
Routers are the backbone of modern digital connectivity, bridging the gap between private networks and the broader internet. Because of this critical role, they are often targeted by attackers seeking to exploit weaknesses that could compromise network integrity and expose sensitive data. Recently, a significant vulnerability has been discovered in the Digisol DG-GR1321 router (Hardware version 3.7L; Firmware version v3.2.02).
Unfortunately, not all vulnerabilities are purely remote. Some exist at the hardware or interface level, providing hidden entry points that attackers with physical access can abuse. These often-overlooked flaws can lead to full system compromise and put confidential data at risk.
In this blog, we will explore CVE-2024-4231, a recently documented vulnerability in the Digisol DG-GR1321 router that stems from improper access control on its UART/Serial interface. We’ll break down how the flaw works, its potential impact, and steps you can take to mitigate the risks.
The vulnerability affects the Digisol DG-GR1321 router (Hardware version 3.7L; Firmware version v3.2.02). The issue lies in the router’s UART/Serial interface, which provides system logs during boot and direct access to the root shell. Unfortunately, this interface lacks proper authentication, enabling attackers to connect and issue commands with full privileges.
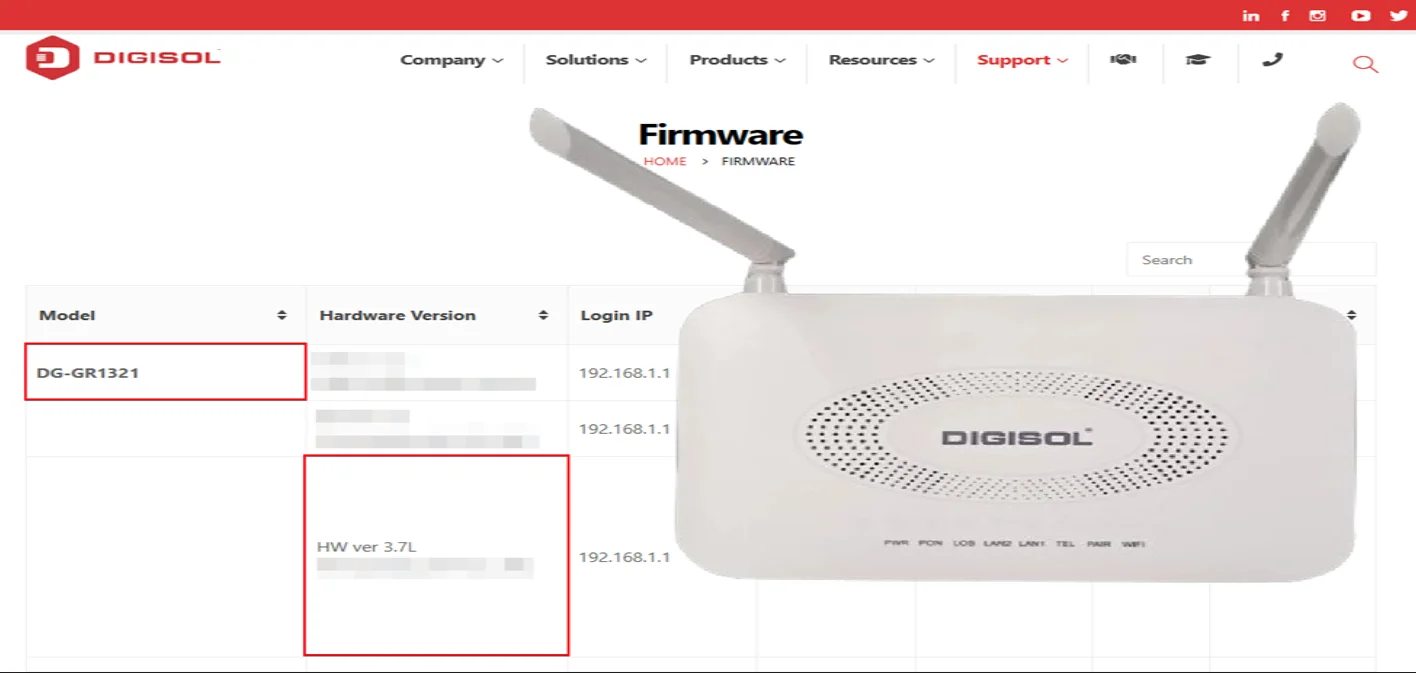
Affected Device: Digisol DG-GR1321
Hardware Version: 3.7L
Firmware Version: v3.2.02
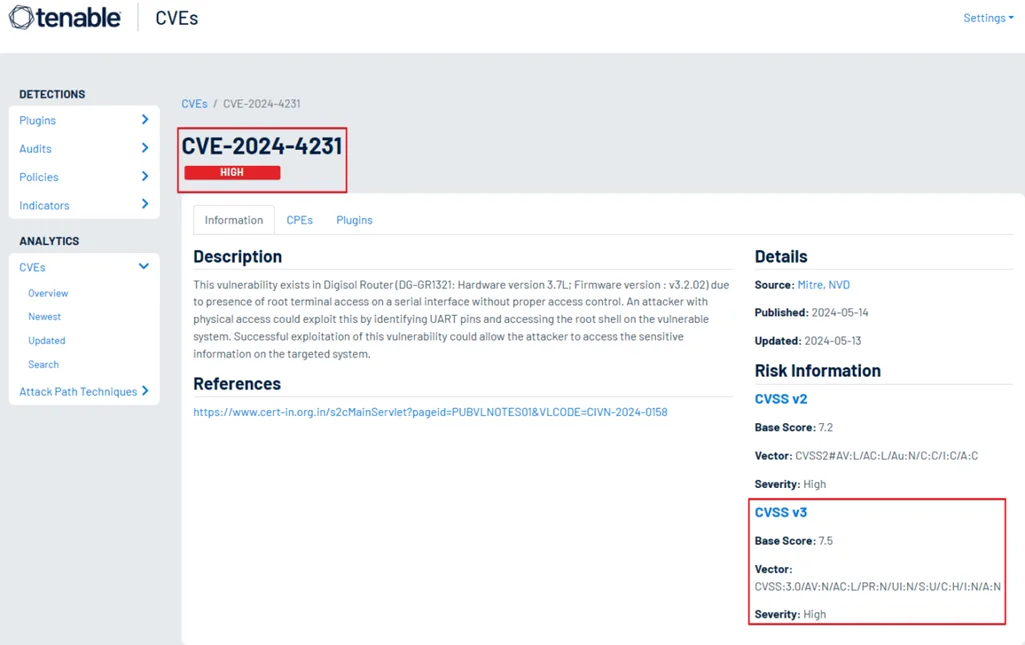
CVE Identifier: CVE-2024-4231
Type of Vulnerability: Improper Access Control
The UART/Serial interface on the router’s PCB is composed of four pins: Rx, Tx, Vcc, and Gnd.
Key technical specifications:
Signal level: TTL
Baud rate: 115200
Functionality: Outputs logs during boot and grants direct root shell access
Critical issue:
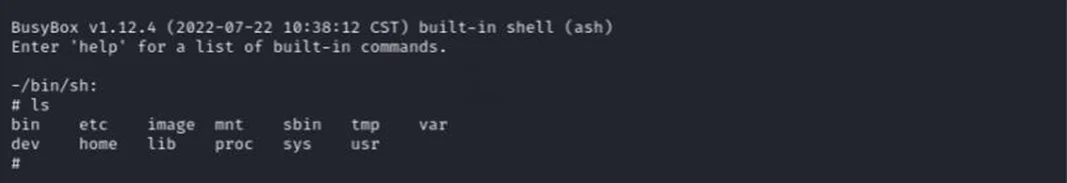
The root shell is accessible without requiring authentication.
No security barriers prevent unauthorized access, allowing attackers to execute privileged commands.
A successful exploitation of CVE-2024-4231 involves the following steps:
Locate UART Pins – Identify Rx, Tx, Vcc, and Gnd pins on the router’s circuit board.
Connect to the Interface – Use a UART-to-USB adapter and terminal emulator software to establish communication.
Observe Boot Logs – During startup, the router outputs log messages through the serial connection.
Gain Root Access – The terminal presents a root shell prompt, confirming unrestricted access to the operating system.
Exploiting this vulnerability can have severe consequences:
Root-level access: Attackers can fully control the router.
Data exposure: Sensitive information stored or transmitted via the device may be extracted.
Network compromise: Unauthorized users could monitor, manipulate, or disrupt traffic.
Security breach: Confidentiality, integrity, and availability of data are at risk.
Although physical access is required, routers deployed in offices, shared spaces, or less secure environments remain vulnerable.
The most effective way to mitigate this vulnerability is to upgrade the firmware to the latest version provided by Digisol. Updated firmware packages address security flaws and may patch this specific issue.
Firmware for DG-GR1321 (HW v3.7L, version V3.1.XX and above) can be downloaded from the Digisol Firmware Website.
A backup link is also available through this Google Drive link.
Recommendation: Always keep network hardware updated with the latest firmware releases and disable unnecessary debug interfaces where possible.
Vulnerability: Improper Access Control (CVE-2024-4231)
Affected Device: Digisol DG-GR1321 (HW v3.7L, FW v3.2.02)
Root Cause: Unauthenticated root shell access via UART interface
Impact: Full device compromise, data extraction, and network exposure
Mitigation: Upgrade to the latest Digisol firmware
CVE-2024-4231 highlights how overlooked debug interfaces like UART can create serious security gaps. Even though this attack requires physical access, organizations must consider the risk of insider threats and insecure deployment environments. Protecting critical infrastructure means accounting for both remote and local vulnerabilities.
At Redfox Security, we specialize in identifying such risks and strengthening organizational defenses. Our team provides penetration testing, vulnerability assessments, and security consulting to ensure your systems are resilient against real-world threats.
If you want to improve your organization’s security posture or safeguard your network infrastructure, reach out to us today. We also offer hands-on security courses designed to help professionals build expertise in detecting and mitigating vulnerabilities like CVE-2024-4231.