
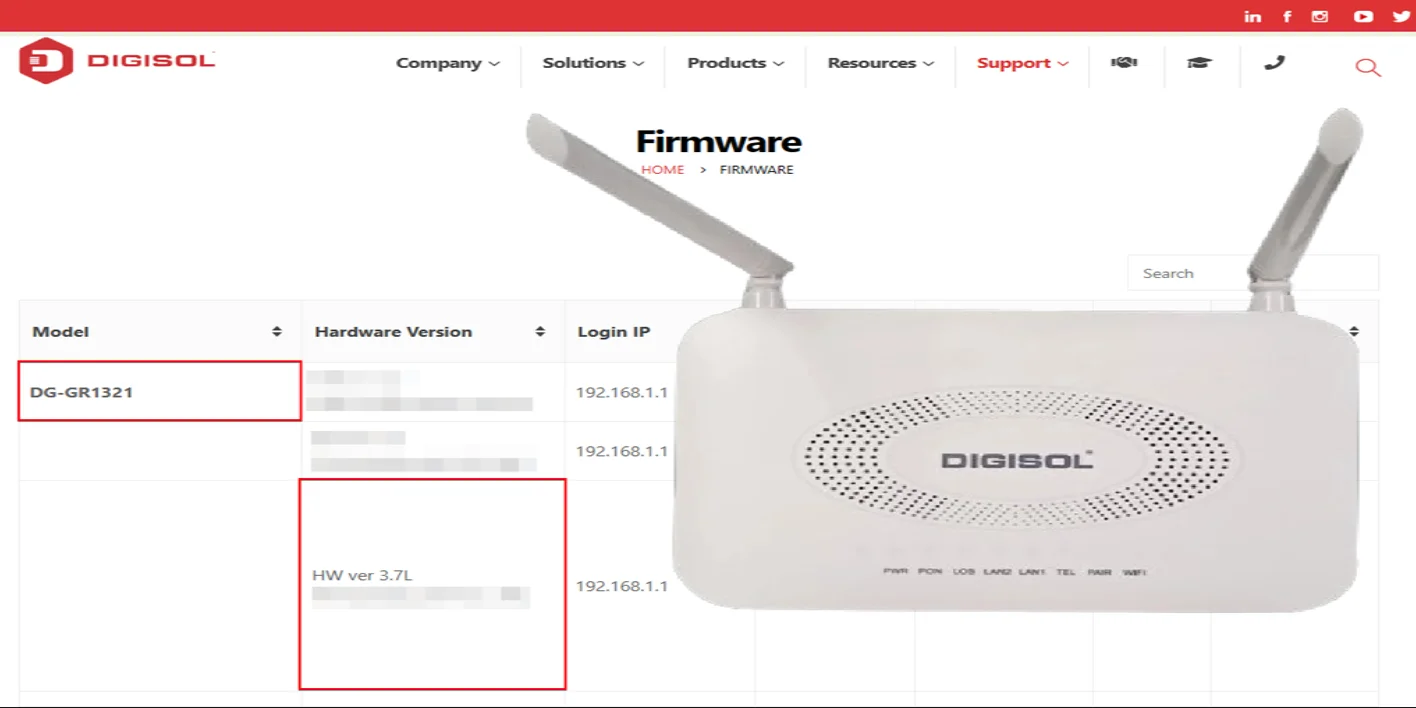
A critical security flaw has been identified in the Digisol DG-GR1321 router (Hardware version: 3.7L; Firmware version: v3.2.02). The issue arises from the router’s improper enforcement of password policies, which are meant to ensure that only strong, complex credentials are allowed. Instead of rejecting weak or non-compliant passwords, the device accepts them, effectively nullifying its own security safeguards.
What makes this particularly concerning is that the flaw can be exploited by anyone with physical access to the router. In practical terms, an attacker could set up or modify the router with an extremely weak password—sometimes as simple as a single digit. Once this is done, the router becomes much easier to compromise, since such passwords can be guessed or brute-forced with minimal effort.
This blog will help understand this flaw and how to remedy it.
Exploiting this weakness in the Digisol DG-GR1321 router can have serious consequences for both individuals and organizations. Because the flaw allows the creation of weak or non-compliant passwords, attackers can exploit it in several ways:
Bypass password restrictions – Instead of being forced to use strong, complex passwords, attackers can set trivial ones such as “1” or “1234.” This renders the entire password policy ineffective and creates a direct path for compromise.
Gain unauthorized access – With weak credentials in place, malicious actors can easily guess or brute-force their way into the router’s management interface. Once inside, they may take over administrative controls, locking out legitimate users.
Manipulate network settings – A compromised router can be reconfigured to reroute traffic, disable protective measures like firewalls, or even inject malicious settings. This manipulation could disrupt business operations or compromise home networks.
Expose sensitive data – Since routers handle all inbound and outbound traffic, unauthorized access could allow attackers to intercept communications, capture login details, or monitor sensitive information flowing through the network.
The overall impact is a dramatic reduction in network security, increasing the likelihood of data breaches, unauthorized surveillance, and potentially even larger attacks on connected systems.
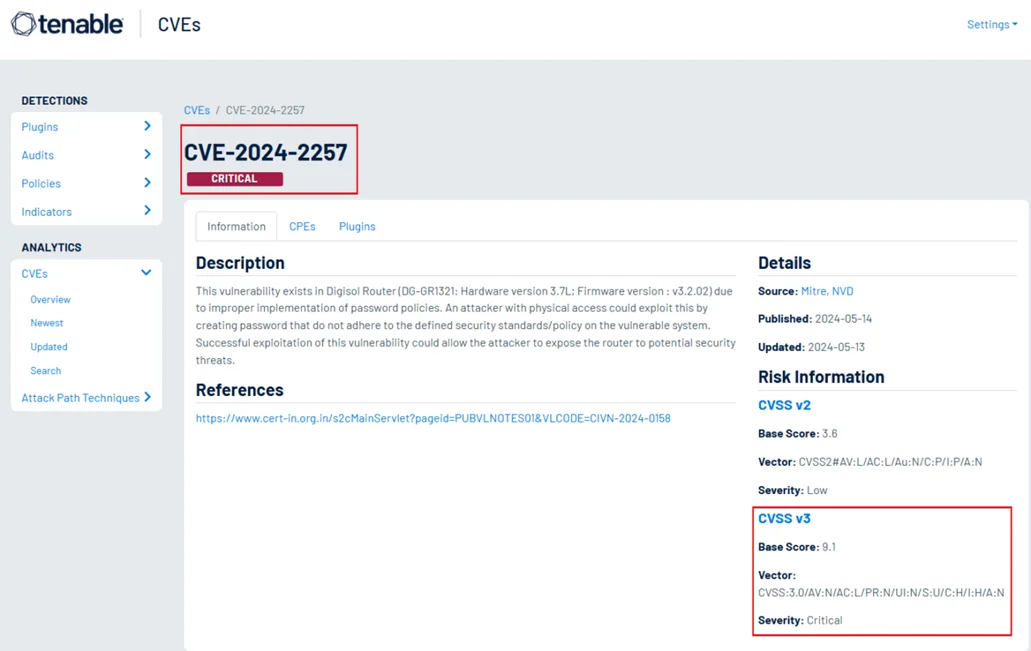
The root cause of this vulnerability lies in the router’s failure to properly enforce password policies. Password complexity requirements are supposed to ensure that users create secure, hard-to-guess credentials, but the DG-GR1321 ignores these rules altogether. The consequences are severe:
Weak password acceptance – Instead of rejecting unsafe choices, the router permits passwords as simple as a single digit, making them trivial to guess.
Reduced security posture – Because password strength is one of the first lines of defense, bypassing this measure drastically weakens the overall security of the device.
Increased attack surface – With weak or predictable passwords in place, the router becomes a prime target for attackers who rely on simple brute-force methods or default password lists.
Higher exposure to threats – Once compromised, the router can be used as an entry point into the broader network, allowing attackers to exploit connected devices, spread malware, or launch man-in-the-middle (MITM) attacks.
This vulnerability essentially undermines the router’s built-in security framework, creating a dangerous gap that attackers can easily exploit.
During testing, it was confirmed that the DG-GR1321 router allows users to set a password consisting of just one digit. This example highlights how the device completely disregards its advertised password policy.
The ease of exploitation cannot be overstated: a single-digit password is not only predictable but also requires virtually no effort to crack. With such a low barrier to entry, even unsophisticated attackers could compromise the router in minutes, gaining full administrative access and control over the network.
To address this vulnerability, it is crucial that users take immediate action:
Upgrade to the latest firmware – Digisol has released updated firmware for the DG-GR1321 (hardware version 3.7L, starting with V3.1.XX). The latest version may include critical patches to fix this flaw. Firmware can be downloaded directly from the Digisol firmware portal.
Adopt strong password practices – Even after applying updates, users should follow best practices when creating router credentials. This includes using a mix of uppercase and lowercase letters, numbers, and symbols, with a minimum length of 12 characters.
By combining firmware updates with robust password hygiene, organizations and individuals can significantly reduce their exposure to this vulnerability.
The Digisol DG-GR1321 router contains a Password Policy Bypass vulnerability (CVE-2024-2257) that allows attackers to create extremely weak passwords, effectively disabling the router’s intended security mechanisms. Exploiting this flaw can lead to unauthorized access, manipulation of network settings, interception of sensitive data, and broader security risks for all connected devices.
Fix: Update the router’s firmware to the latest version and enforce strong password practices to restore security.
At Redfox Security, we are a global team of cybersecurity professionals dedicated to helping organizations identify and mitigate risks before attackers can exploit them. Our services include penetration testing, vulnerability assessments, and security consulting, all designed to strengthen your organization’s defenses.
If you’re looking to enhance your security posture, contact us today to discuss your specific needs. Our experts can help you uncover hidden vulnerabilities, provide detailed remediation guidance, and ensure your systems are protected against evolving threats.
We also offer comprehensive training programs to empower your teams with the knowledge and skills needed to proactively safeguard your digital environment. Join us on our mission to build a safer, more resilient cybersecurity future.