Introduction to VLAN
Virtual LAN is a logical method of grouping Layer-2 switchports on a local switch into different broadcast domains. VLANs can help to segment a physical network switch to multiple virtual networks. VLANs can be set up by configuring network switches with a specific VLAN name and number. Valid VLAN numbers can range from 0-4095, but some numbers are reserved for special purposes or by specific switch vendors.
VLAN Trunking
In larger environments with multiple switches/VLANs, there may arise the need to group different network hosts on different VLANs even if they are not on the same physical switch. VLAN Trunking (IEEE 802.1q) helps to solve this issue. This protocol introduces VLAN tagging for ethernet frames, labelling it as belonging to a certain VLAN.
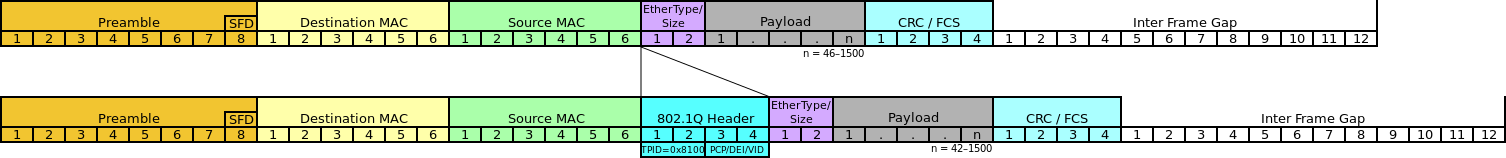
These tags are not present in regular ethernet frames coming out of network hosts. They are added to the regular frame by network switches on switchports which are configured to do so. Switchports support access mode and trunk mode configurations. A Frame coming to an access port on a switch should be a regular ethernet frame and if any tags are present, the frame will be discarded. Also, when an access port is transmitting a frame out into the wire, it will not add any tags. A switchport in trunk mode adds the necessary VLAN tags before transmitting the frame out into the wire.
The 802.1q Protocol specifies that one VLAN on a trunk shall not be tagged (aka Native VLAN). On some switches, VLAN 1 is configured to be the Native VLAN by default. On other switches, the Native VLAN is not enabled by default and has to be manually set up by the administrator.
VLAN Hopping
VLAN hopping is a type of network attack which allows frames from one VLAN to pass into another VLAN. This enables adversaries to send traffic to a VLAN, which their host should not be able to reach. Two main methods of VLAN hopping attacks are Switch spoofing and Double tagging.
Switch spoofing
Cisco DTP (Dynamic Trunking Protocol) switchports can be configured into 4 modes.
Access
An access port does not function as a trunk interface and allows only one VLAN. Whether or not the surrounding interface is a trunk interface, an interface in access mode becomes a nontrunk interface.
Trunk
The trunk mode enables the interface to be set in permanent trunking mode.
Dynamic Auto
This DTP mode causes the interface to wait passively for a negotiation message to make itself a trunk, at which point the switch will respond and negotiate whether or not to employ trunking.
Dynamic Desirable
This DTP mode allows a switchport to start trunking with another switchport by sending a negotiation message that allows the switchport to dynamically decide whether or not to start trunking.
If the switchport is configured in dynamic auto/dynamic desirable mode, then adversaries can trick a switch into creating a trunk with their host using DTP frames. This allows adversaries access to otherwise unreachable VLANs.
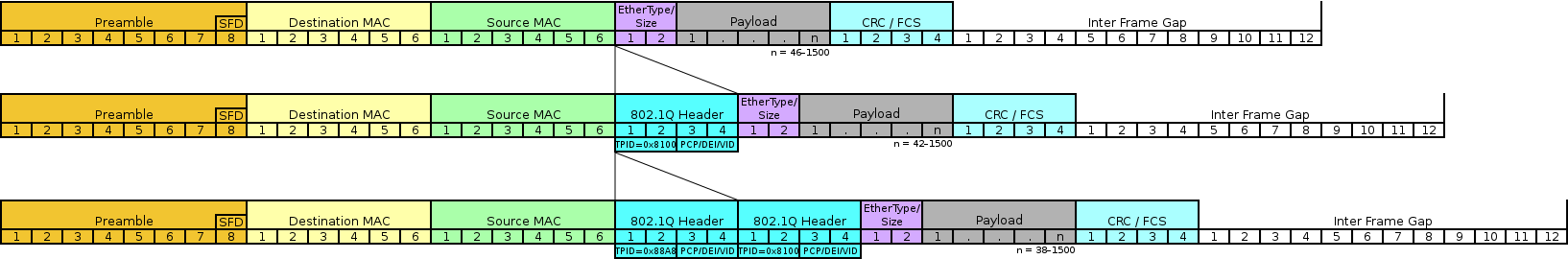
Double Tagging
If an adversary has access to a native VLAN, then he/she can send traffic from one switch to another by sending frames with two 802.1q tags. Because it is the native VLAN of a trunk interface, the frame is forwarded without the initial tag. The second tag is then visible to the frame’s encounter with the second switch. The frame is destined for a target host on a second switch, as indicated by the second VLAN tag. The packet is subsequently delivered to the target host as though it came from the target VLAN, successfully circumventing the network procedures that logically separate VLANs.
Mitigations
Switch spoofing: Switch spoofing can be prevented by configuring the switchports to not negotiate trunks dynamically i.e., by disabling DTP. Also, switchports that are not intended to be trunks should be manually configured as access ports.
Double Tagging: Hosts on native VLAN configured switches are a requirement for double tagging attacks. To prevent double tagging attacks, configure the native VLAN of all trunk ports to an unused VLAN ID with no hosts. Also avoid using VLAN 1 which is the default native VLAN to make the network more secure.
In this blog, we discussed about VLANs, trunks, VLAN hopping attacks and their mitigations. Adversaries also abuse VLAN hopping to gain access to segmented Industrial Control Systems and can cause irrevocable damages. Since VLANs are not inherently secure, special care has to be taken when configuring them.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”