
A critical privilege escalation vulnerability (CVE-2024-28326) has been identified in the Asus RT-N12+ B1 router. The device exposes an unrestricted root terminal via its UART (Universal Asynchronous Receiver-Transmitter) interface, lacking any form of authentication or access control. This flaw allows anyone with physical access to the device to execute arbitrary commands with root privileges, posing a significant threat to system integrity and data confidentiality.
An attacker with physical access to the router can exploit the UART interface to:
Gain root-level access to the operating system
Alter system configurations
Install malicious software
Intercept or exfiltrate sensitive data
Permanently compromise the device and network
Given that this model has reached end-of-life status, no official security updates are planned, which leaves the device perpetually vulnerable.
Interface Type: UART/Serial
Pinout: Rx (Receive), Tx (Transmit), Vcc (Power), GND (Ground)
Logic Level: TTL (Transistor-Transistor Logic)
Baud Rate: 57600
Access: Physical
Authentication: None
Privilege Level: Root
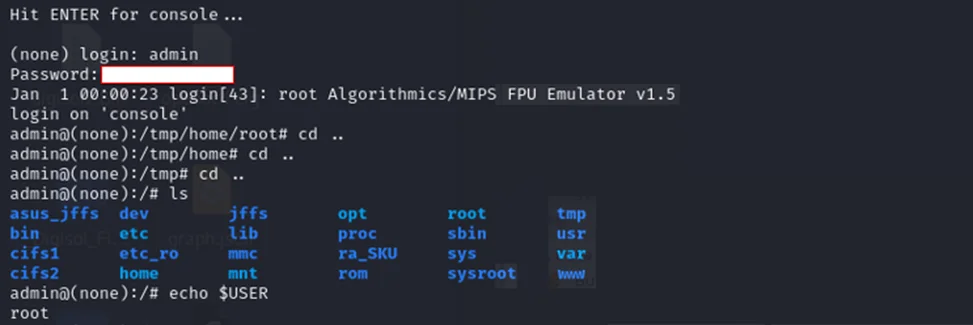
Upon connecting to the UART interface and pressing the Enter key during the boot process, a root shell is exposed without requiring any credentials.
During our assessment, the device consistently allowed root terminal access over UART. The boot logs were observable, and upon pressing Enter, full root access was granted—without authentication.
This demonstrates a critical flaw in credential storage and interface security design, confirming the severity of this vulnerability.
Physical Security: Restrict physical access to the router to prevent UART exploitation.
Replace Device: Consider replacing the Asus RT-N12+ B1 with a newer, supported model.
Interface Hardening: Disable or physically block UART interfaces when not required.
Principle of Least Privilege: Limit access to debug interfaces and enforce proper access control policies on all administrative ports.
The Asus RT-N12+ B1 router contains a severe security vulnerability—CVE-2024-28326—that allows attackers with physical access to gain root-level access via an unsecured UART/Serial interface. Operating at TTL logic level (57600 baud), this interface exposes the system’s inner workings without any authentication, enabling full control over the device. With the product marked as end-of-life, this issue remains unpatched unless users opt to test the beta firmware provided by Asus.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.