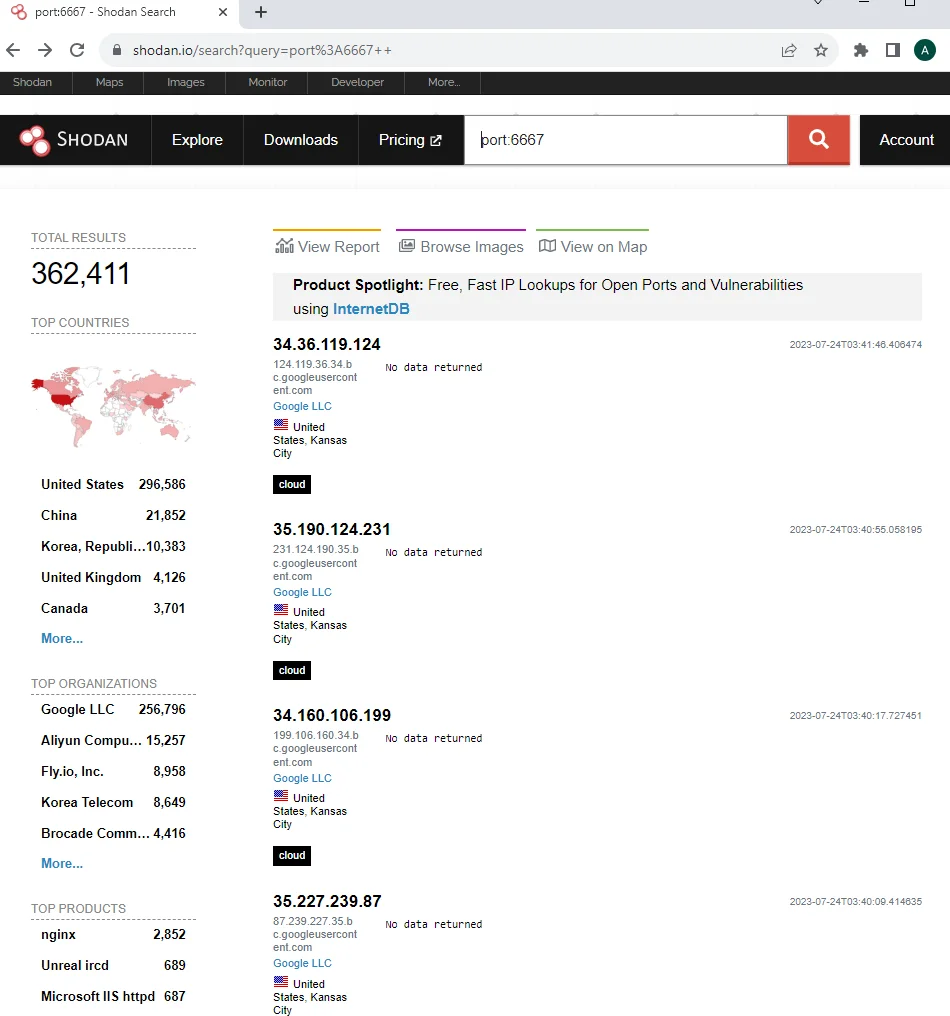
Example 1: Find devices that run a specific port
To search for devices running on a specific port, simply enter the port number in the search bar. For example, to find devices running on port 6667, you would enter:
port:6667
Example 2: Look for devices with a specific OS and port
If you’re interested in finding devices with a specific operating system and port, you can combine the “os” and “port” filters. For instance, to find devices running Windows 2003 on port 445, you would enter:
os:windows 2003 port:445
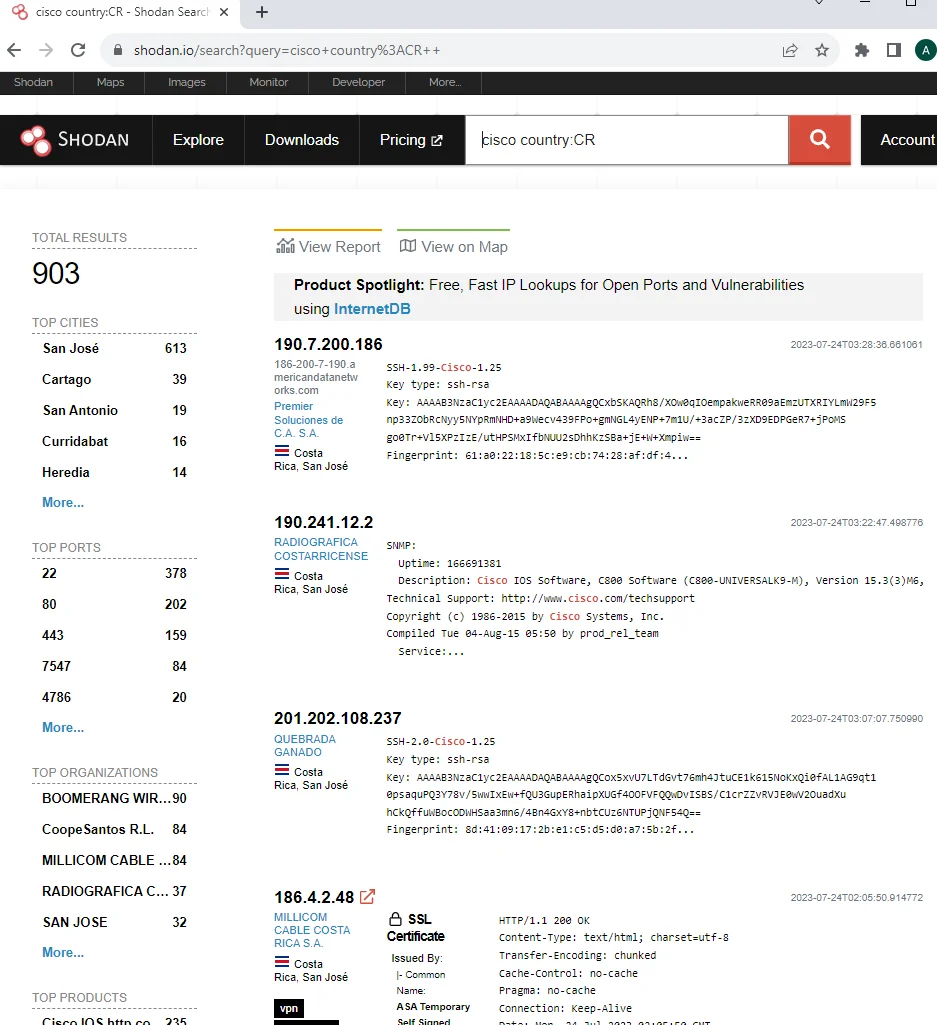
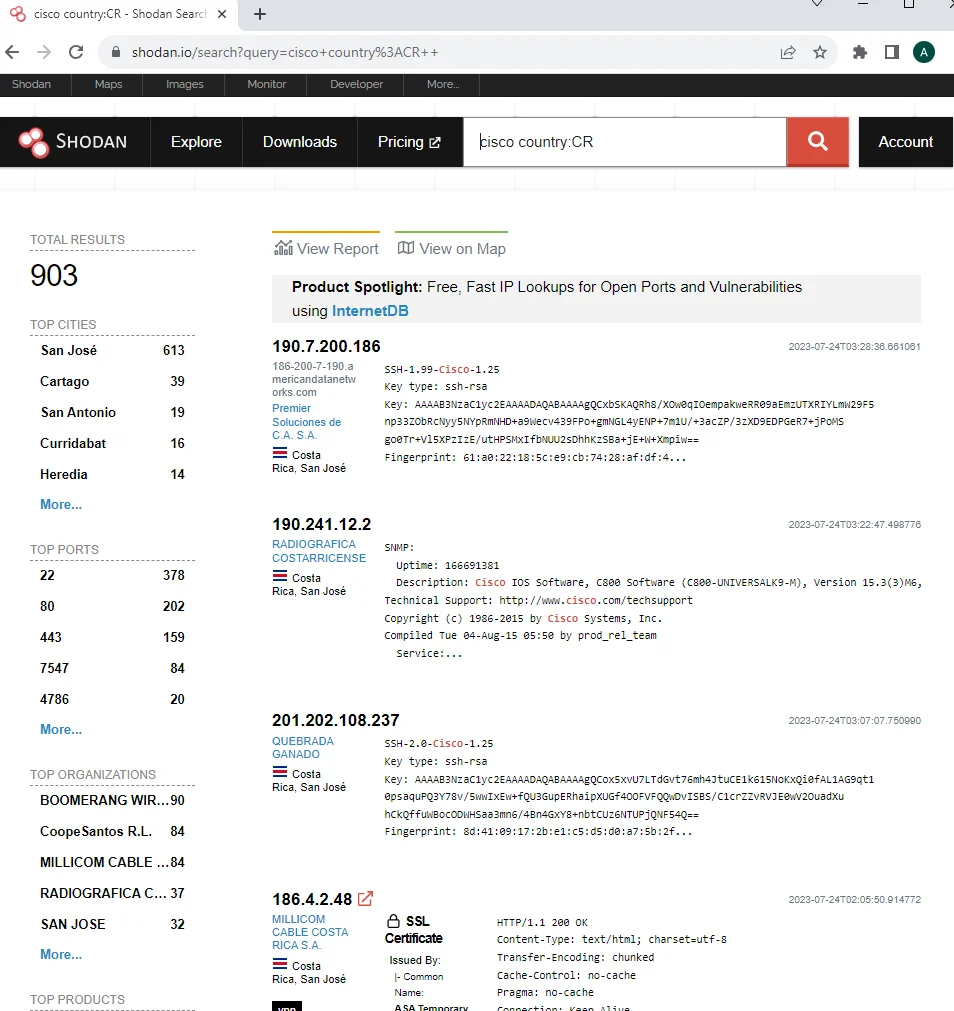
Example 3: Search for devices by country and keyword
To locate devices in a specific country and with a specific keyword, you can use the “country” and “keyword” filters. For example, to find Cisco devices in Costa Rica, you would enter:
cisco country:CR
Example 4: Search by company, OS type, and location
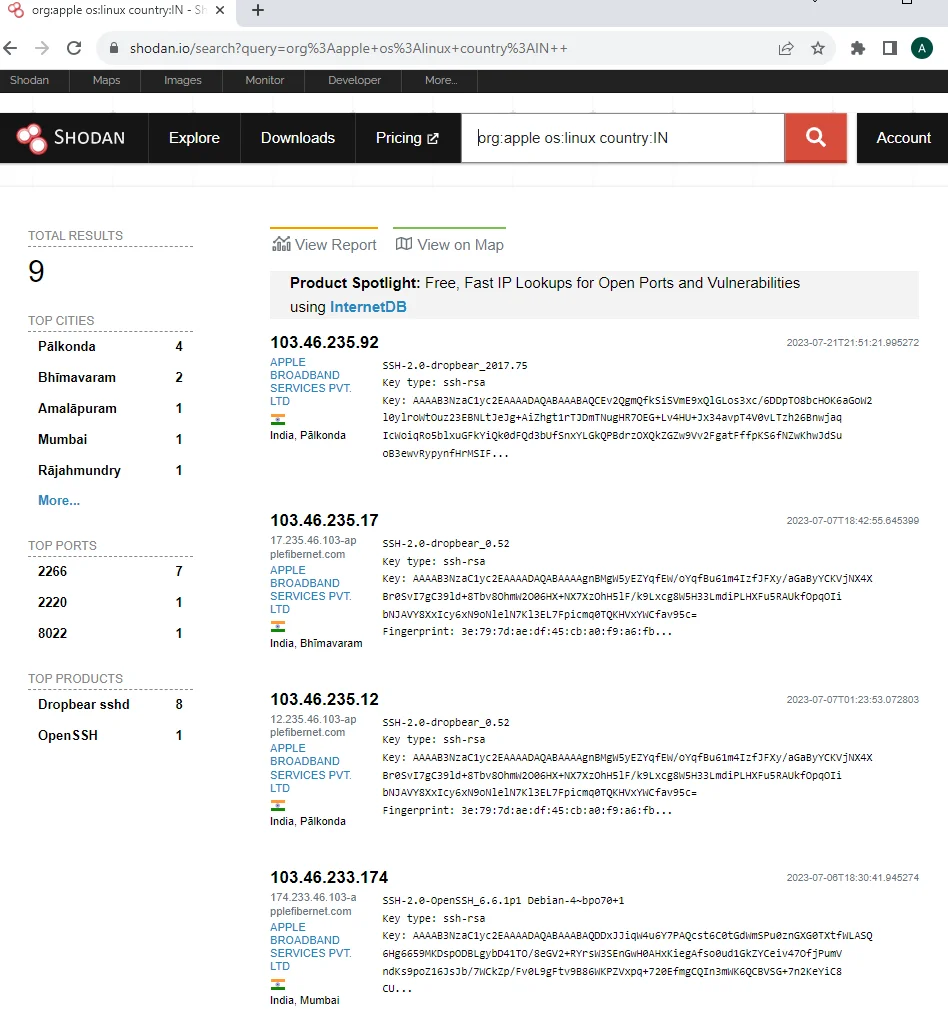
Shodan allows you to search for devices based on the company, operating system, and location. For instance, to find Apple devices running Linux in India, you would enter:
org:apple os:linux country:IN
Example 5: Search for title details and keywords
If you’re looking for specific details mentioned in the title of a device, you can use the “title” filter. For example, to find devices related to cameras with the default settings, you would enter:
title:camera default
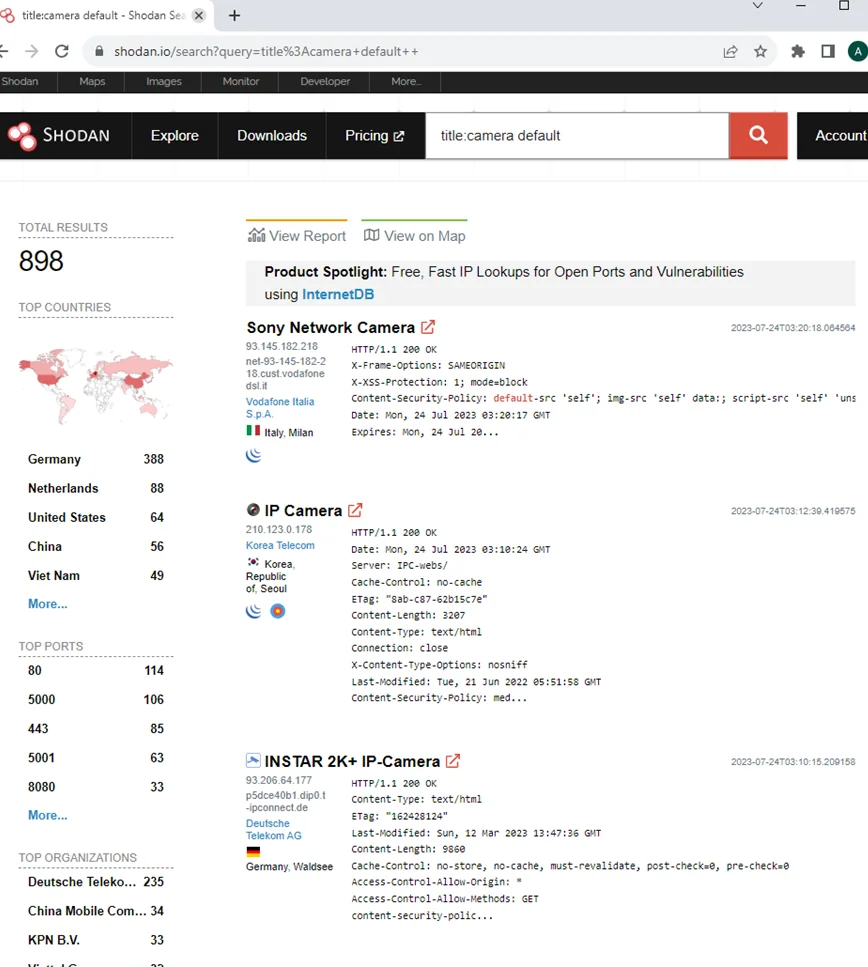
Once you’ve searched, Shodan will exhibit a list of outcomes matching your query. Let’s take a closer look at how to analyze and interpret the information provided.
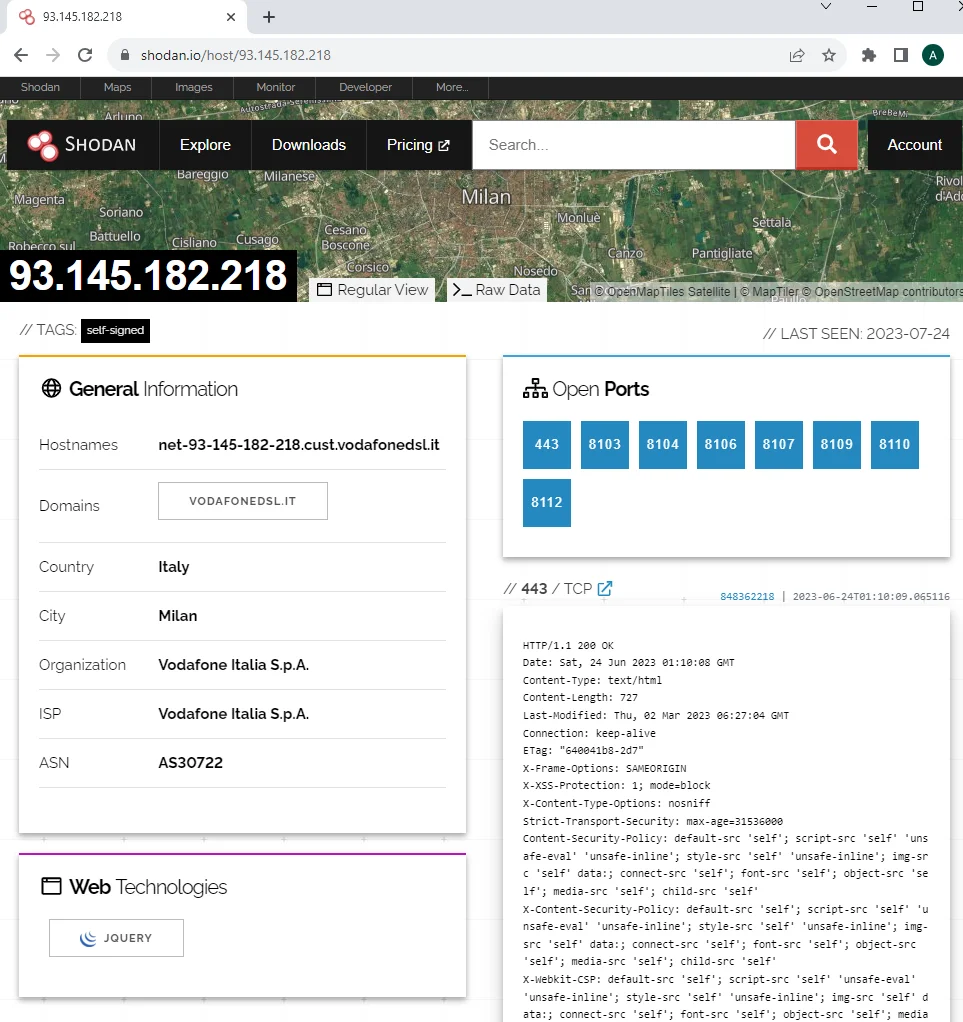
Device Details
When you click on a result, Shodan will display various details about the device. This information typically includes:
Vulnerability Scanning Results
In some cases, Shodan may display vulnerability scanning results for a device. This can provide valuable insights into potential security weaknesses that could be exploited.
Open Ports
Shodan also shows a list of open ports discovered on the device. Each port listing may contain additional information about the protocol and even useful configuration details.
Shodan offers additional features that can enhance your research and analysis:
Downloading Data
If you want to download the search results, Shodan allows you to do so by clicking on “Download Results.” Keep in mind that downloading results may require credits, so use them wisely.
Creating Reports
Shodan also provides the option to create reports of your search results. Simply click on “Create Report” to generate a report that you can download and analyze further.
API and CLI
For more advanced users, Shodan offers an API and a command-line interface (CLI) that provide additional functionality and flexibility. The API allows you to integrate Shodan’s capabilities into your own applications, while the CLI provides a convenient way to interact with Shodan from the command line.
Once you have installed shodan use the following command.
shodan init <your_shodan_api_key>
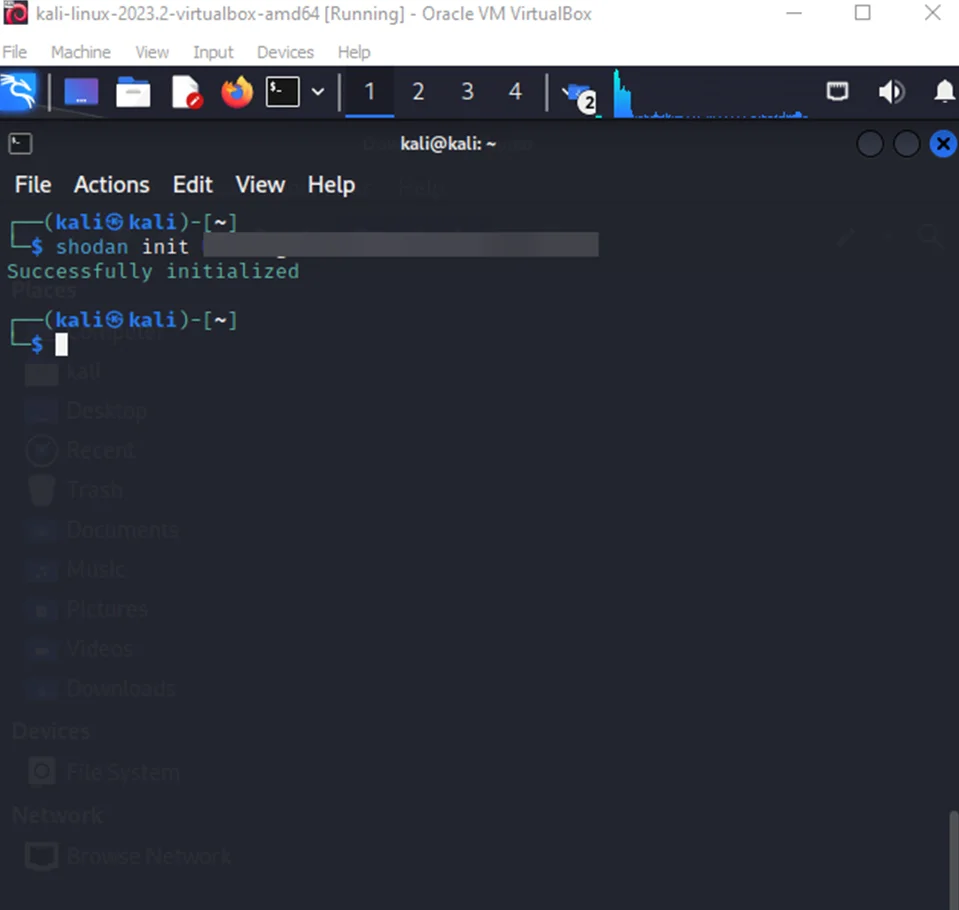
Now, we can start using shodan. Number of tasks can be done using the command line . To get further information, click on the help menu using the following command.
shodan –h
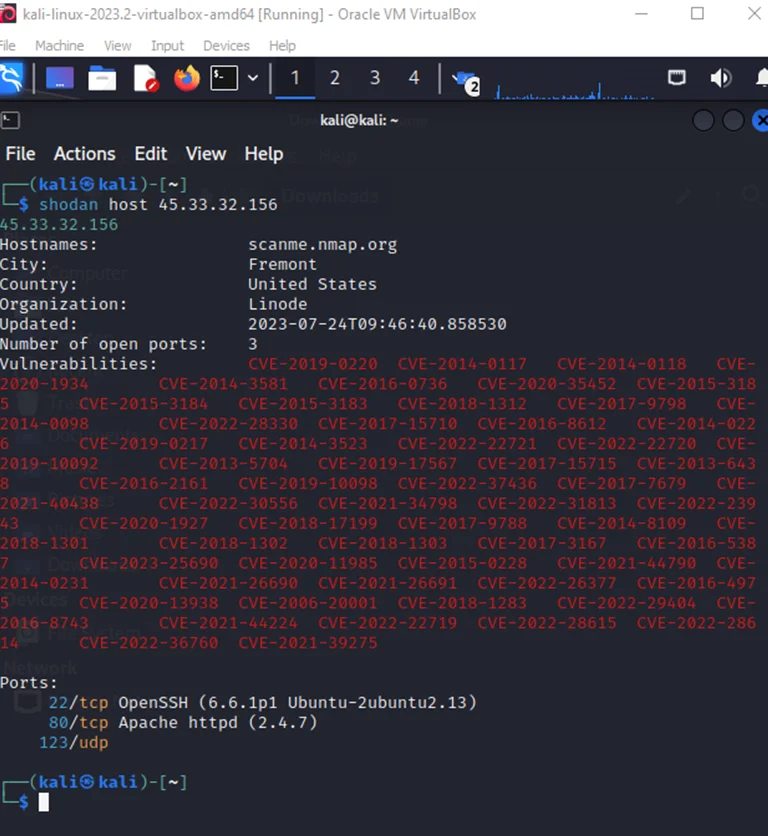
Now, use the following command, to get information related to the host :
shodan host <ip>
Shodan goes beyond text-based results and provides additional visual tools to enhance your exploration:
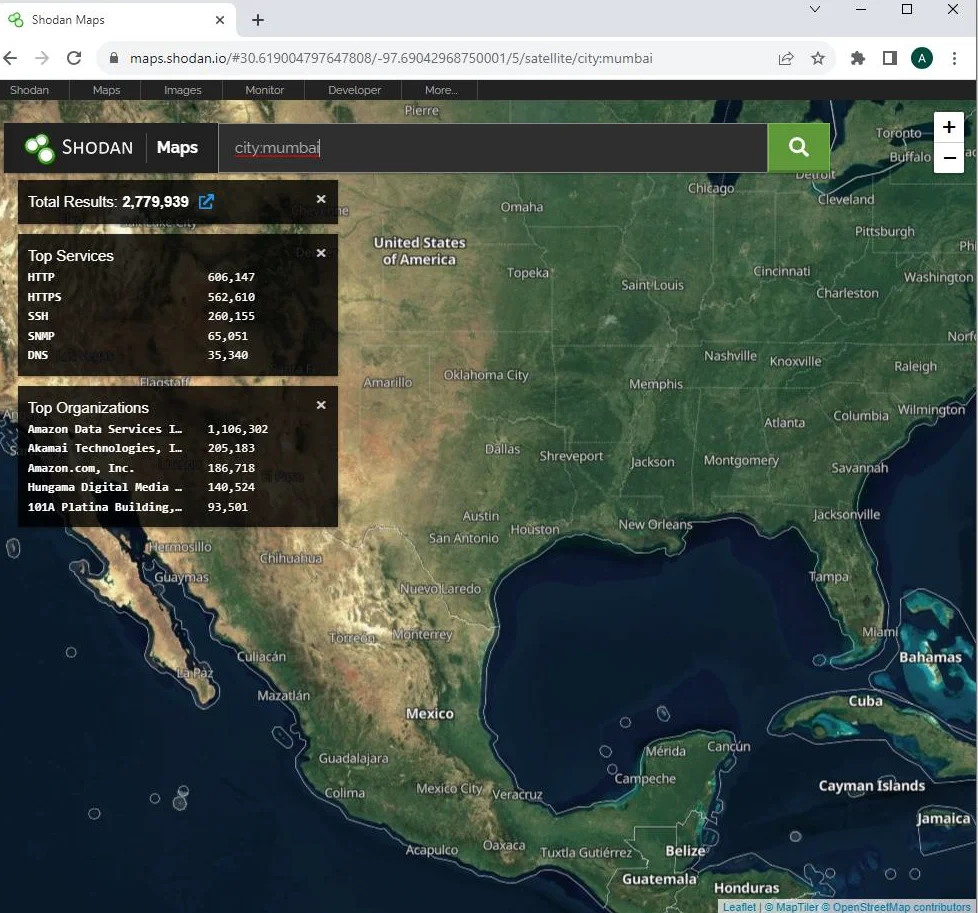
Shodan Maps
It is a graphical map interface that allows you to visualize the geographical distribution of your search results. It provides a unique perspective on the global presence of internet-accessible devices.
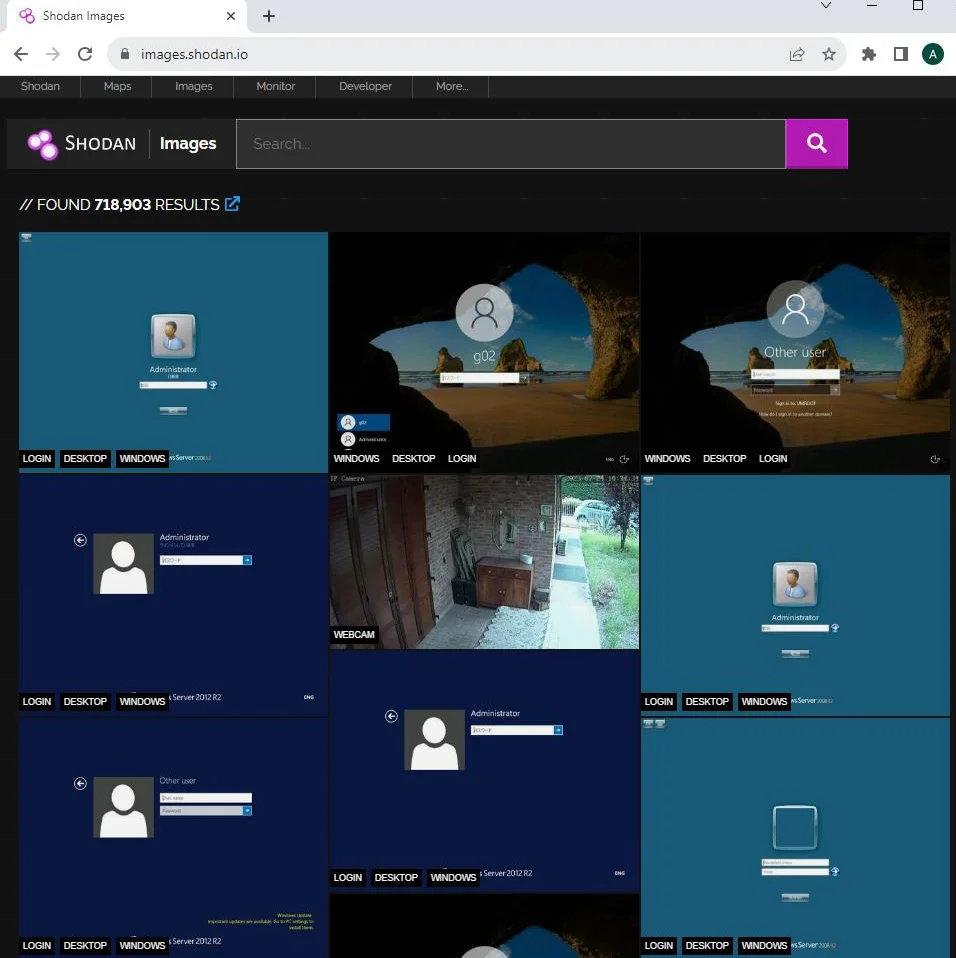
Shodan Images
Shodan Images is a feature that displays screenshots or images captured from various sources, such as VNC, Remote Desktop (RDP), RTSP, webcams, and X Windows. It offers a glimpse into the visual interface of these devices.
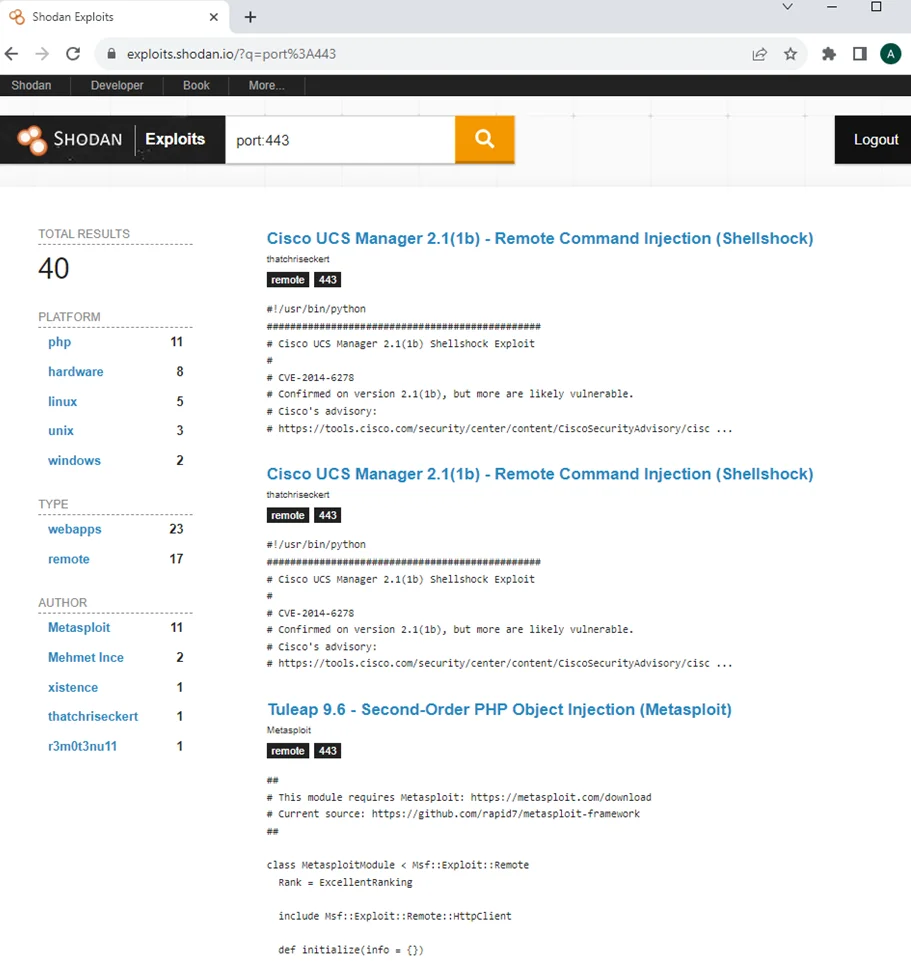
Exploit Search
Shodan provides a basic exploit search function that allows you to search for known vulnerabilities within its database. This can be a useful feature for security researchers and professionals looking to identify potential targets or gather information about specific exploits.
Shodan offers additional tools and services to further enhance your experience:
Shodan provides a tool that shows detailed information about your API usage. This allows you to monitor and track your usage, ensuring that you have the necessary resources to support your research.
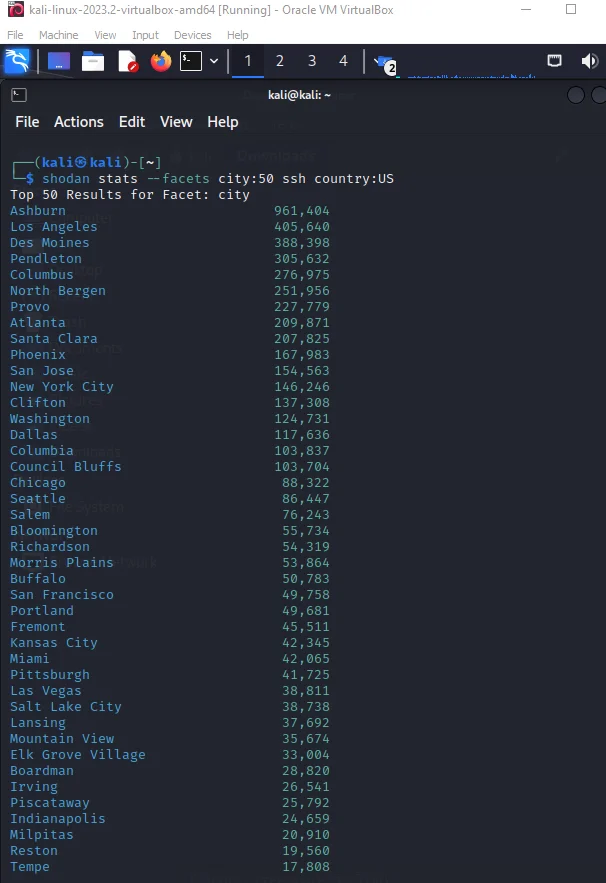
The Shodan API also makes it possible to get a distribution of values for a property using a concept called facets. A facet is typically named after a matching property and lets you see how many results there are for a given property value. Filters let you narrow down search results while facets let you see the big picture of the results.
For example, here is a list of the top 50 cities in the U.S. that are running SSH:
shodan stats --facets city:50 ssh country:US
Shodan’s network monitoring feature allows you to keep track of the devices you have exposed to the internet. It provides notifications, scanning capabilities, and complete visibility into your connected devices.
Navigate to monitor.shodan.io and click on the setup network monitor tab and enter the desired network name and range to monitor
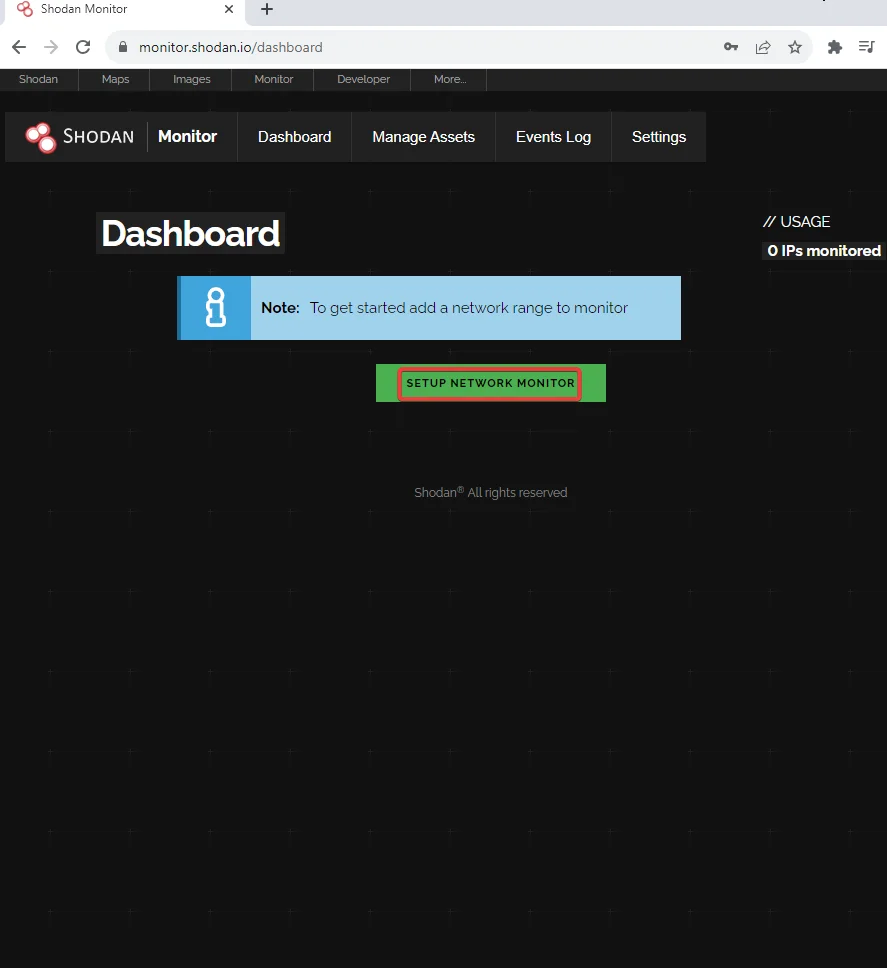
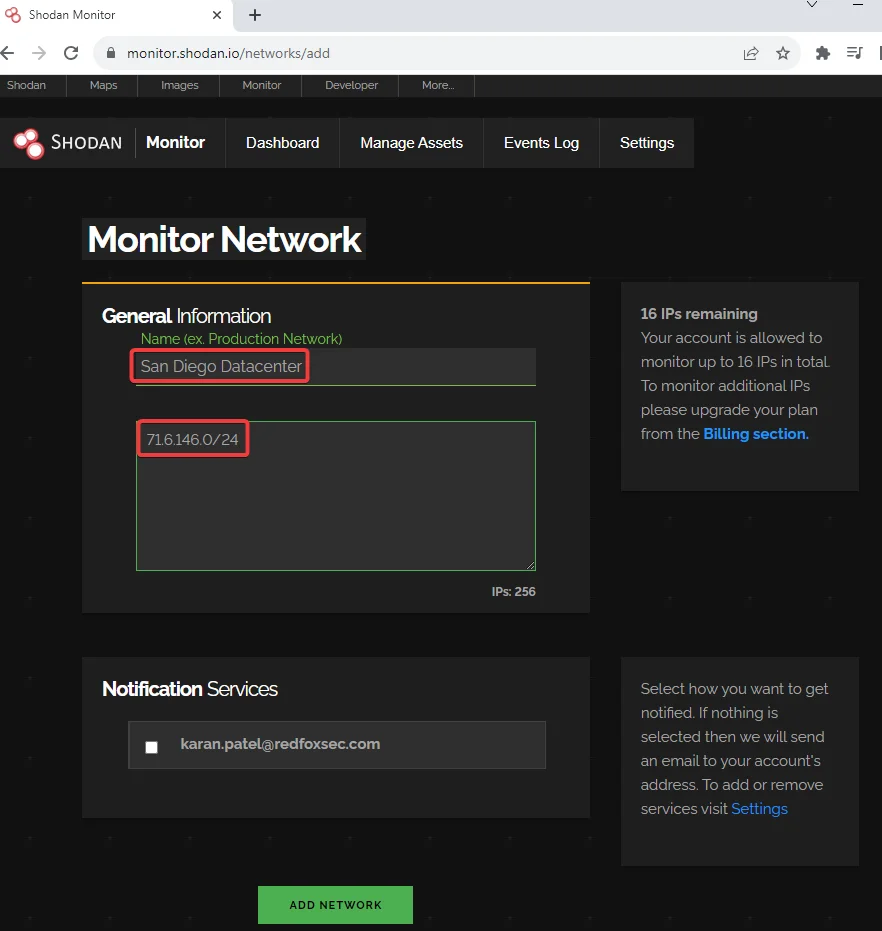
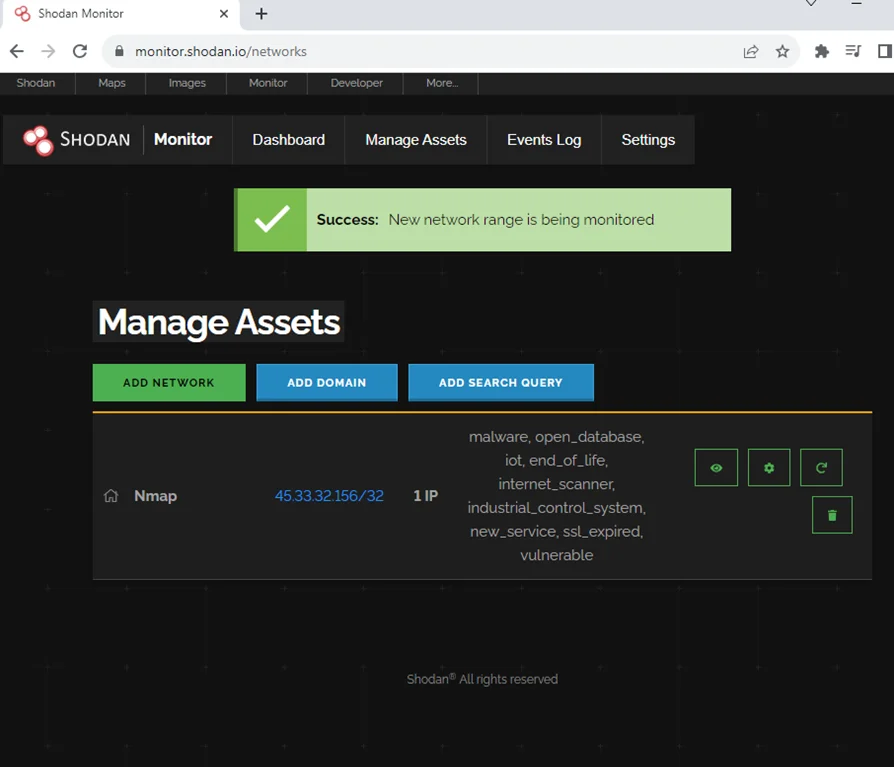
Once done, click on the dashboard and we can see that we got additional information about the network we just added.
Shodan offers specialized tools that cater to specific areas of interest:
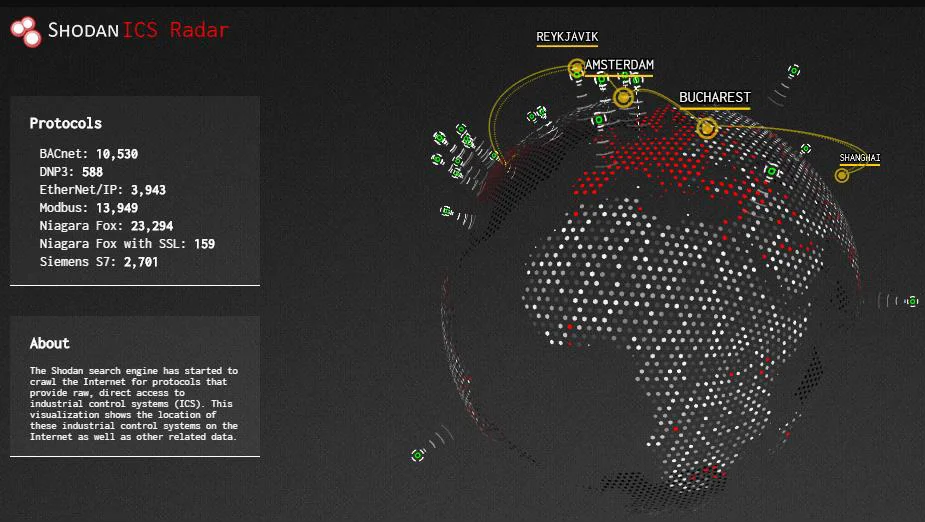
ICS Radar is a 3D map of Industrial Control Systems (ICS) devices found by Shodan’s extensive crawling capabilities. It provides insights into the distribution and prevalence of ICS devices around the world.
The Honeypot Score service assigns a score to an IP address, indicating the probability of it being a honeypot. This can help researchers identify potentially malicious or suspicious devices.
Useful Shodan Queries
To help you get started with Shodan, here are some useful queries that can assist you in finding specific types of devices: Link to GitHub repository with Shodan queries
Shodan is a powerful search engine that opens the door to a hidden world of internet-accessible devices. By utilizing its search filters, you can uncover a vast array of information and potential vulnerabilities. Whether you’re a security professional, researcher, or simply curious about the devices connected to the internet, Shodan offers a unique perspective and invaluable insights into the ever-expanding digital landscape.
Remember, with great power comes great responsibility. Always use Shodan ethically and responsibly, respecting the privacy and security of others. Happy searching!
Disclaimer: The information provided in this article is for educational purposes only. The authors and publishers do not endorse or condone any unauthorized access, hacking, or illegal activities. Always obtain proper authorization before accessing any device or system.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“