
As cars transform into rolling computers, they bring not just convenience—but also new risks. Modern vehicles are no longer mechanical boxes on wheels; they are distributed, networked computing platforms that run complex software, collect data, and connect to the outside world. Connected vehicles now house infotainment systems, advanced driver assistance and autonomous-driving capabilities, telematics and wireless communication modules, and app ecosystems. While these innovations dramatically improve safety, comfort, and mobility, they also open new avenues for cyber threats that can affect privacy, safety, and business continuity.
This guide approaches car hacking from a cybersecurity perspective: what a vehicle’s digital architecture looks like, where the weak points are, how attackers can (and have) exploited them, and—crucially—how industry and users can reduce risk.

Today’s cars are complex digital ecosystems. They rely on numerous interconnected systems, both hardware and software, that collectively manage everything from acceleration to entertainment.
1.Hardware Components:
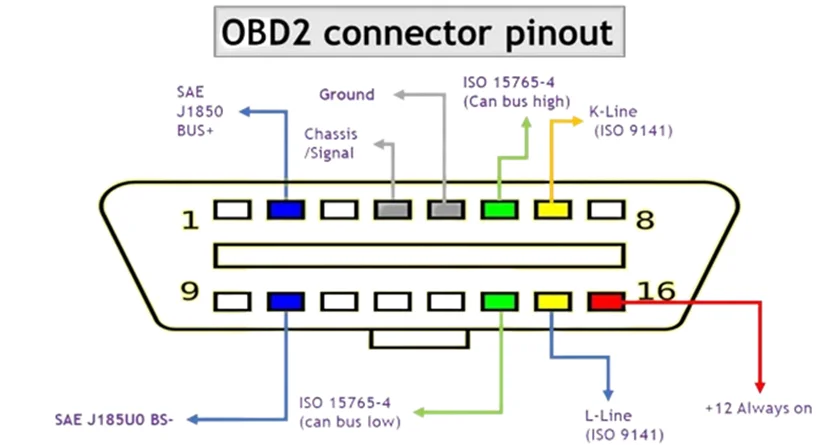
(i) OBD-II Ports: These are like the car’s doctor’s office. They let mechanics plug in computers to check how the car is doing.
(ii) USB Ports:Enable device connectivity but can also be exploited for malware injection.
(iii) Wireless Modules: Bluetooth, Wi-Fi, and cellular connections expand functionality but widen the attack surface.
2. Software Components

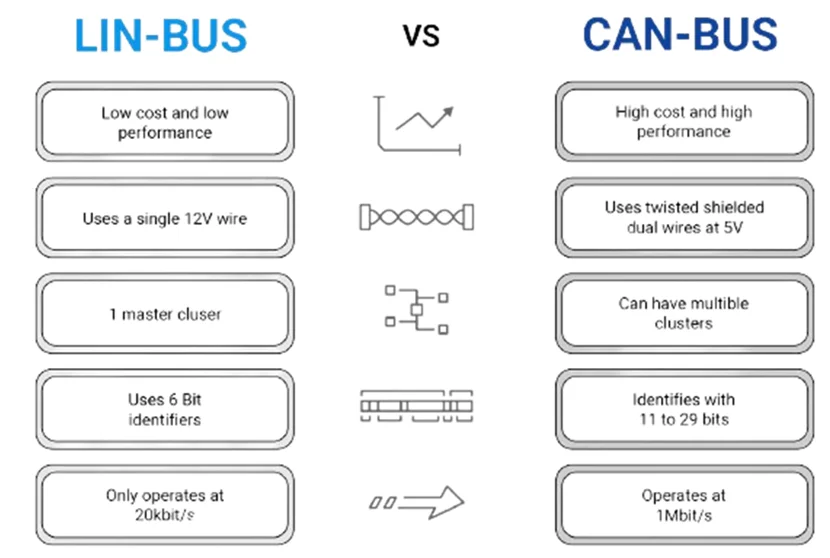
1. CAN (Controller Area Network) Bus
History: Developed by Bosch in 1985, CAN was designed to replace complex point-to-point wiring systems in vehicles. It allowed ECUs (Electronic Control Units) to communicate efficiently without relying on a central host computer.
Functionality: CAN is a message-based protocol where all devices share a common bus. Each message has a priority, and the bus arbitration ensures that the highest-priority message gets transmitted without collision.
Applications: Ubiquitous in automotive systems, powering communication in engine management, powertrains, chassis control, braking, airbags, and battery management. Also widely used in industrial automation.
Advantages:
Reliable and robust in noisy automotive environments
Cost-effective and reduces wiring complexity
Extremely well-established, with a massive ecosystem of tools and expertise
2. FlexRay
History & Purpose: Introduced in the early 2000s by a consortium of automakers (including BMW and DaimlerChrysler), FlexRay was designed to handle the increasing demand for deterministic and fault-tolerant communication in advanced automotive systems.
Functionality: FlexRay offers time-triggered communication with predictable timing, along with fault tolerance via redundant channels. It supports higher data rates (up to 10 Mbps), making it suitable for safety-critical and real-time applications.
Applications: Primarily used in advanced driver assistance systems (ADAS), x-by-wire technologies (brake-by-wire, steer-by-wire), and powertrain control where deterministic behavior is critical.
Advantages:
Deterministic and predictable data delivery
High speed compared to CAN and LIN
Redundancy and fault tolerance for safety-critical systems
3. Local Interconnect Network (LIN)
History & Role: Developed in the late 1990s by a consortium led by Volkswagen, LIN was designed as a low-cost complement to CAN for simpler, slower subsystems.
Functionality: LIN uses a single-master, multiple-slave architecture, providing low-speed communication (up to 20 Kbps). It is used for non-critical, local communications within a vehicle.
Applications: Commonly used in body electronics, such as window regulators, seat control, mirrors, sunroofs, and climate control sensors.
Advantages:
Extremely cost-effective
Simple architecture with reduced complexity
Integrates seamlessly with CAN as a subnetwork
4. Automotive Ethernet
History & Purpose: Adapted from traditional IT networking, Automotive Ethernet has gained adoption in the 2010s to support the huge bandwidth needs of modern vehicles.
Functionality: Enables high-speed communication (100 Mbps to multi-Gbps) using existing Ethernet standards adapted for the automotive environment (single twisted-pair cables, time-sensitive networking).
Applications: Vital for infotainment, high-resolution cameras, ADAS sensors, over-the-air (OTA) updates, and vehicle-to-everything (V2X) communication.
Advantages:
Extremely high bandwidth compared to legacy automotive protocols
Leverages existing IT standards and infrastructure
Scalable for future autonomous driving requirements
5. Wireless Protocols
History & Role: As vehicles became more connected, wireless standards from the consumer world (Bluetooth, Wi-Fi, cellular) were integrated into cars.
Functionality:
Bluetooth: Enables short-range connectivity for hands-free calling, audio streaming, and keyless entry.
Wi-Fi: Supports in-car internet access, OTA updates, and media sharing.
Cellular/Telematics (3G, 4G, 5G): Connects vehicles to cloud platforms for navigation, diagnostics, remote management, and fleet operations.
V2X (Vehicle-to-Everything): Emerging protocols like DSRC and C-V2X allow vehicles to communicate with infrastructure, pedestrians, and other cars.
Applications: Infotainment, remote diagnostics, vehicle tracking, emergency services (eCall), OTA updates, and smart city integration.
Advantages:
Expands vehicle capabilities beyond the car itself
Enables real-time data exchange with cloud and infrastructure
Essential for autonomous and connected mobility ecosystems
The attack surface includes every possible entry point for cyber intrusions:
Remote Access Points:
Telematics & Cellular Systems—can be exploited over networks.
Wi-Fi & Bluetooth—targets for remote takeover of infotainment or control systems.
Physical Access Points:
OBD-II Port—a direct gateway into vehicle networks.
USB Ports—susceptible to malware-loaded devices.
Internal Networks:
CAN Bus—hackers can inject malicious commands or intercept data.
ECUs—vulnerable to firmware manipulation.
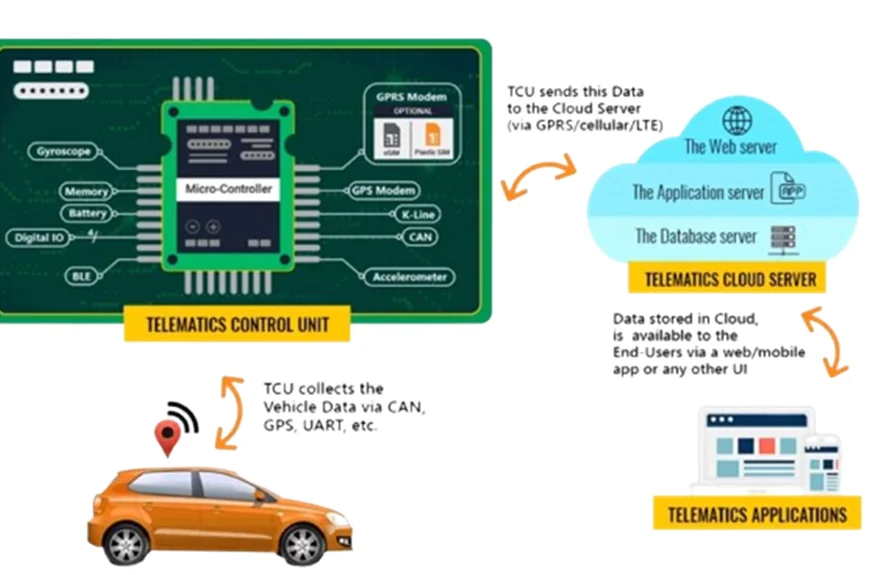
Here’s how a typical vehicle cyberattack unfolds:


Hackers remotely controlled a Jeep Cherokee’s steering and brakes via the infotainment system—leading to a recall of over 1.4 million vehicles.
Vehicles are susceptible to different weaknesses that attackers might exploit to gain unauthorized access or control. Common vulnerabilities include:
1.Insecure Communication Protocols:
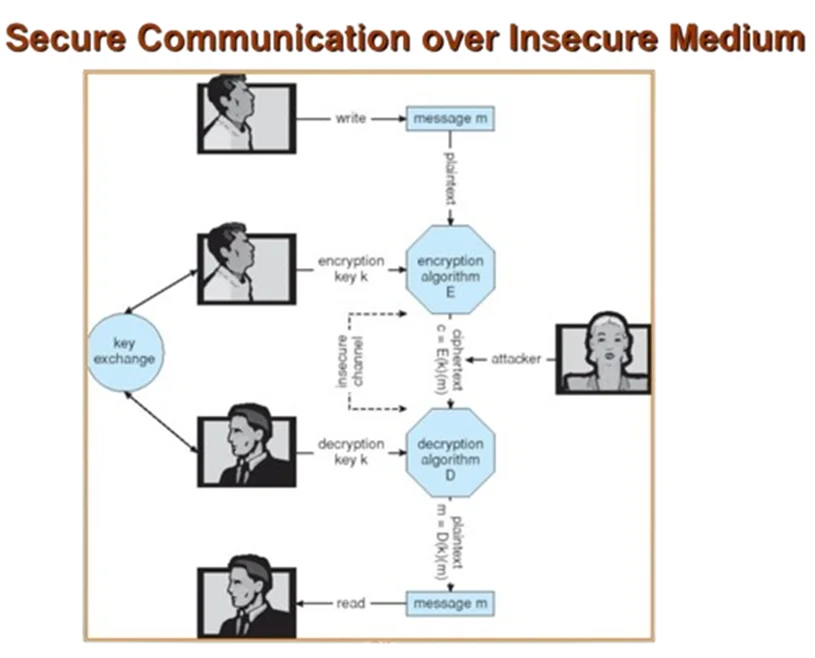
2.Software Bugs:
3.Lack of Authentication:
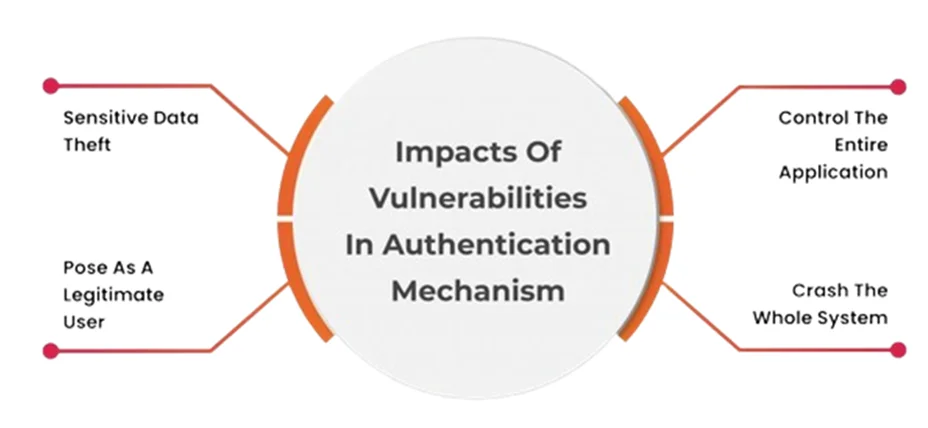
4. Physical Access Points:
In car hacking, attackers can exploit various vulnerabilities in-vehicle systems to gain unauthorized access, manipulate functionality, or cause disruptions. Here are some common types of attacks possible in car hacking:
1. Remote Attacks: These attacks target vulnerabilities in the vehicle’s remote communication systems, such as cellular networks, Wi-Fi, or Bluetooth connections. Attackers may exploit weaknesses in these systems to remotely access the vehicle’s infotainment system, telematics, or control functions.
2. Physical Access Attacks: Physical access attacks involve gaining direct physical access to the vehicle or its components. This could include tampering with the vehicle’s OBD-II port, USB interfaces, or other entry points to install malware, manipulate hardware, or extract sensitive information.
3. ECU Manipulation: Electronic Control Units (ECUs) control various vehicle functions, including engine management, braking, steering, and more. Attackers may exploit vulnerabilities in ECU firmware or software to manipulate these functions, potentially leading to vehicle malfunctions or accidents.
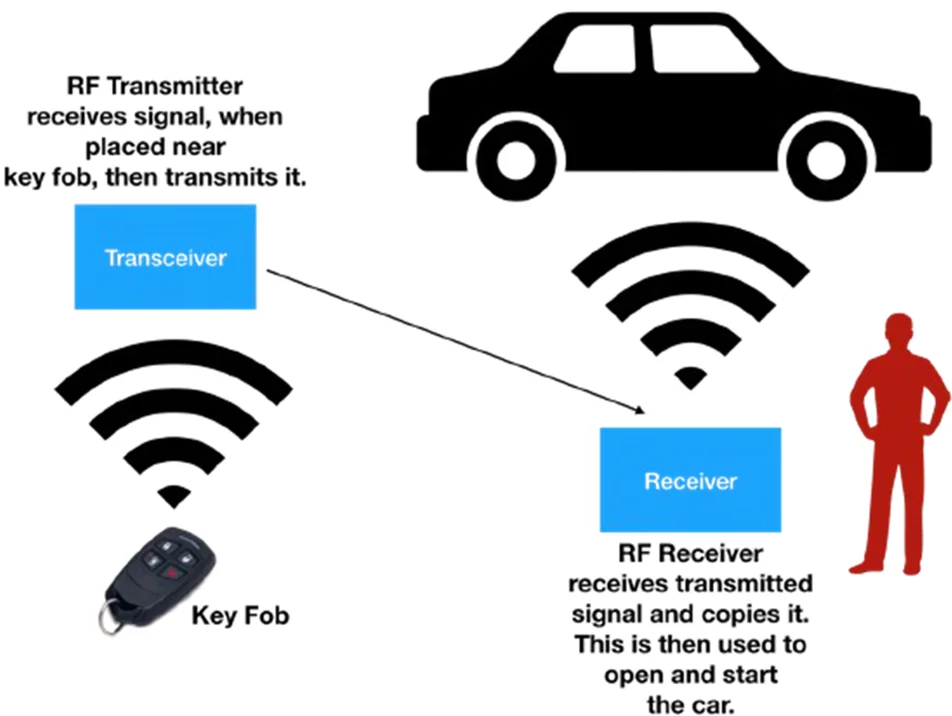
4. Key Fob Attacks: Key fobs are used for remote keyless entry and ignition systems in many modern vehicles. Attackers may attempt to intercept, clone, or jam signals transmitted between key fobs and vehicles to gain unauthorized access or steal vehicles.
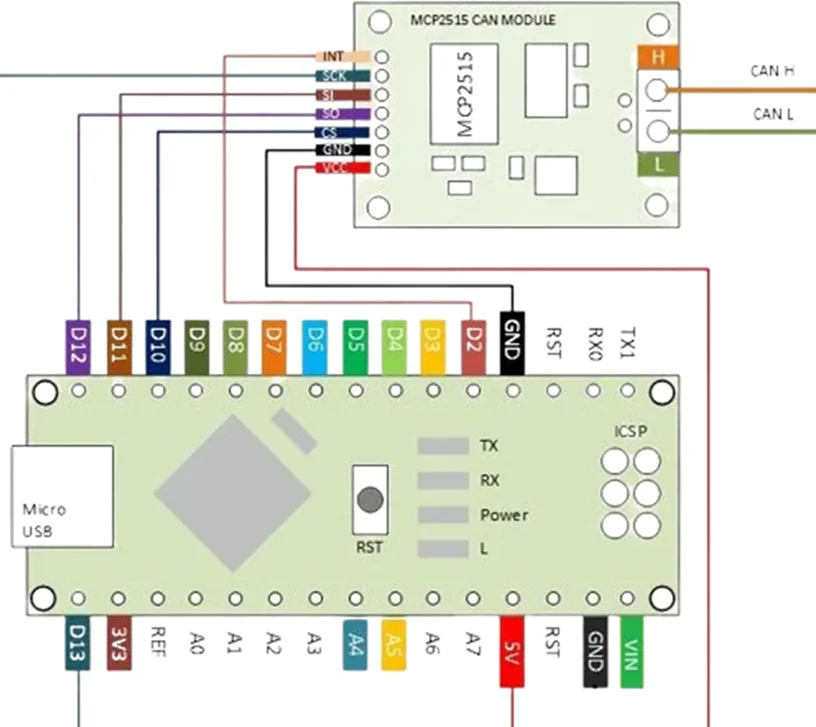

7. OTA Update Exploitation: Over-The-Air (OTA) updates are increasingly common in modern vehicles, allowing manufacturers to remotely update vehicle software. Attackers may exploit vulnerabilities in OTA update mechanisms to install malicious firmware or inject malware into vehicle systems.
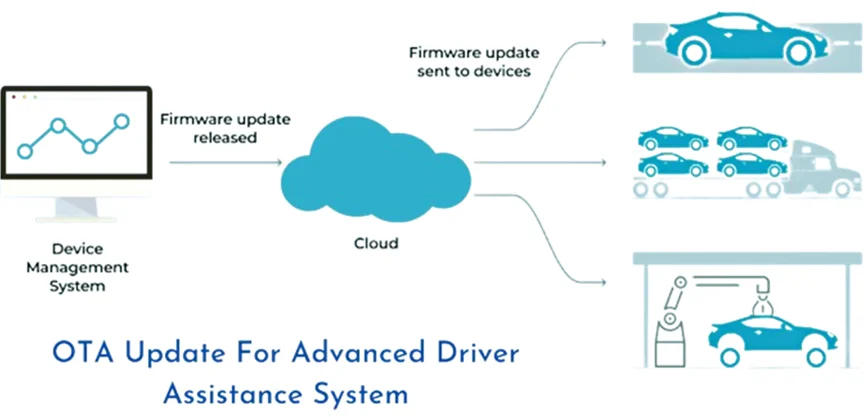
8. GPS Spoofing: Global Positioning System (GPS) spoofing attacks involve manipulating GPS signals to deceive vehicle navigation systems. Attackers may use GPS spoofing to mislead drivers, tamper with location-based services, or disrupt autonomous vehicle operations.
9. Tools and Techniques Used in Car Hacking
Hackers employ a range of tools and methods to detect and exploit weaknesses in vehicle systems. Some commonly used tools include:

To safeguard vehicles against hacking, manufacturers and users can implement several mitigation strategies and best practices:
As vehicles continue to evolve with advanced technologies like autonomous driving and V2X (Vehicle-to-Everything) communication, the landscape of car hacking will also change. Key future trends include:
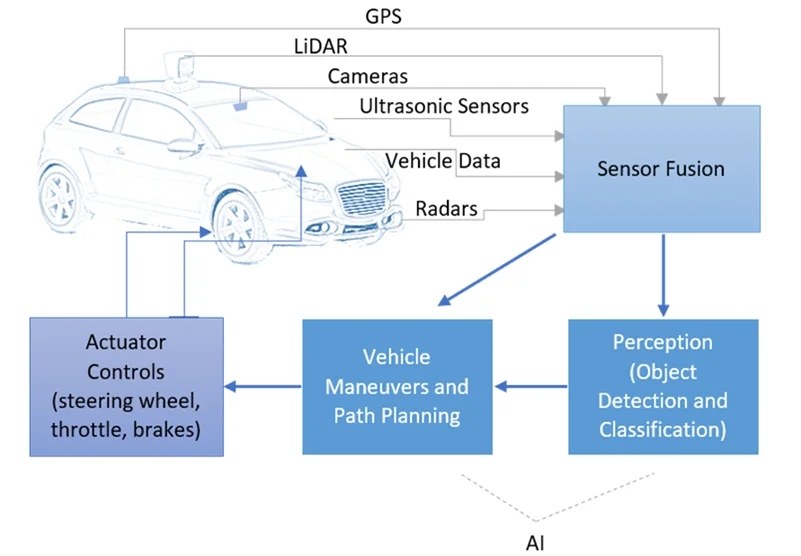
As vehicles become more connected and autonomous, car hacking is no longer theoretical—it’s happening now. Weaknesses in wireless systems, control units, and vehicle apps open the door to attackers. The automotive industry must respond with robust cybersecurity, from secure protocols to continuous threat assessments.
Redfox Security specializes in advanced vehicle penetration testing, CAN bus analysis, and firmware reverse engineering. Whether you’re an OEM, Tier 1 supplier, or startup, we’ll help you stay ahead of evolving threats.
Contact us today to schedule a security consultation. Also you can learn from the best by enrolling in our car hacking and embedded systems courses—designed for engineers, researchers, and red teamers.