
Ensuring the security of networking devices is more critical than ever in today’s connected world. Routers, often overlooked, are the gateways to our homes and organizations, and vulnerabilities in them can expose sensitive information to malicious actors. Recently, a serious flaw was discovered in the Asus RT-N12+ B1 router (CVE‐2024‐28325) that highlights the importance of proactive security practices.
In this blog, we will explore the details of this vulnerability, the risks it poses, the timeline of disclosures and vendor responses, and the available mitigation strategies to help protect users.
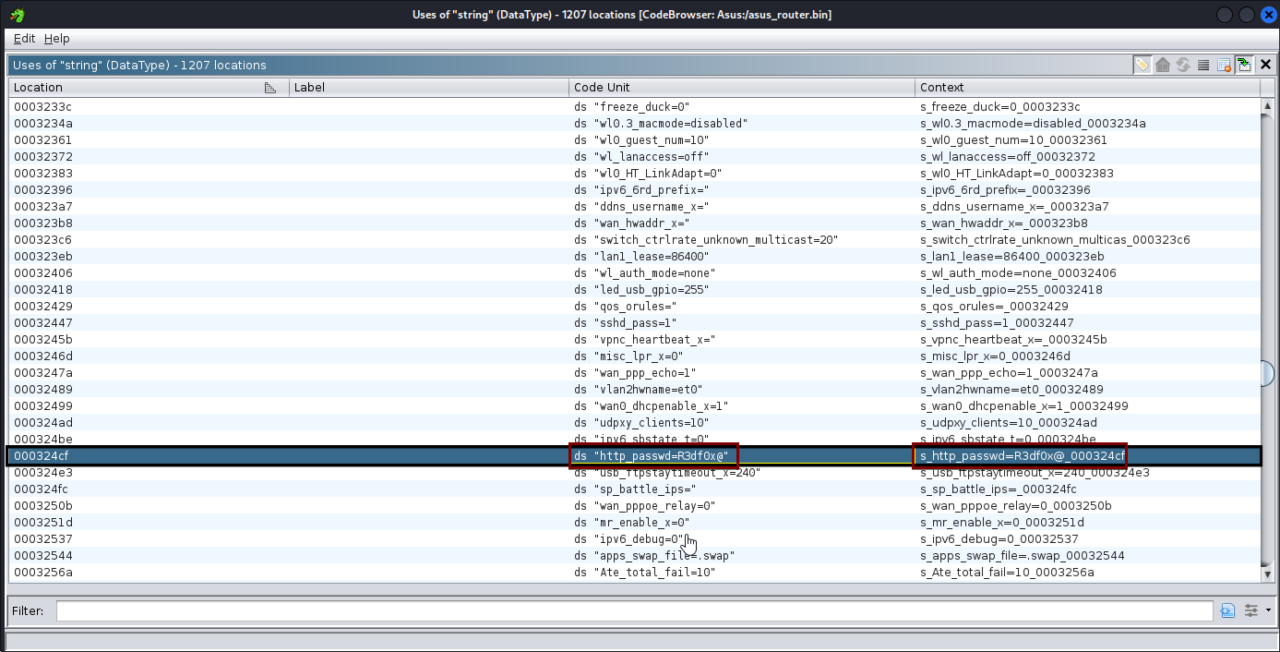
A critical vulnerability has been identified in the Asus RT-N12+ B1 router, specifically linked to how it handles sensitive credentials. The router stores user passwords in cleartext within its database. Since the credentials are not encrypted or hashed, they can be easily read and accessed by unauthorized individuals who gain access to the firmware or database.
This poor practice leaves users exposed to severe security risks, including unauthorized access, router manipulation, and potential data exposure. Given the seriousness of this flaw, immediate remediation is essential.
21/02/2024 – Initial Contact: Vulnerability report submitted to Asus.
28/02/2024 – Follow-up: First communication with Asus after no initial response.
05/03/2024 – Asus Acknowledgment: Vendor confirms receipt of the vulnerability report.
Asus has indicated that a beta version of the router’s firmware is now available for testing. These companies seek user feedback to evaluate if this beta version addresses any identified issues. The beta firmware can be accessed and reviewed via this link.
01/04/2024 – Second Follow-up & Acknowledgment: Ongoing communication to track remediation progress.
02/04/2024 – Third Follow-up: Continued outreach regarding updates.
12/04/2024 – Asus Response: Vendor highlights challenges due to firmware size and device end-of-life status.
Asus has indicated that upon examination, they’ve determined that the firmware size for this model is excessively large, and the product has reached the end of its life cycle, posing challenges for ongoing maintenance.
Additionally, they have provided a beta firmware version for the router firmware. They’ve requested feedback on whether the provided firmware effectively addresses the identified issues. You can access the beta firmware file through this link
The implications of storing credentials in plaintext extend beyond the router itself:
Unauthorized Access – Attackers can directly view login credentials and take control of the device.
Router Manipulation – With full access, malicious actors can reconfigure the router, redirect traffic, or disable security settings.
Data Exposure – Any connected devices or traffic routed through the compromised device may be at risk.
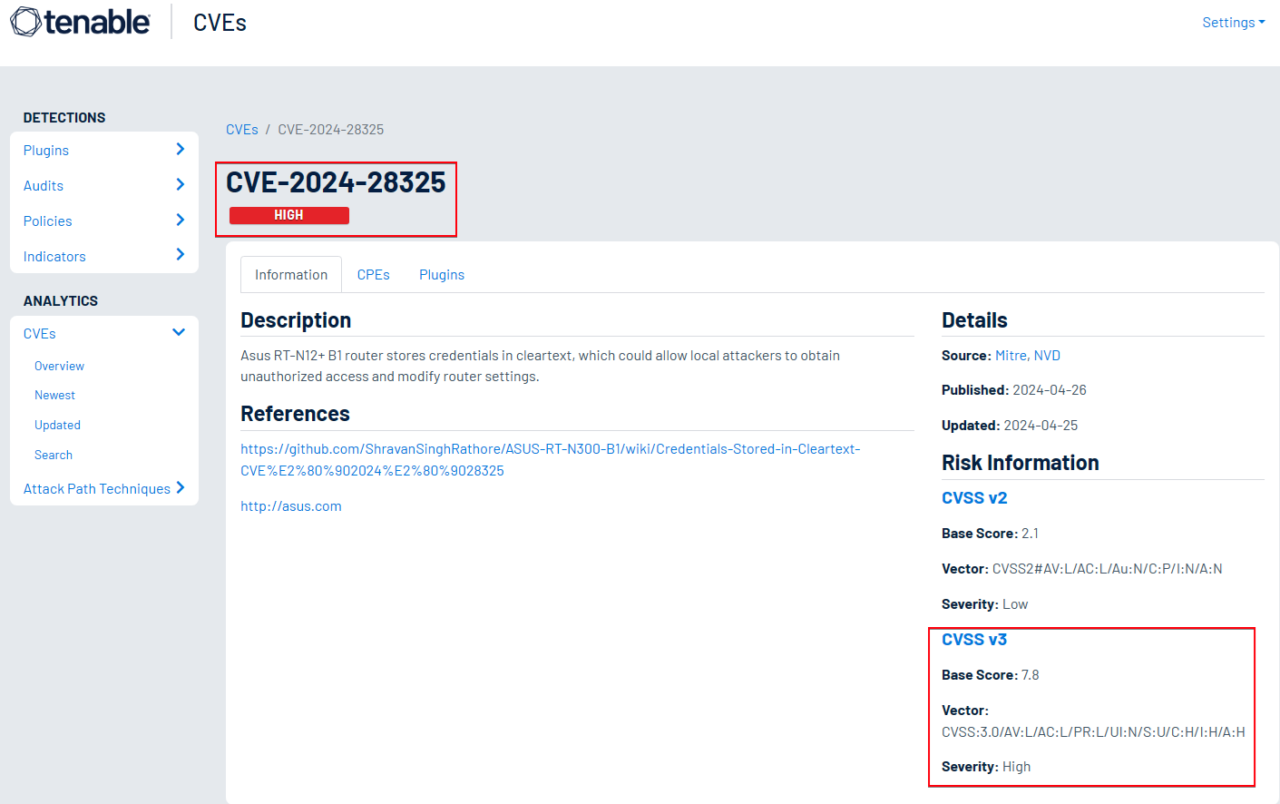
Access the router’s firmware or database.
Review stored credentials.
Observe that passwords are visible in cleartext and can be directly used to authenticate.
This confirms the severity of the flaw and underscores the risks of inadequate credential management.
To mitigate risks associated with this vulnerability:
Do Not Store Passwords in Plaintext – Credentials should always be protected using secure techniques such as hashing or encryption.
Upgrade Devices – Users should strongly consider replacing the Asus RT-N12+ B1 with a modern, actively supported router.
Test Beta Firmware – Users who cannot immediately upgrade may test the beta firmware provided by Asus, but caution is advised given its non-final status.
Implement Network Segmentation – Place legacy devices on isolated networks to minimize exposure.
Issue: Asus RT-N12+ B1 router stores credentials in plaintext.
Risk: Unauthorized access, router manipulation, and data exposure.
Status: Device is end-of-life; official updates discontinued.
Mitigation: Upgrade hardware, test Asus beta firmware, adopt secure credential management.
The Asus RT-N12+ B1 cleartext credentials vulnerability (CVE‐2024‐28325) is a reminder of the risks associated with outdated, unsupported hardware. Users should prioritize replacing or upgrading legacy networking devices to maintain strong security postures.
At Redfox Security, we specialize in helping organizations identify vulnerabilities like these and strengthen their defenses. If you’re looking to assess and enhance your security infrastructure, contact us today.
Join us on our journey of growth and development by signing up for our comprehensive courses.