
In today’s connected world, routers act as the first line of defense for both home and business networks. When vulnerabilities are discovered in these devices, they can open the door to significant security threats. Recently, a critical flaw (CVE-2024-28327) was identified in the Asus RT-N12+ B1 router, linked to the insecure storage of sensitive credentials in cleartext.
In this blog, we will explore the details of this vulnerability, its potential impact on users, the timeline of communications with Asus, and the available mitigation options. By understanding these risks, users can make informed decisions to better protect their networks.
The Asus RT-N12+ B1 router’s insecure credential storage exposes users to multiple risks:
Unauthorized Access: Cleartext passwords can be directly read and abused by attackers.
Router Manipulation: Compromised accounts allow malicious reconfiguration of the router.
Data Exposure: Attackers can pivot into the network, potentially accessing sensitive data and connected devices.
Because the RT-N12+ B1 has officially reached end-of-life status, these risks remain unpatched, leaving users without long-term security coverage.
21/02/2024 – Initial Contact: Vulnerability report submitted to Asus.
28/02/2024 – First Follow-Up: Contacted Asus to confirm receipt.
05/03/2024 – Asus Response: Asus acknowledged the issue, stating that the RT-N12+ B1 (also known as RT-N300 B1) has reached end of its product life cycle. Firmware updates were discontinued years ago. They released a beta firmware version for testing and invited community feedback.
01/04/2024 – Second Follow-Up: Continued communication with Asus.
01/04/2024 – Asus Response: Acknowledgment received.
02/04/2024 – Third Follow-Up: Further inquiries sent.
12/04/2024 – Asus Response: Asus confirmed challenges with the firmware size for this model, reiterated its end-of-life status, and again offered the beta firmware while requesting user feedback on whether it mitigates the vulnerability.
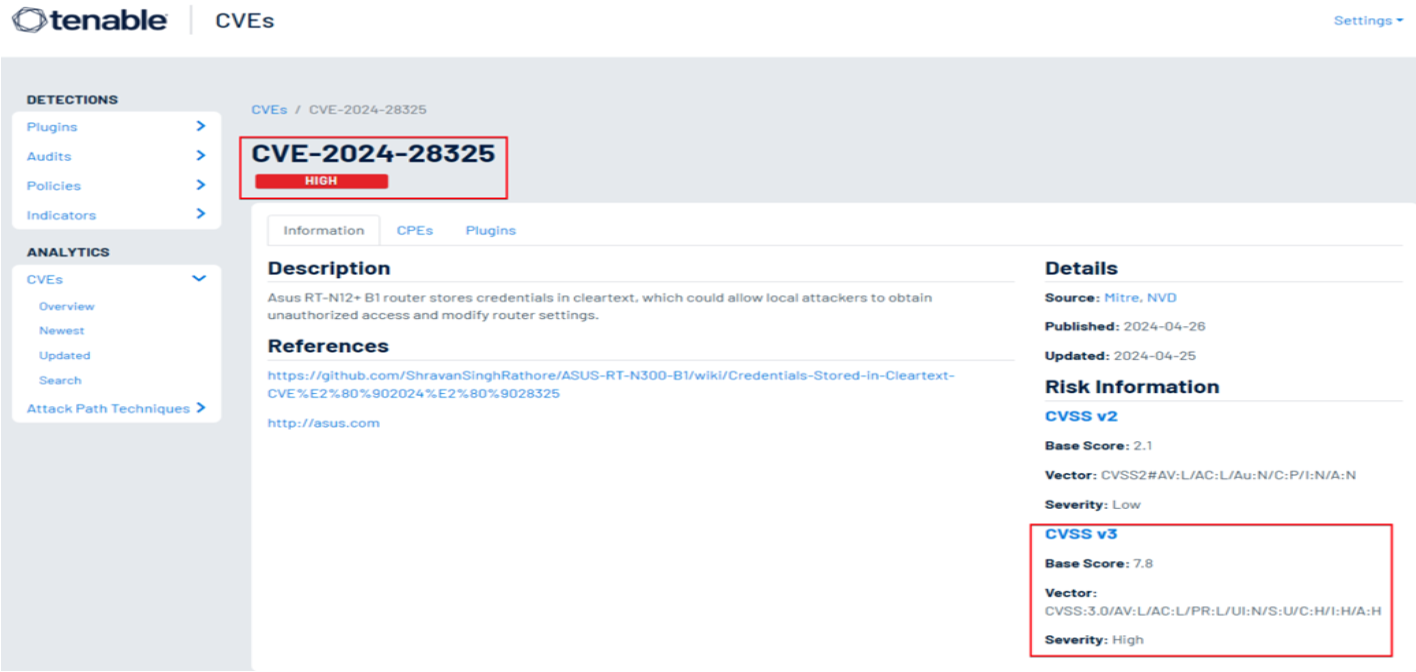
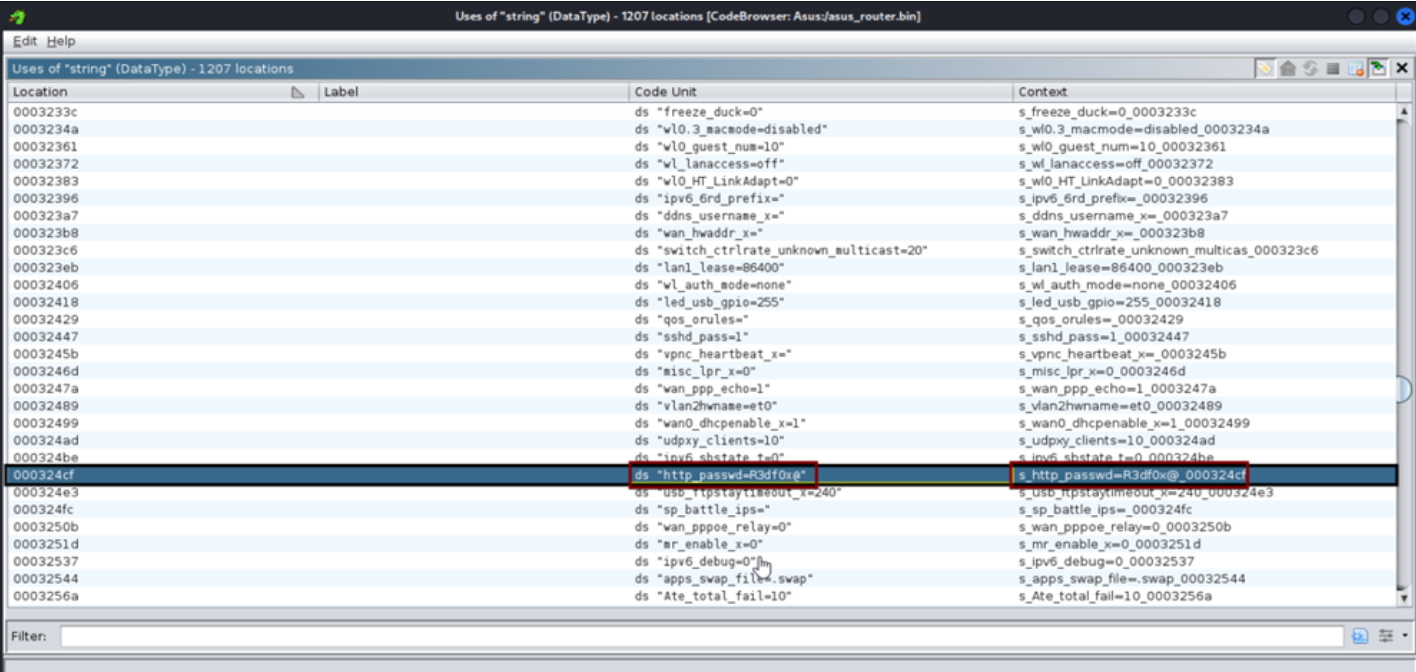
The Asus RT-N12+ B1 router is affected by a cleartext credential storage vulnerability. Instead of encrypting user passwords, the router stores them in plain text within its database. This design flaw means that anyone who gains access to the firmware or database can easily retrieve login credentials.
If an unauthorized individual obtains the router’s firmware or database files, they can read the stored passwords without decryption. With this access, attackers can manipulate configurations, hijack the router, or establish persistent control over the network.
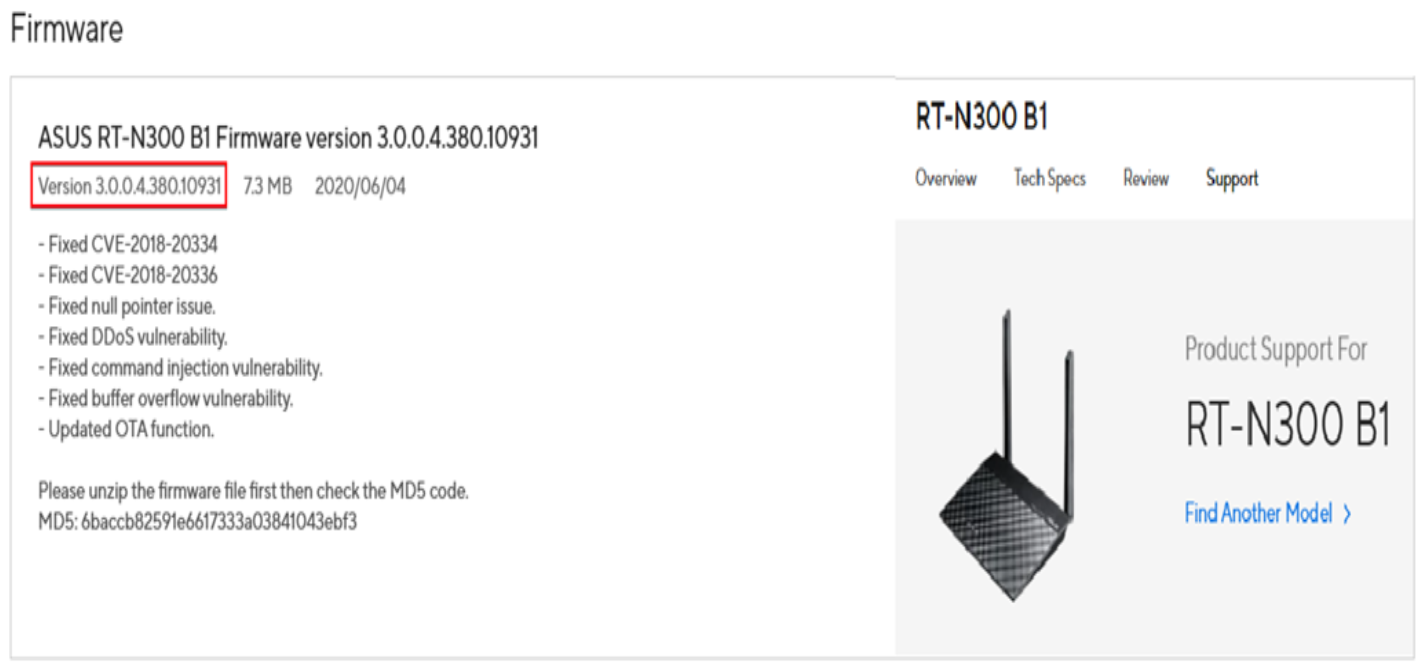
Upgrade Firmware: Install the latest beta firmware provided by Asus and test whether it resolves the issue.
Replace Hardware: Given the router’s unsupported status, the most secure option is to transition to a modern, actively maintained model that receives regular security updates.
Enhance Network Hygiene: Regularly update login credentials, monitor device logs for unusual activity, and segment sensitive systems from general traffic.
The Asus RT-N12+ B1 router suffers from cleartext password storage (CVE-2024-28327). This flaw allows attackers to gain unauthorized access and manipulate router settings. Since the device is no longer officially supported, users are strongly advised to install the beta firmware or replace the router entirely.
Redfox Security is a global network of expert security consultants committed to helping organizations protect their digital assets. We specialize in identifying vulnerabilities, improving resilience, and providing actionable recommendations tailored to your needs.
If you’re looking to improve your organization’s security posture, contact us today to discuss your security testing requirements.
And if you want to grow your expertise, join us by enrolling in our comprehensive security training courses—designed to equip professionals with the knowledge and skills to defend against modern cyber threats.