
Routers form the backbone of modern digital infrastructure, enabling connectivity for homes, businesses, and entire networks. However, when vulnerabilities exist in these devices, they can quickly become gateways for attackers to exploit, compromise, and steal sensitive data.
In this blog, we examine multiple critical vulnerabilities identified in the LB-Link BL-W1210M router. These flaws range from weak password enforcement to insecure credential storage and clickjacking risks. Each issue represents a potential entry point for attackers to gain unauthorized access or fully compromise the device.

Device: LB-Link BL-W1210M
Firmware Versions: V1.0.0 / Open-MATCH-V1.02 / V1.2.8
1. Password Policy Bypass / Inconsistent Password Policy (CVE-2024-33373)
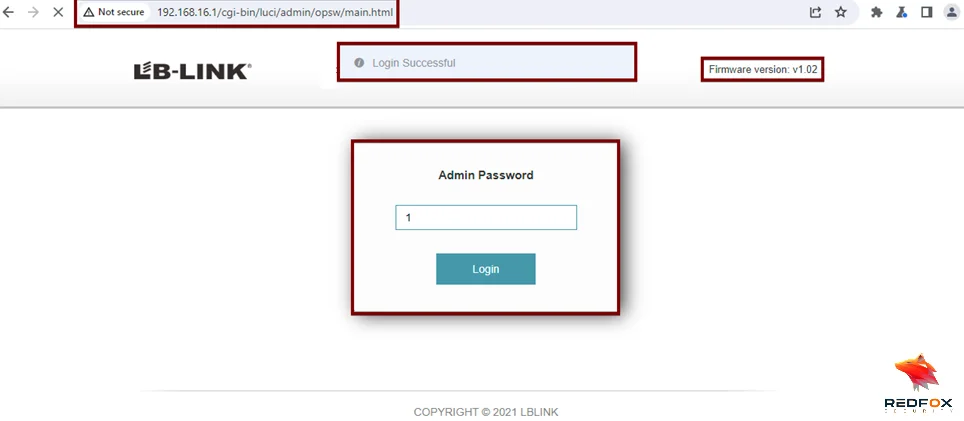
2. Incorrect Access Control (CVE-2024-33374)
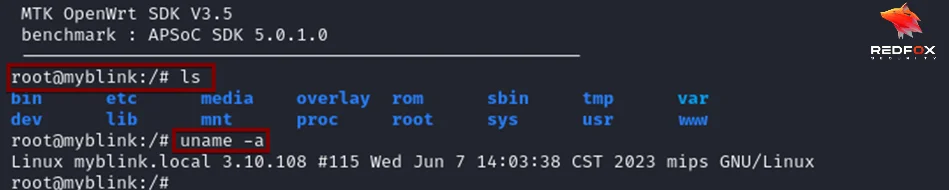
3. Credentials Stored in Cleartext (CVE-2024-33375)
USER1 and USER2 were recovered directly from the firmware.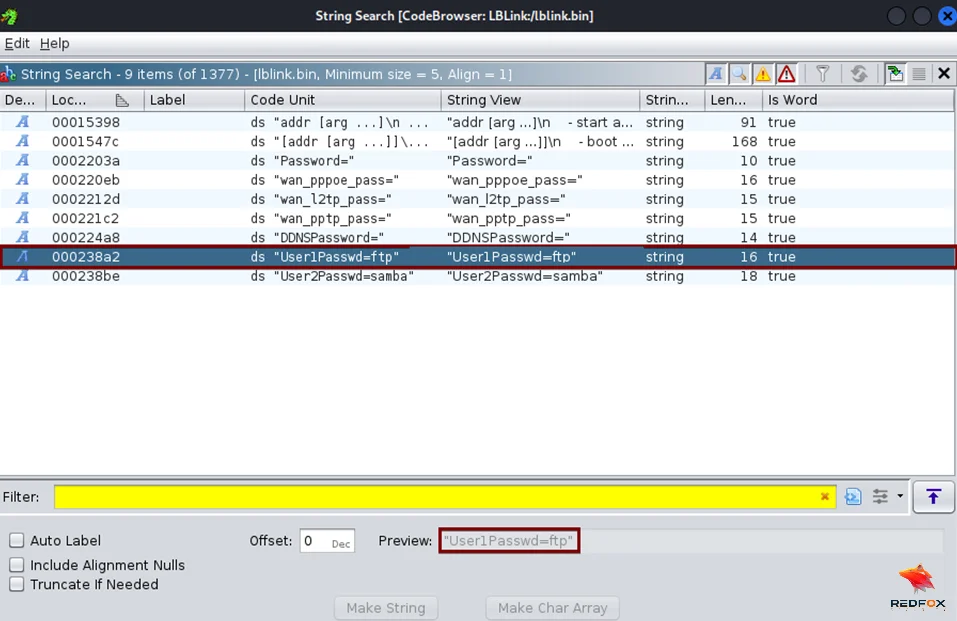
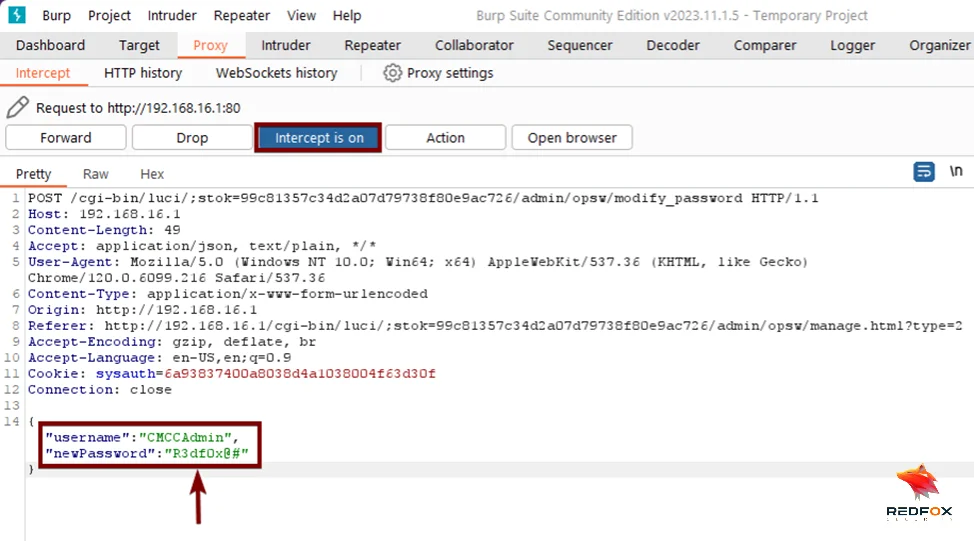
4. Clickjacking Vulnerability (CVE-2024-33377)
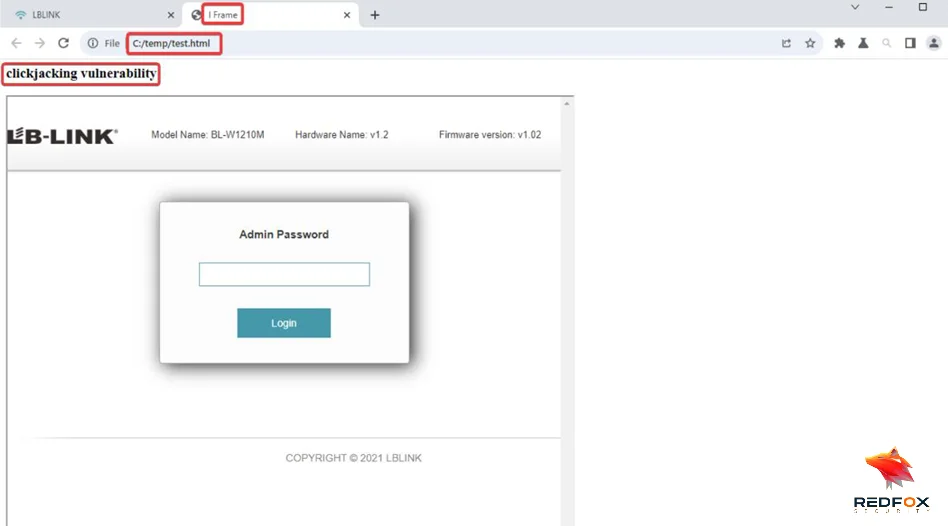
5. Outdated JavaScript Library
axios.min.js v0.21.0 was confirmed.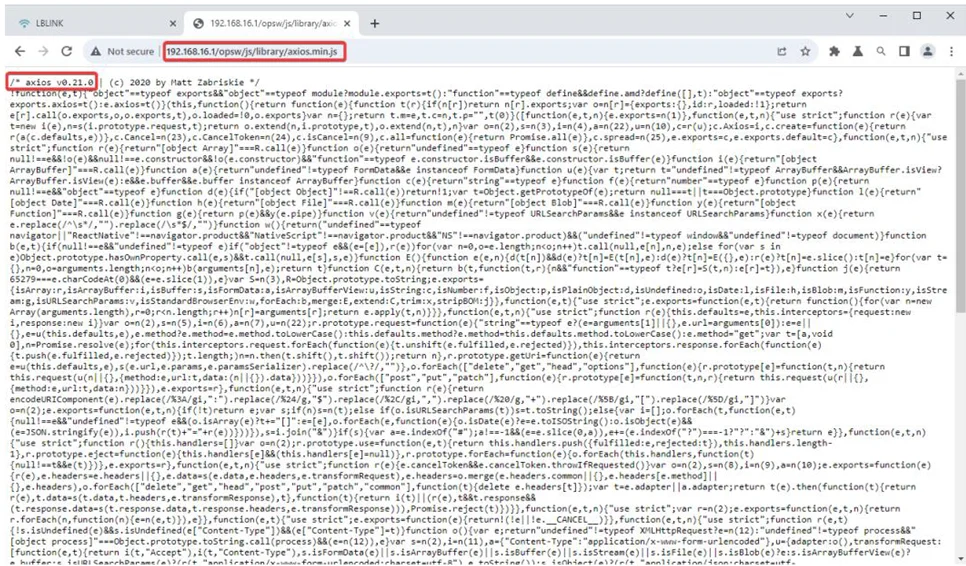
6. Missing HTTP-Only Flag on Cookies
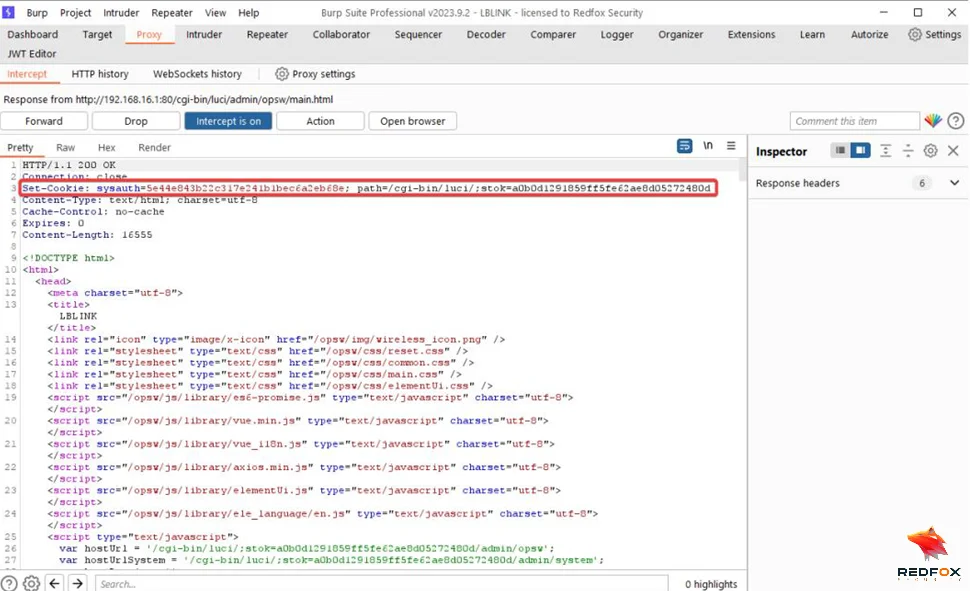
These vulnerabilities highlight several recurring issues in embedded device security:
Weak authentication mechanisms expose devices to brute-force and credential-stuffing attacks.
Poorly implemented access controls allow attackers to bypass restrictions entirely.
Failure to encrypt sensitive data such as credentials is an ongoing concern across IoT and networking devices.
Outdated dependencies remain a silent but dangerous attack vector.
Neglected secure development practices (e.g., missing cookie flags, lack of anti-clickjacking measures) leave users exposed to client-side threats.
Given how routers often sit at the perimeter of networks, these flaws could provide attackers with direct access to internal systems, potentially affecting an entire organization.
The vulnerabilities uncovered in the LB-Link BL-W1210M router represent significant threats, ranging from credential theft to full device takeover. Attackers could exploit these weaknesses to gain complete control of a network environment.
Immediate Action For Users:
Update to the latest available firmware.
Change default or weak passwords immediately.
Limit physical access to devices wherever possible.
Consider network segmentation to reduce exposure in case of compromise.
At Redfox Security, we specialize in uncovering these types of risks before attackers can exploit them. Our team can help assess vulnerabilities in your infrastructure and provide tailored remediation strategies.
Take action today—strengthen your defenses, secure your infrastructure, and protect your data. Explore our expert consulting services as well as our comprehensive security training programs to build in-house expertise and resilience against evolving threats.