
Want to intercept all HTTPS traffic from Android apps — even those that block user-installed certificates? This guide walks you through installing Burp Suite’s CA certificate as a system certificate on a rooted Android device or emulator. Ensure full traffic visibility and test even the most locked-down apps.
Intercept All HTTPS Traffic, System-Wide
Even apps that reject user-installed certificates will trust a system-installed Burp CA, allowing full interception.
Bypass network_security_config.xml Restrictions
Android 7.0+ requires apps to explicitly allow user CAs — but system certificates are trusted by default.
Export Burp suite Certificate (DER format)
1) In Burp Suite, navigate to the “Proxy” > “Proxy Settings”.
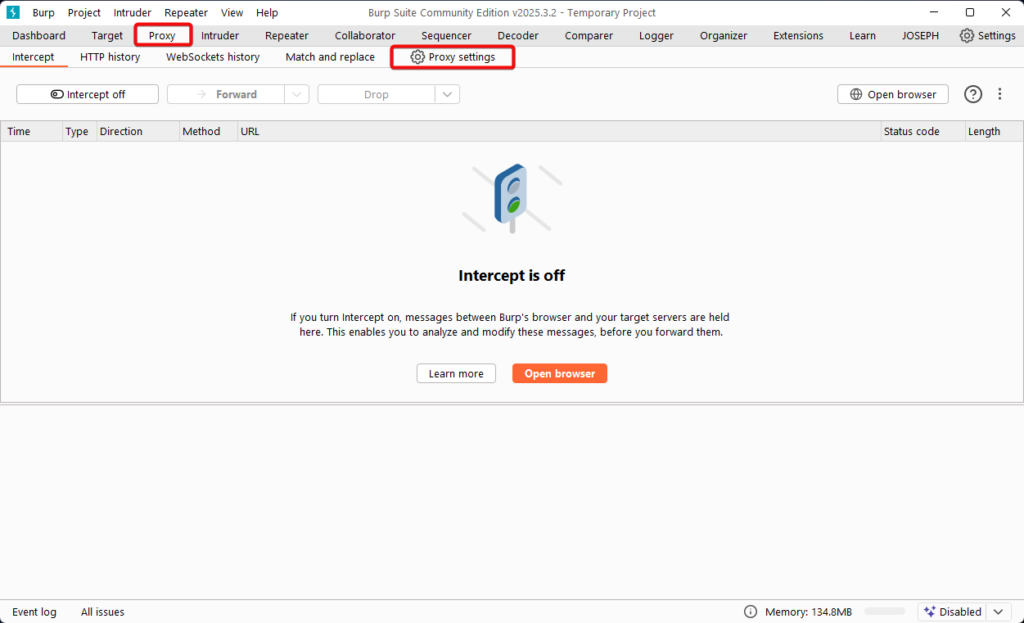
2) Select the “Import / export CA certificate” button.
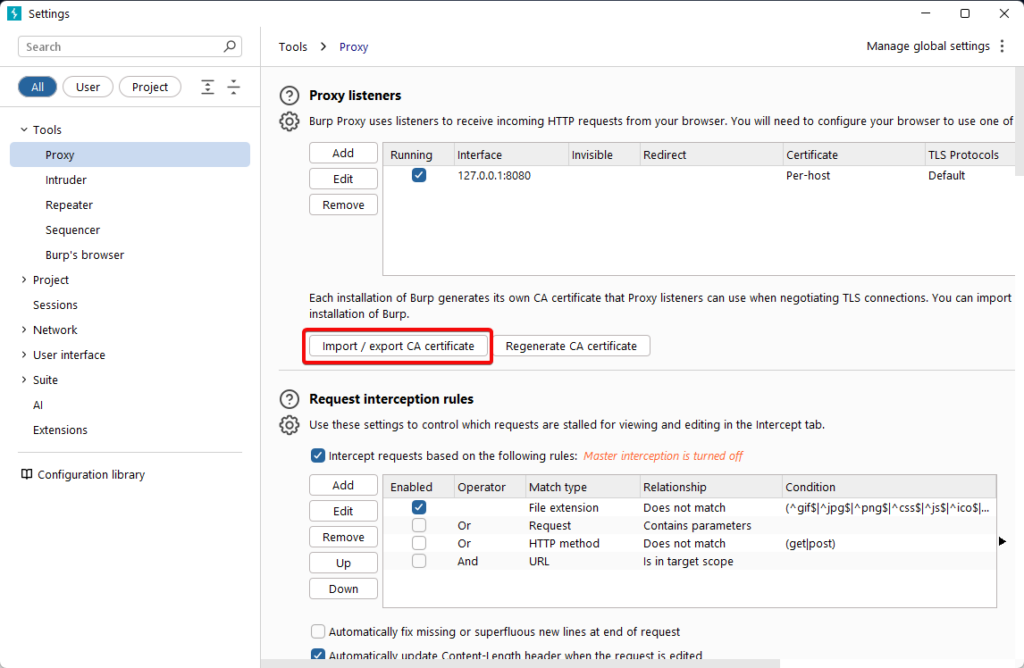
3) Choose “Certificate in DER format”, then click “Next”.
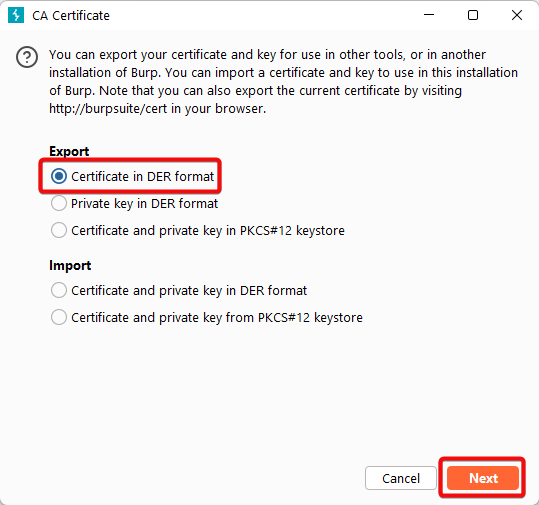
4. Click “Select file”, choose the location where you want to save the certificate, and name the file Burp.der.
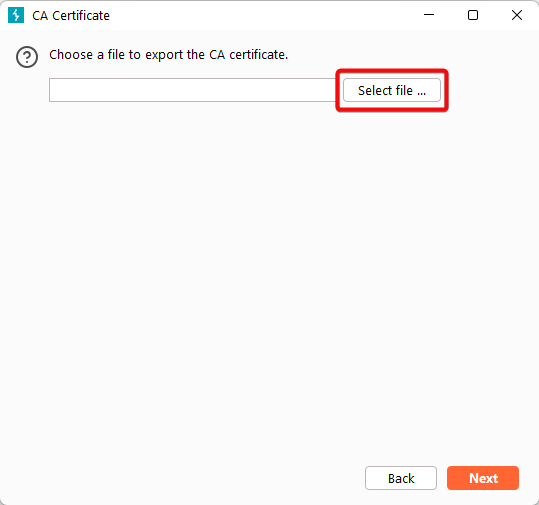
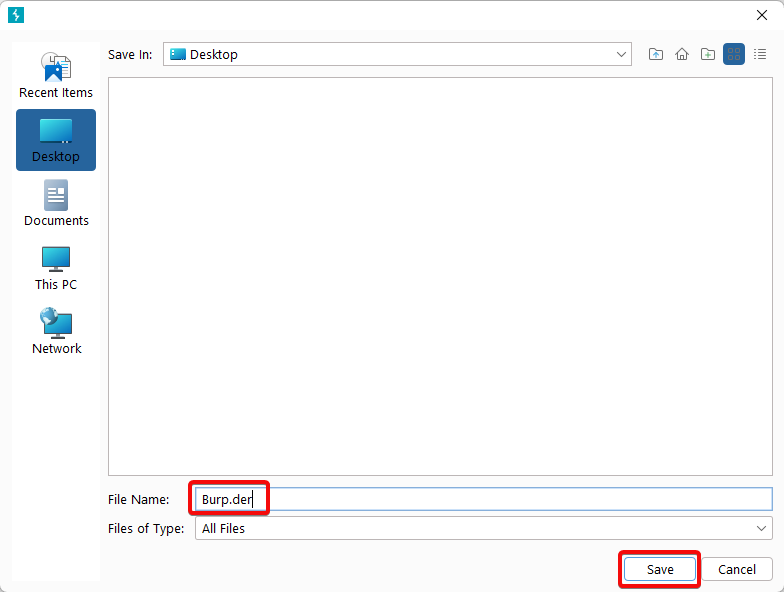
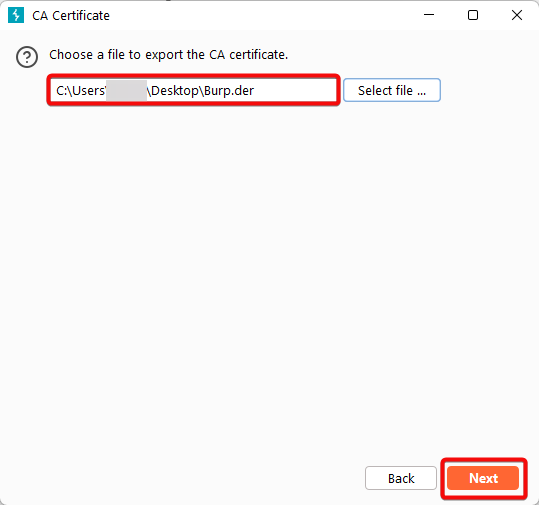
5. Click “Next” to complete the export process.
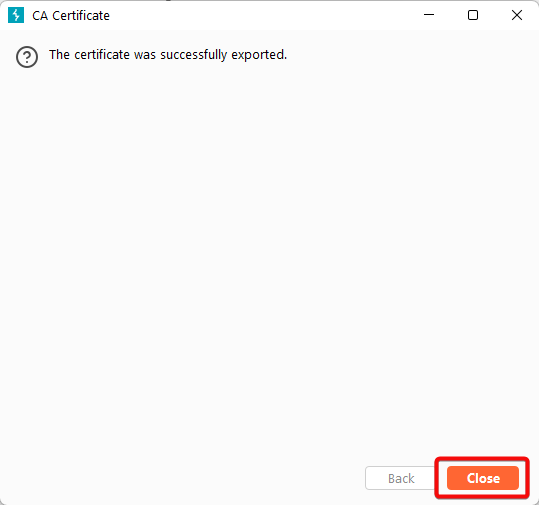
6. Navigate to the location where you saved the Burp.der file

1. Copy Burp.der file in kali linux.
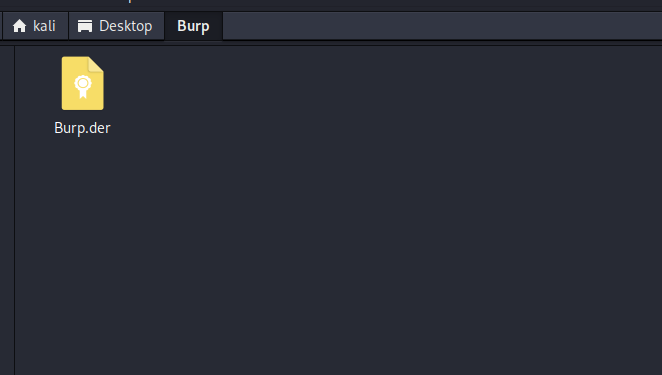
2. Open terminal and navigate to folder where you pasted (Burp.der) file and run command
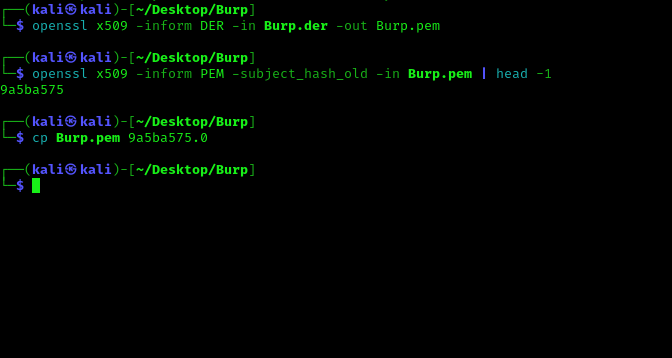
openssl x509 -inform DER -in Burp.der -out Burp.pem
openssl x509 -inform PEM -subject_hash_old -in Burp.pem | head -1
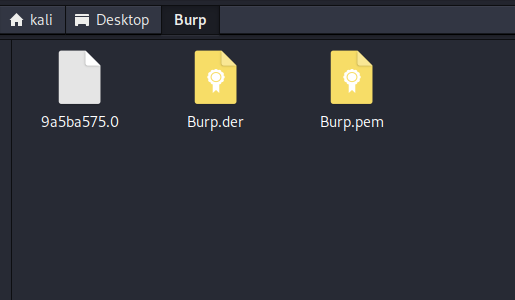
cp Burp.pem 9a5ba575.0
1. Connect to Emulator (I will be using Nox Emulator)
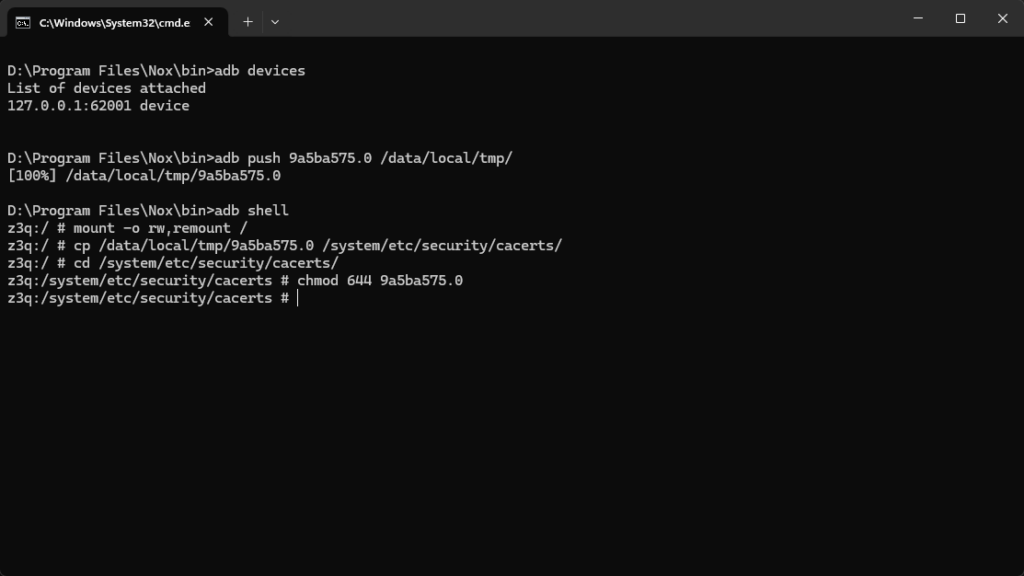
2. Open command prompt run command
adb devices
adb push 9a5ba575.0 /data/local/tmp
adb shell
mount -o rw,remount /
cp /data/local/tmp/9a5ba575.0 /system/etc/security/cacerts/
cd /system/etc/security/cacerts/
chmod 644 9a5ba575.0
3. Open (Nox emulator) Go to Settings > Encryption & Credentials >Trusted Credential > SYSTEM
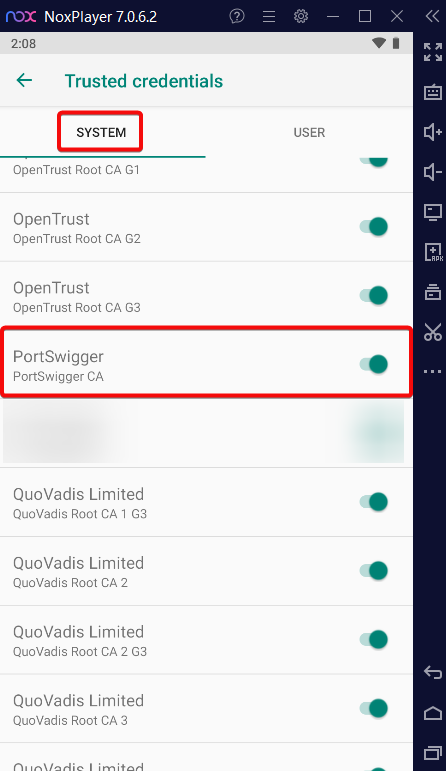
Installing Burp Suite’s CA certificate as a System Certificate instead of a User Certificate unlocks full control over HTTPS traffic interception on Android. Unlike user certificates — which are ignored by apps that enforce strict network_security_config or certificate pinning — system certificates are trusted by all apps by default, including those with enhanced security.